A scenario involving a large-scale ransomware attack that does not require device infection no longer belongs solely to the realm of fiction. A study by SquareX warns that the browser may soon become the next battlefield for ransomware, capable of evading traditional security mechanisms. This emerging threat poses a significant risk to cloud services and corporate data—especially in an era dominated by SaaS applications and cloud-only storage solutions.
Historically, ransomware attacks necessitated direct access to a target device—whether a computer or smartphone. Today, however, conventional defenses may prove insufficient.
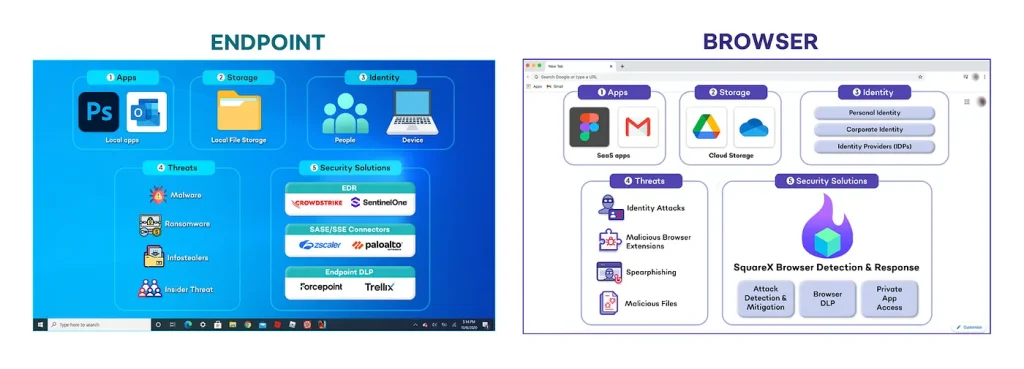
With the transition to cloud-based storage and web applications, a substantial portion of corporate operations has migrated to the browser. Cybercriminals have quickly adapted, crafting malicious tools that function entirely within the browser environment, bypassing the device’s file system altogether. According to SquareX, this affords attackers a lucrative advantage—high efficiency with minimal risk of detection.
Unlike traditional ransomware, browser-based variants employ fundamentally different tactics. They do not download files or initiate local processes, and thus escape the notice of antivirus software and security systems. Instead, they operate through OAuth permissions, malicious browser extensions, phishing schemes, or account synchronization—allowing them to surreptitiously seize control of victims’ cloud services.
SquareX’s report outlines three hypothetical attack vectors:
- In the first scenario, an attacker disguises a malicious application as legitimate, gains access to the victim’s Google Drive, copies and deletes sensitive files, then demands ransom in exchange for not publishing the stolen data.
- The second method involves consent phishing—phishing campaigns that exploit permission-based access. By infiltrating a victim’s email, the attacker identifies which SaaS platforms are in use. Then, using AI, they automatically reset passwords, hijack accounts, and exfiltrate stored data.
- The third scenario hinges on a vulnerability in browser synchronization. Through a compromised extension, an attacker silently authorizes their own profile, which syncs with the victim’s account. This grants access to all saved passwords and SaaS applications.
Unlike conventional malware, which leaves a trace on the file system, browser-based ransomware operates beyond the visibility of EDR, SASE, and other established security frameworks. Compounding the issue, most enterprise cybersecurity tools do not monitor OAuth grants, extension installations, or in-browser behavior. A lack of threat intelligence and standardized response protocols further exacerbates the risk.
Moreover, the browser-centric model enables broad horizontal spread: a single compromised user with shared file access can jeopardize the integrity of an entire corporate archive. Whereas traditional ransomware typically affects a single endpoint, browser-based compromises threaten all interconnected resources.
Experts caution that the components for such an attack already exist and have been employed in isolated incidents. One such case involved Cyberhaven, where attackers distributed a malicious update for a Chrome browser extension. While no full-scale campaign has been observed yet, researchers believe the first major browser-based ransomware attack is a matter not of possibility, but of time.


