Malicious software continues to disguise itself as popular artificial intelligence tools—fake installers for OpenAI ChatGPT and InVideo AI are now being used to disseminate a range of threats, including the ransomware strains CyberLock and Lucky_Gh0$t, as well as a destructive malware variant known as Numero.
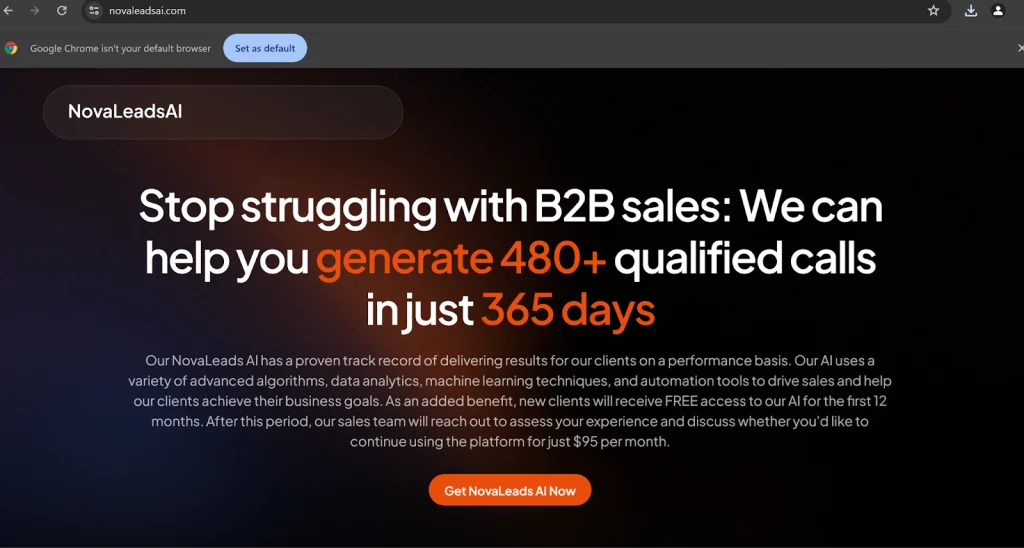
According to researchers at Cisco Talos, these counterfeit installers are being deployed to target users in B2B sales and digital marketing sectors. Among the fraudulent domains identified is novaleadsai[.]com, a spoof of the NovaLeads lead monetization platform. It is believed that the site’s visibility is artificially enhanced through SEO poisoning techniques designed to manipulate search engine rankings.
Victims are lured with the promise of free access to what appears to be a legitimate tool for one year, followed by a $95 monthly subscription. Instead of the expected software, they are prompted to download a ZIP archive containing the executable NovaLeadsAI.exe, which was compiled on the same day the domain appeared—February 2, 2025. Running the file triggers the installation of CyberLock, a PowerShell-based ransomware.
This ransomware is capable of escalating its privileges to administrator level, after which it encrypts files on drives C:, D:, and E: with specific file extensions. It concludes the attack by leaving a ransom note demanding $50,000 in Monero, claiming the funds will be donated to women and children in Palestine, Ukraine, Africa, Asia, and other regions where, according to the attackers, “injustice is a daily reality.” In the final phase, the malware executes Windows’ built-in cipher.exe tool with the /w flag, erasing free space on the disk to hinder data recovery.
In another case, the Lucky_Gh0$t ransomware—a variant of the sixth iteration of Chaos, also known as Yashma—was distributed through a fake premium installer of ChatGPT. The deployment was carried out via a self-extracting SFX archive containing an executable named dwn.exe, mimicking the legitimate system process dwm.exe. The archive also included genuine open-source Microsoft utilities sourced from GitHub.
Upon execution, a script extracted and launched the ransomware, which encrypted files smaller than 1.2 GB and deleted both shadow volume copies and backups prior to commencing the encryption process. Victims received a ransom note containing a unique ID and instructions to communicate via the encrypted messaging app Session to obtain a decryption tool.
Lastly, an attack involving a counterfeit InVideo AI installer was discovered. It functioned as a dropper carrying three components—a BAT file, a VBScript, and an executable named Numero. Once executed, the script ran in an infinite loop: launching the malicious process, pausing for 60 seconds, terminating it, and then relaunching it—ensuring the malware remained persistently active on the machine.
Numero itself, written in C++ and compiled on January 24, 2025, is a 32-bit Windows executable. It scans running processes for analysis and debugging tools before executing its payload, which effectively destroys the graphical interface of Windows. It does so by corrupting window headers, buttons, and desktop elements—replacing them with an endless string of digits, “1234567890,” rendering the system unusable.
Thus, the burgeoning interest in AI tools has become fertile ground for cyberattacks, where threat actors exploit user trust in reputable brands and emerging technologies—transforming innovation into a conduit for danger.


