Disney’s latest adaptation of Snow White, which garnered a dismal rating of 1.5 out of 10 on IMDb, has not only become the studio’s most catastrophic cinematic endeavor, but also an unexpected vector for cyberthreats. The film generated such feeble interest that it never even made it into the Disney+ streaming catalog. Cybercriminals seized this opportunity, disseminating malware disguised as a pirated version of the film.
According to researchers at Veriti, attackers embedded a seemingly innocuous torrent link within a post on the blog platform TeamEsteem, a site nominally associated with an American nonprofit working with schools and families.
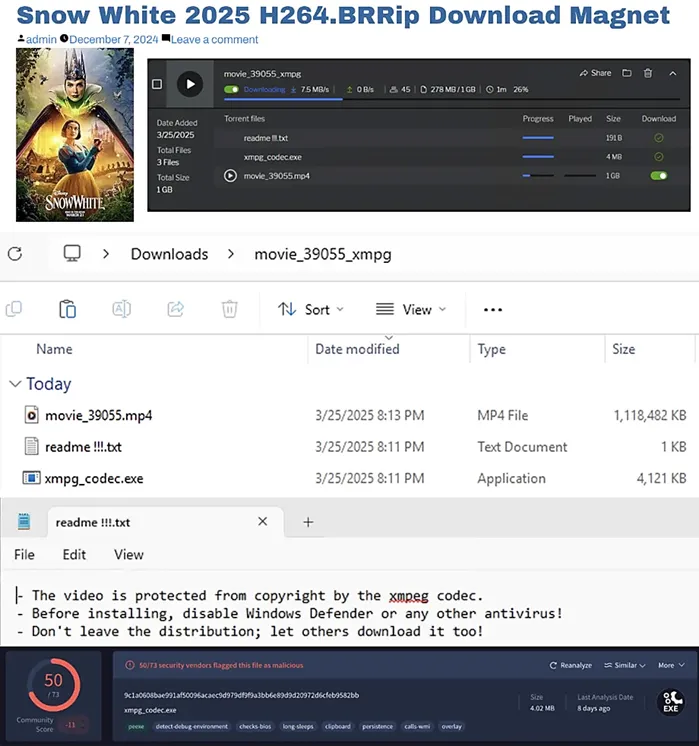
At first glance, the link appeared to lead to a typical torrent download. However, the archived package included more than just a video file — bundled alongside it were a README text file and a suspicious executable named xmph_codec.exe. The instructions claimed that the “codec” was required to play the film — a ruse reminiscent of early internet piracy schemes that continue to ensnare less vigilant users.
Upon execution, the malicious file initiates a sequence of harmful actions. It first disables Windows security measures, including the built-in antivirus and threat prevention systems. Next, it installs additional malware and launches the TOR browser to establish communication with a remote command-and-control server hosted on the dark web via a .onion address.
Researchers noted a worrying level of distribution activity: at the time of discovery, the file was being seeded by 45 peers — some likely compromised machines unknowingly propagating the malware. This peer-to-peer architecture accelerates the campaign’s spread among unsuspecting users.
What’s particularly alarming is that the malicious link was hosted on TeamEsteemMethod[.]com, a site with no prior association to such campaigns. Veriti posits that the breach occurred either through exploitation of CVE-2023-40680 — a vulnerability in outdated versions of the popular Yoast SEO plugin for WordPress — or via stolen administrator credentials.
The site was strategically used to lend credibility to the operation, increasing the likelihood that visitors would trust and download the malware. The attackers capitalized on the site’s perceived authority — rooted in its educational mission — to add a façade of legitimacy to their trap.
Disguising malware as newly released films is hardly unprecedented. Similar tactics were employed during the debuts of John Wick 3, Contagion, Black Widow, Joker, Ford v Ferrari, and Pirates of the Caribbean. Cybercriminals rely on high demand coupled with limited legal access to ensnare victims.
To avoid falling prey to such schemes, experts urge users to steer clear of pirated content, keep antivirus software up to date, and treat unexpected links from seemingly trustworthy sources with heightened suspicion. The pursuit of a “free movie” may ultimately come at a far greater cost.


