Map of operation RoundPress victims in 2024 | Image: ESET
Since 2023, the hacker collective APT28 has been conducting a sweeping cyber-espionage operation known as RoundPress, aimed at exfiltrating email communications from government bodies and critical infrastructure entities across the globe. The campaign remains active to this day, continually evolving to exploit newly discovered vulnerabilities and infiltration techniques.
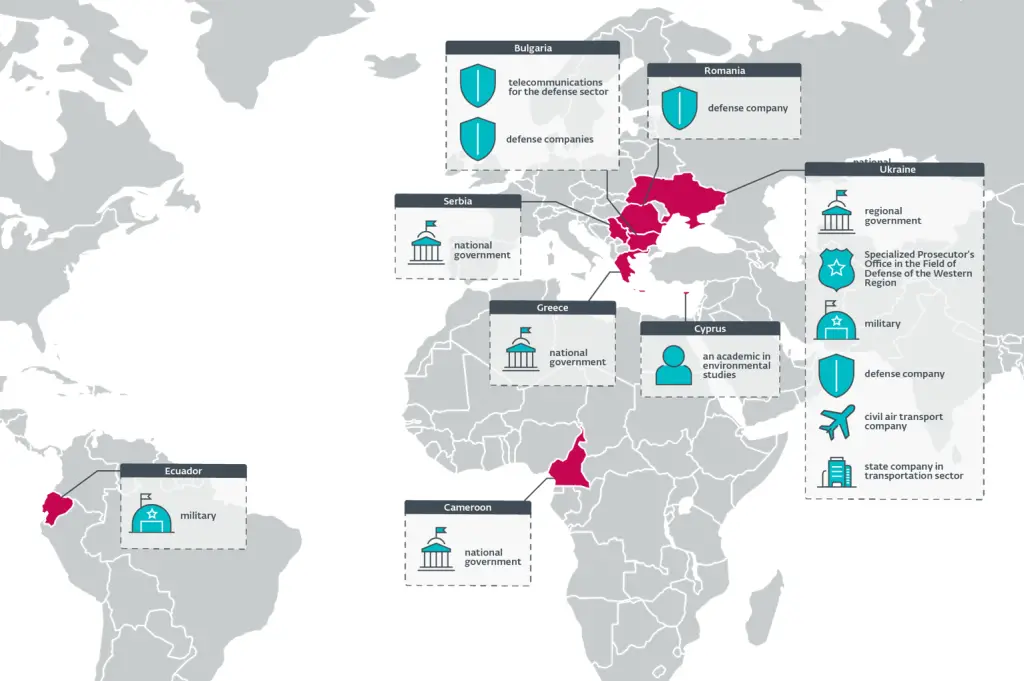
The operation employs a blend of both long-known and newly unearthed vulnerabilities in widely used webmail platforms, including Roundcube, Horde, MDaemon, and Zimbra. According to ESET, targeted entities include government institutions in Greece, Ukraine, Serbia, and Cameroon; military units in Ukraine and Ecuador; defense contractors in Bulgaria, Ukraine, and Romania; as well as critical infrastructure in Bulgaria and Ukraine.
The attack typically begins with a meticulously crafted phishing email, designed to mirror current news or political developments to establish credibility. Embedded within the HTML body of these messages is a malicious JavaScript payload that exploits cross-site scripting (XSS) flaws in the webmail interface. Merely opening the email in a browser is sufficient for infection—no clicks or downloads are required.
Digital paranoia is the new common sense.
The malicious code is never saved locally; it executes only upon viewing the message. The script injects invisible input fields to deceive the browser or password manager into auto-filling login credentials. In addition, it scrapes the page for sensitive information, including correspondence, contact lists, user settings, login history, and even two-factor authentication codes. All harvested data is then transmitted to preconfigured command-and-control servers.
The RoundPress campaign has leveraged the following vulnerabilities:
- Roundcube – CVE-2020-35730 (CVSS 6.1): A stored XSS flaw that allowed JavaScript to be injected into the email body. Actively exploited in 2023.
- Roundcube – CVE-2023-43770 (CVSS 6.1): A hyperlink-handling vulnerability that saw widespread use in early 2024.
- MDaemon – CVE-2024-11182 (CVSS 5.3): A zero-day flaw in the HTML parser exploited in the latter half of 2024, enabling bypass of 2FA and access via App Passwords.
- Horde – Undisclosed XSS: An attempt to exploit a legacy XSS issue via the
<img onerror>handler, though newer versions of the software effectively mitigated the threat. - Zimbra – CVE-2024-27443 (CVSS 6.1): A vulnerability in the calendar subsystem, allowing the injection of a stealthy script through the
X-Zimbra-Calendar-Intended-Forheader.
Each script was meticulously tailored to the architecture and quirks of its target mail server, underscoring the attackers’ technical sophistication. While no new RoundPress activity has been detected thus far in 2025, the tactics employed are easily adaptable to emerging XSS vulnerabilities that frequently surface in mainstream webmail systems.
This campaign serves as a stark reminder of how vulnerable even legitimate webmail interfaces can be when user interaction is minimal. A single email, once opened, can compromise an entire security infrastructure if adversaries are leveraging such refined attack vectors.


