Image: Cyfirma
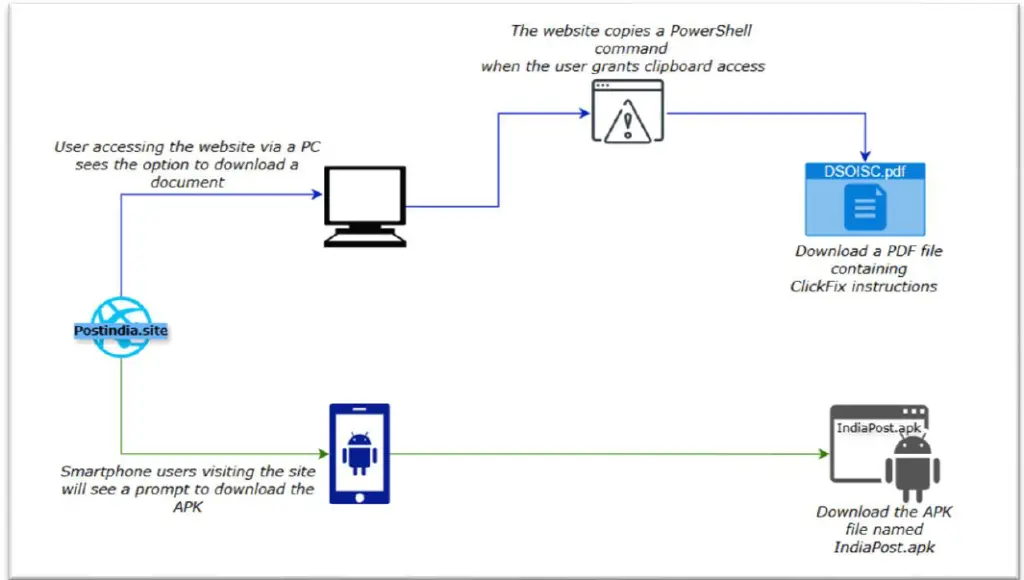
The Pakistan-linked threat actor APT36 has launched a sophisticated malware campaign by masquerading as the official website of India’s postal service. The counterfeit site, hosted at “postindia[.]site,” targets both Windows and Android users through distinct infection mechanisms: a malicious PDF document for desktop users and a counterfeit mobile application for Android devices.
When accessed via a desktop browser, the site prompts users to download what appears to be an official document. However, embedded within it is a deceptive instruction employing the “ClickFix” technique—victims are urged to press Win + R and input a PowerShell command. Once executed, the system connects to an external server to retrieve the next stage of the malware. Although the command-and-control server is currently offline, the malicious file continues to circulate across various platforms.
Metadata from the PDF document reveals an author identified as “PMYLS,” which may allude to Pakistan’s youth laptop distribution initiative. The spoofed domain name, closely mimicking India Post, was registered in November 2024—one month after the document was created—highlighting the deliberate orchestration of this campaign.
On mobile devices, the infection vector takes a different form. Users are prompted to install a fraudulent “India Post” application for added “convenience.” In reality, the app is a malicious tool endowed with extensive permissions. It harvests sensitive data, including contacts, location, and external storage contents. To evade detection, the app replaces its icon with that of “Google Accounts,” complicating user efforts to identify and remove it.
Particular emphasis was placed on persistence: the malware launches automatically after reboot, bypasses power-saving restrictions, and forcefully enables necessary permissions, even when users initially deny them.
CYFIRMA researchers, who examined the operation, attribute the campaign to APT36—also known as Transparent Tribe—with moderate confidence. The group is notorious for targeting Indian citizens and frequently employs a combination of social engineering and technical exploits.
The dual-pronged attack on both desktop and mobile platforms reflects an increasingly multifaceted strategy among APT groups. Disguising malware as a government-branded app is especially alarming, given the inherent trust users place in official institutions.
While the campaign has yet to reach a broad scale, its execution and choice of target suggest it may be a precursor to more expansive operations. Users are strongly advised to exercise caution when downloading files or applications from unfamiliar sources, even if they visually mimic trusted domains.


