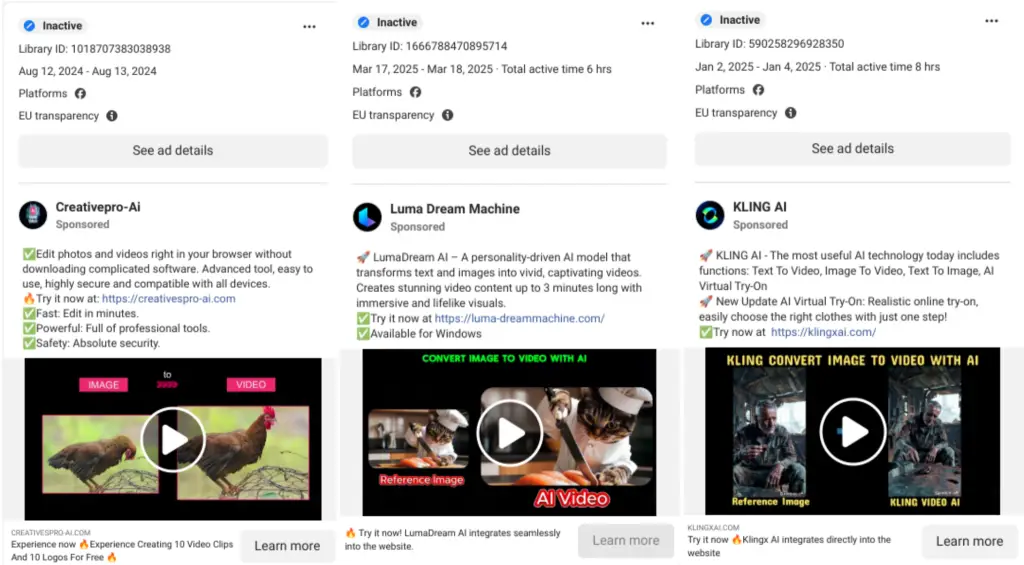
Since late 2024, the Mandiant Threat Defense team has been monitoring a large-scale campaign orchestrated by the group UNC6032, which has weaponized the global fascination with generative AI as a lure for distributing malware. The primary tactic involves counterfeit websites impersonating popular text-to-video generation tools such as Luma AI, Canva Dream Lab, and Kling AI. Victims are redirected to these cloned sites via thousands of fraudulent advertisements on Facebook and LinkedIn, where they are enticed into downloading infected archives.
According to Mandiant, the malicious campaign utilizes more than 30 domains, with fake advertisements reaching over 2.3 million users across EU countries alone. These ads originate from both fabricated profiles and hijacked accounts, with domains frequently rotated to evade detection and takedown. While LinkedIn played a smaller role volume-wise, it was the platform of choice for targeting audiences in the United States, Europe, and Australia.
The downloaded archive conceals a file with a deceptive double extension, .mp4.exe, camouflaged using invisible Braille Unicode characters within the filename. Its icon mimics that of a standard video file, making the malicious executable appear innocuous.
The primary dropper, dubbed STARKVEIL, is written in Rust. Upon execution, it unpacks and installs various components into internal directories, including the backdoors XWORM and FROSTRIFT, as well as the loader GRIMPULL. STARKVEIL then launches a Python interpreter with encrypted code that eventually triggers the execution of legitimate binaries accompanied by malicious DLLs. These libraries serve as injectors, embedding payloads into native Windows processes.
GRIMPULL is a .NET-based loader equipped with sandbox and virtual machine detection mechanisms. It utilizes the Tor network to establish contact with its command-and-control server and to retrieve additional modules. Its configuration is encrypted and stored as Base64. If Tor is not present on the system, it can autonomously install it, encrypting traffic using TripleDES.
XWORM functions as a comprehensive backdoor, offering capabilities such as keylogging, screenshot capture, remote command execution, and USB-based propagation. It communicates with its C2 server over TCP, transmits exfiltrated data via Telegram, and accepts commands for tasks such as system shutdown, reboot, launching a command prompt, and more. Additional plugins can be downloaded and executed on demand.
FROSTRIFT, in contrast, focuses on data exfiltration. It collects detailed system information, checks for the presence of 48 widely used browser extensions—including crypto wallets, password managers, and 2FA tools—and analyzes installed cryptocurrency applications. The backdoor uses GZIP-compressed protobuf messages over SSL, stores its modules in the Windows registry, and loads them into memory upon command. It can also ensure persistence via registry-based autostart mechanisms.
All three backdoors rely on DLL sideloading through trusted Windows applications, significantly complicating detection efforts. Each module employs distinct obfuscation techniques and resilient communication protocols.
Mandiant has observed that UNC6032’s attacks have impacted victims across various countries and industries. Stolen data—including login credentials, cookies, payment card details, and Facebook profiles—is funneled through Telegram. Google’s Threat Intelligence Group has linked UNC6032 to Vietnam. Major platforms such as Meta and LinkedIn are actively working to combat the campaign, taking down malicious ads and blocking malicious domains, though the group’s activity remains persistent.
These counterfeit AI services have become universal traps—no longer targeting designers alone, but luring any user intrigued by artificial intelligence into downloading compromised files. Similar incidents have already been recorded in Europe and Asia. Heightened vigilance and domain authenticity verification have become critical safeguards in the age of deceptive AI tools.


