TOUGHPROGRESS infection chain (Google TAG)
In late October 2024, analysts from Google’s Threat Intelligence Group uncovered a new targeted campaign in which threat actors leveraged a compromised government website to disseminate a malicious payload dubbed TOUGHPROGRESS. The defining characteristic of this operation was its innovative use of Google Calendar as a command-and-control (C2) channel, enabling the attackers to mask malicious traffic amidst legitimate network activity.
The campaign has been attributed to the Chinese state-sponsored threat group APT41, also known as HOODOO—a globally active actor previously implicated in intrusions against logistics, automotive, IT, and media sectors. In this latest operation, APT41 distributed phishing emails containing links to a ZIP archive hosted on the compromised government domain. The archive included a deceptive LNK shortcut disguised as a PDF file and a folder containing images of insects. However, two of these files—6.jpg and 7.jpg—were in fact a malicious DLL and an encrypted payload, respectively.
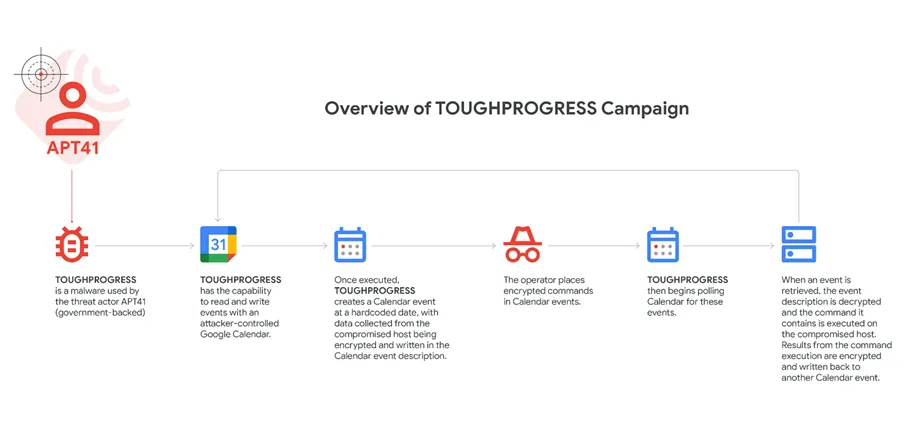
The infection chain unfolded across three stages: the PLUSDROP module first loaded the next-stage malware into memory; PLUSINJECT then injected malicious code into the legitimate process svchost.exe; finally, TOUGHPROGRESS carried out its operations on the infected system and established communication with the C2 server via calendar events. TOUGHPROGRESS exhibits a high degree of technical sophistication, utilizing encryption, obfuscation, convoluted arithmetic logic, and even 64-bit register overflows to obscure function calls.
On the Google Calendar side, the malware created zero-duration events that encoded stolen information from the victim’s device. Commands were embedded in other pre-scheduled events, which were decrypted and executed on the compromised host. Responses were subsequently encrypted and embedded into new calendar events. The communication protocol employed LZNT1 compression, dual XOR key encryption, and a complex custom header structure.
In collaboration with Mandiant, Google researchers developed unique signatures that enabled the detection and dismantling of APT41’s infrastructure, including malicious Google Workspace projects and calendar instances. Safe Browsing protections were updated, and all domains and URLs involved in the campaign were blacklisted, including subdomains hosted on Cloudflare Workers, InfinityFree, TryCloudflare, and numerous link shorteners. These measures successfully halted the spread of TOUGHPROGRESS and helped prevent further infections.
Google also notified affected organizations and shared detailed network telemetry and indicators of compromise. APT41 has previously employed similar tactics, exploiting cloud services to conceal the control mechanisms of other malware strains such as VOLDEMORT and DUSTTRAP, with prior abuse observed through platforms like Google Sheets and Google Drive.
Despite the takedown, APT41 continues to exploit free hosting services to deliver malicious loaders and capitalize on the implicit trust placed in widely-used cloud platforms. This underscores the urgent need for holistic defense strategies, including robust cloud traffic analysis and early detection of anomalous behavior within enterprise environments.


