Hackers have begun actively distributing a new iteration of the Amatera Stealer—a reimagined and fortified clone of the notorious ACR Stealer, once a staple of underground cybercriminal marketplaces. First identified in early 2025, this malware represents a significant leap forward in the evolution of information-stealing trojans, blending time-tested techniques with sophisticated obfuscation and evasion strategies.
According to Proofpoint, Amatera Stealer operates under a Malware-as-a-Service (MaaS) model, offered via subscription plans ranging from $199 per month to $1,499 annually. Its emergence coincided with the discontinuation of ACR Stealer in the summer of 2024 and the disruption of another major player—Lumma Stealer—positioning Amatera as a likely frontrunner in the dark web malware economy.
Its primary distribution vector is through web injection campaigns, notably spearheaded by a threat group known as ClearFake. Attackers compromise legitimate websites with malicious HTML and JavaScript, often leveraging techniques like EtherHiding—a method that embeds malicious scripts into the Binance Smart Chain blockchain.
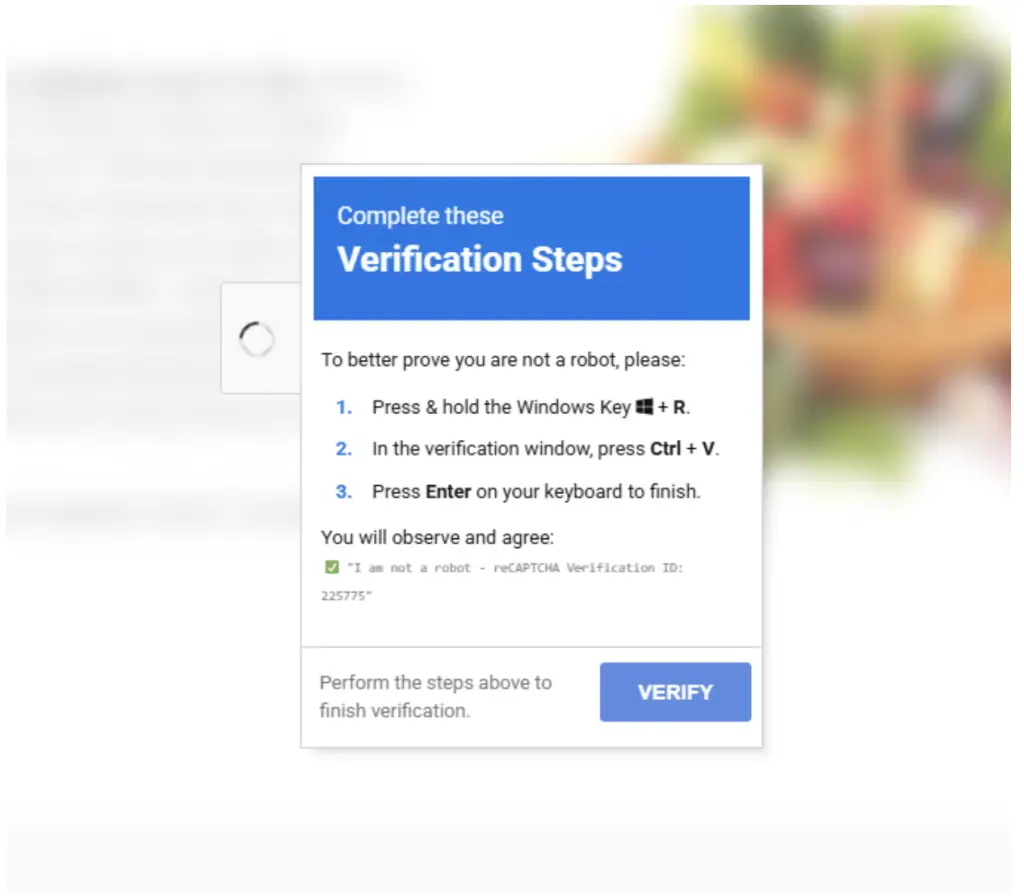
Additional infection vectors involve social engineering techniques, such as ClickFix, which manipulates victims into executing commands via the “Run” dialog (Win+R), thereby triggering a malicious PowerShell script. This initiates a multi-stage loader sequence that ultimately deploys Amatera Stealer via shellcode injection.
The trojan also spreads through counterfeit applications, pirated software cracks, and fake installers, highlighting its adaptability and mass-market appeal.
Once inside the host system, Amatera employs unconventional communication mechanisms with its command-and-control (C2) infrastructure. Rather than using standard Windows APIs, it leverages the NTSockets library, enabling it to circumvent conventional network monitoring tools. Moreover, it utilizes WoW64 syscalls—low-level system calls that bypass user-mode defenses—thereby minimizing detection by Endpoint Detection and Response (EDR) solutions.
To further obscure its network footprint, the malware connects to hardcoded IP addresses, camouflaging its traffic as if it originated from legitimate Content Delivery Networks (CDNs) such as Cloudflare. This tactic allows it to evade DNS filters and maintain the façade of legitimacy.
Amatera Stealer is meticulously crafted for exfiltration of sensitive data: it harvests credentials from browsers, cryptocurrency wallets, email clients, and messaging applications. It also supports the downloading of secondary payloads on demand. C2 configurations are transmitted as JSON files over HTTP, allowing attackers to dynamically alter the malware’s behavior—ranging from script updates to deployment of entirely new threats.
Future updates are expected to introduce HTTPS support, enhancing its concealment capabilities even further. Its rapid development and reliance on advanced detection evasion techniques mark Amatera as a particularly dangerous addition to the cybercriminal toolkit. Experts strongly advise reinforcing defenses against social engineering and restricting the execution of PowerShell scripts without strict administrative oversight.


