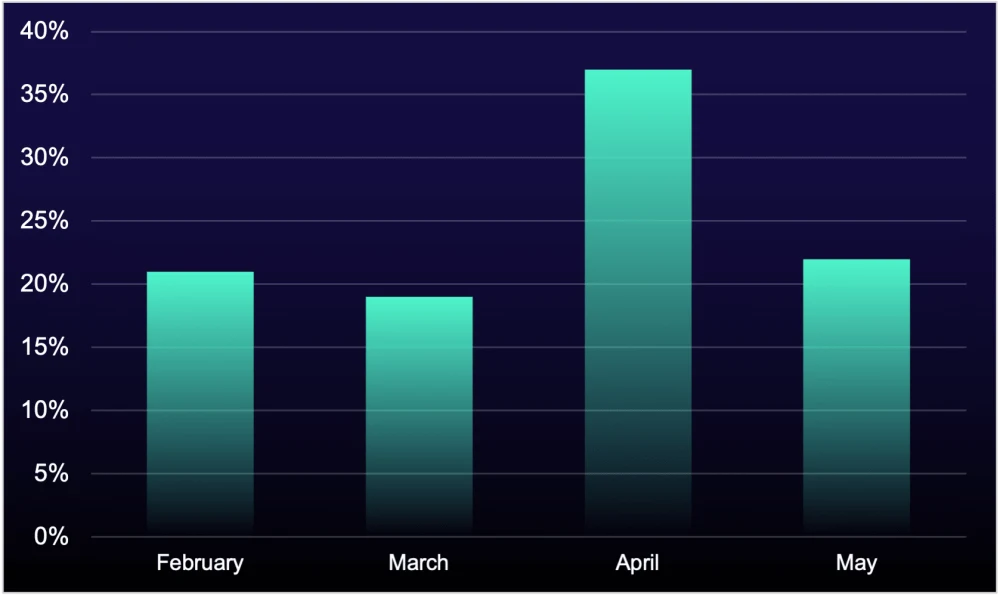
Volume of help-desk phishing events on Microsoft Teams targeting ReliaQuest customers in 2025
Despite the public collapse of the Black Basta syndicate following the leak of its internal chat logs in February 2025, its former operatives continue to deploy familiar attack techniques—methods they have not only preserved but actively refined. According to a report by ReliaQuest, traditional tactics such as mass email spam and phishing via Microsoft Teams have now been augmented with Python scripts and the covert transmission of malicious payloads through cloud platforms.
A pivotal innovation in recent campaigns is the use of cURL requests to download and execute malicious scripts directly on victims’ machines. These attacks have been observed targeting the financial, insurance, and construction sectors, with attackers masquerading as support personnel via compromised domains and forged accounts on “onmicrosoft[.]com” addresses. Between February and May 2025, nearly half of all phishing attempts via Teams originated from such domains, 42% of which involved already compromised infrastructure.
ReliaQuest notes that intruders often exploit the gained access to initiate remote sessions through tools like Quick Assist and AnyDesk. Once established, they deploy a malicious Python script that maintains persistent command-and-control communication with the infected host. In certain instances, victims are shown fake Windows login prompts designed to harvest credentials.
Amid continued activity by Black Basta’s former members, the escape of the group’s alleged leader, Oleg Nefyodov, from an Armenian courtroom caused considerable stir. Local media reported his arrest on June 21, 2024, following an Interpol request, with a mandated 72-hour detention pending a prosecutor’s motion for temporary custody. However, during the hearing, Nefyodov’s lawyer successfully requested a 15-minute recess, during which the defendant was permitted a “walk” and subsequently vanished.
Though Black Basta’s leak site has disappeared, its methodologies have been reborn. Evidence suggests that some ex-members may have migrated to the CACTUS group, as indicated by references in leaked chats to a $500–600K transfer to the collective. Still, CACTUS has not posted any new leaks since March 2025, raising suspicions that it may have either gone underground or ceased operations altogether.
A likely new refuge for these operatives could be BlackLock—a group allegedly aligned with a rising cartel called DragonForce. This alliance has been increasingly linked to major cyberattacks in recent months.
The attack infrastructure itself continues to evolve. Analysts have identified enhanced Java-based backdoors, previously associated with credential theft in Black Basta operations. These now utilize cloud services such as Google Drive and OneDrive to proxy command traffic, effectively evading conventional detection mechanisms. Notably, recent samples leave proxy configuration fields empty, signaling a deliberate pivot to cloud service provider (CSP) infrastructure.
New versions of the malware can transfer files, establish SOCKS5 proxies, extract browser-stored passwords, launch Java classes from remote URLs directly into memory, and even display spoofed login windows—rendering them formidable tools for network persistence and attack deployment.
Tactics pioneered by Black Basta alumni are now proliferating among other threat groups. For example, BlackSuit has adopted similar social engineering techniques, including phishing via Teams and leveraging Quick Assist—suggesting either tactical convergence or cross-group membership.
The report also references additional malware strains, such as the Anubis Python backdoor, a Java-based variant, and a Rust-written utility believed to function as a loader for an SSH client. Of particular note is the tunneling backdoor QDoor—previously linked to BlackSuit and recently spotted in 3AM-style attacks documented by Sophos.
In a broader context, other threat actors are mounting parallel offensives. Scattered Spider, for instance, is targeting managed service providers (MSPs) using Evilginx-powered phishing pages to bypass multi-factor authentication. Meanwhile, the Qilin group—also known as Agenda or Phantom Mantis—continues to exploit vulnerabilities in Fortinet FortiGate, and Play is aggressively abusing CVE-2024-57727 in SimpleHelp software to breach U.S.-based organizations.
Amid these developments, internal discord within the VanHelsing group led to a full leak of their source code, including TOR keys, admin panels, blog databases, and chat systems. Simultaneously, the Interlock group has begun distributing a new JavaScript backdoor, dubbed NodeSnake, which is specifically targeting educational and governmental institutions across the United Kingdom.
As emphasized by Quorum Cyber, the use of Remote Access Trojan (RAT) tools remains a cornerstone of modern threat operations. These tools enable adversaries to exert control over systems, monitor user activity, deploy additional payloads, and exfiltrate sensitive data—making them indispensable assets in the arsenal of today’s cybercriminals.


