Artificial intelligence continues to reshape the labor market: according to a survey by the World Economic Forum...
Phan Kenny
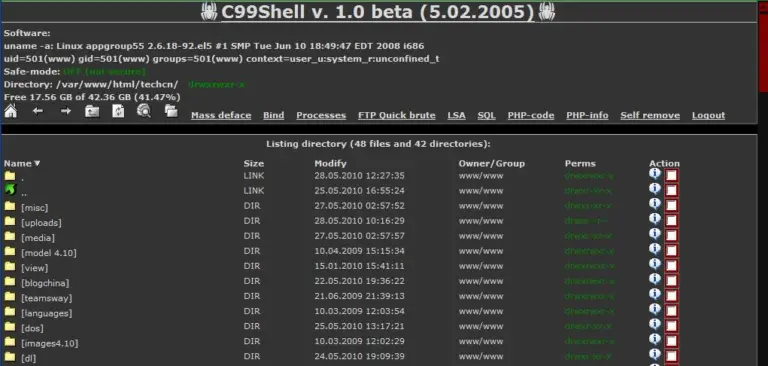
More than 4,000 unique web shells are exploiting expired domains and abandoned infrastructure, many of which are...
Motorola’s automatic license plate recognition (ALPR) cameras were found connected to an unsecured server, enabling unrestricted access...
A pilot program by the Pentagon has identified over 800 potential vulnerabilities and biases in the use...
On January 8, 2025, a significant theft of funds from the Orange Finance platform came to light....
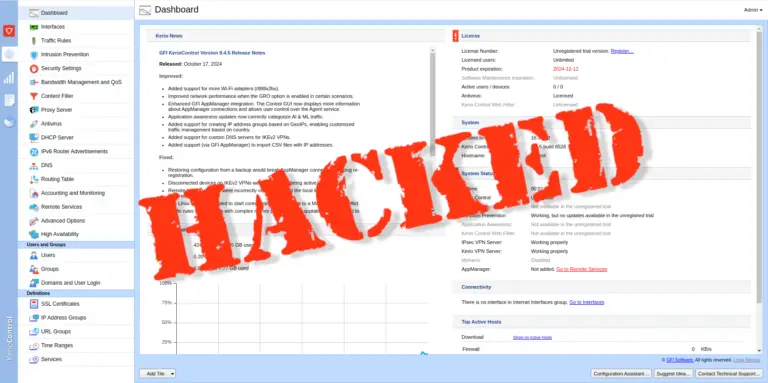
Hackers are actively exploiting CVE-2024-52875, a vulnerability discovered in GFI KerioControl—a firewall solution designed for small and...
Ivanti has announced the active exploitation of a critical vulnerability, CVE-2025-0282 (CVSS 9.0), affecting Connect Secure (up...
Fraudsters have devised an intricate social engineering scheme targeting bank clients in Middle Eastern countries. Masquerading as...
The White House has announced the launch of the U.S. Cyber Trust Mark initiative, a program aimed...
The Chairwoman of the Federal Communications Commission (FCC), Jessica Rosenworcel, has urged her colleagues to swiftly establish...
The National Police Agency of Japan has attributed over 200 cyberattacks in the past five years to...
Fraudsters are increasingly exploiting legitimate Apple and Google services to forge notifications and deceive users. These attacks,...