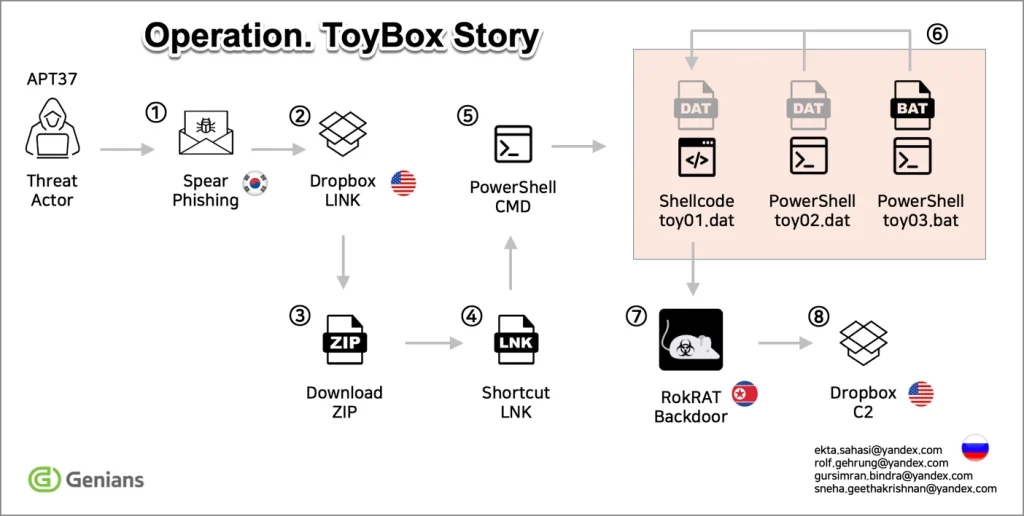
In March 2025, cybersecurity specialists from South Korea’s Genians Security Center uncovered a new operation orchestrated by the North Korean hacking group APT37. The campaign, dubbed ToyBox Story, revealed itself as a meticulously crafted spear-phishing operation targeting activists engaged with North Korean affairs. To lure victims, the attackers leveraged the theme of a real-world event titled Trump Era 2.0: Prospects and South Korea’s Response.
The phishing emails were disguised as formal invitations to academic forums and arrived with ZIP file attachments containing LNK shortcut files. These shortcuts triggered PowerShell commands that initiated a malware delivery chain. The campaign made extensive use of cloud storage services — including Dropbox, pCloud, and Yandex — which served as command-and-control (C2) servers. This tactic falls under the LoTS (Living off Trusted Sites) approach, a variant of Living off the Land (LotL) techniques where adversaries cloak their activity within legitimate traffic.
One example involved an email allegedly from a South Korean expert concerning North Korean soldiers reportedly sent to Russia. The attached ZIP archive contained an LNK file that executed a sequence of actions: displaying a decoy HWP document, generating a BAT file, and progressively decrypting malicious payloads. The operation employed advanced evasion tactics — such as obscuring file extensions and executing code directly in memory without writing to disk — hallmarks of sophisticated fileless attacks.
In both recorded incidents, the ultimate goal was the deployment of RoKRAT — a spyware toolset frequently used by APT37. This malware collects system information, captures screenshots, receives commands from operators, and can execute additional payloads downloaded from the C2 infrastructure. Device data and screenshots are packaged, encrypted, and transmitted to the attackers’ servers. The encryption strategy incorporated XOR, AES-CBC, and RSA, significantly complicating efforts to intercept or analyze the data.
RoKRAT communicated with the APIs of popular cloud platforms using access tokens tied to specific email addresses. Investigators also discovered older Gmail addresses linked to previous APT37 campaigns. Some of these matched usernames found on LinkedIn, though the exact nature of these connections remains undetermined.
A comparative analysis of RoKRAT’s code against earlier incidents revealed a high degree of continuity. The same PowerShell-based delivery method, encryption logic, and command structures were employed, indicating a conservative strategy. Rather than overhauling its toolkit, APT37 has focused on adapting it to new delivery vectors while evading conventional antivirus detection.
Operation ToyBox Story underscores the persistent and dangerous evolution of APT37. The group continues to adapt to shifting environments, increasingly leveraging legitimate platforms for malware delivery and control, all while preserving the core architecture of its tools. This strategy demands constant endpoint behavior monitoring and advanced analytics from organizations to ensure timely and effective incident response.


