Analysts at Symantec have uncovered serious vulnerabilities in several widely used Google Chrome extensions, jeopardizing the privacy and security of users. The issues stem from the transmission of sensitive data over unsecured HTTP protocols and the presence of hardcoded secrets within the extensions’ source code.
According to cybersecurity researcher Yuanjing Guo of the Symantec team, multiple popular extensions are inadvertently transmitting sensitive data through unencrypted HTTP connections. Among the leaked data are visited domain names, device identifiers, operating system details, usage analytics, and even information regarding extension uninstallation—all sent in plaintext. The lack of encryption renders this traffic vulnerable to adversary-in-the-middle (AitM) attacks. Malicious actors on the same network—such as a public Wi-Fi—can not only intercept this data but also tamper with it, potentially leading to severe consequences.
The list of insecure extensions includes:
- SEMRush Rank and PI Rank, which connect over HTTP to
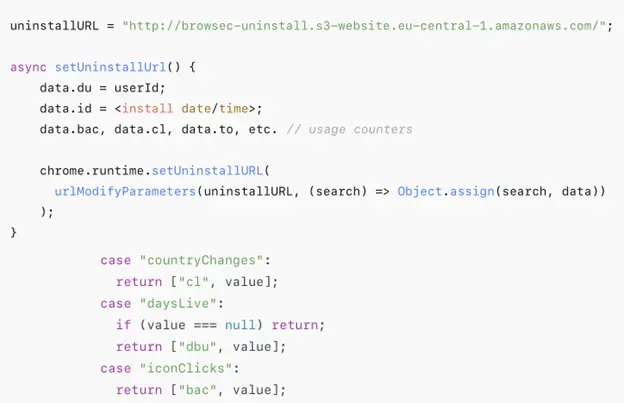
rank.trellian[.]com; - Browsec VPN, which sends an HTTP request to
browsec-uninstall.s3-website.eu-central-1.amazonaws[.]comupon removal; - MSN New Tab, MSN Homepage, and Bing Search & News, which transmit unique device identifiers to
g.ceipmsn[.]com; - DualSafe Password Manager, which sends usage statistics, extension version, and browser language to
stats.itopupdate[.]com.
Although no direct leakage of passwords was observed, the mere fact that a password manager transmits telemetry via an unsecured channel undermines confidence in its reliability.
Symantec also identified another group of extensions that embed API keys, tokens, and secrets directly in their code. These exposed credentials can be exploited by threat actors to craft malicious requests or conduct sophisticated attacks.
Notable examples include:
- AVG Online Security, Speed Dial [FVD], and SellerSprite, which hardcode Google Analytics 4 (GA4) secrets, potentially allowing for metric manipulation;
- Equatio, which contains a Microsoft Azure key used for speech recognition;
- Awesome Screen Recorder and Scrolling Screenshot Tool, which expose an AWS developer key used to upload screenshots to an S3 bucket;
- Microsoft Editor, which uses a telemetry key (
StatsApiKey) for data collection; - Antidote Connector, which relies on a third-party library (InboxSDK) containing embedded API keys—a library that is also used in over 90 other extensions whose names remain undisclosed;
- Watch2Gether, Trust Wallet, and TravelArrow, which expose public API keys for Tenor, Ramp Network, and ip-api, respectively.
Should these keys fall into the wrong hands, they could be used to falsify telemetry, simulate cryptocurrency transactions, host illicit content, or incur inflated API usage costs for developers.
Experts stress the severity of the issue: from GA4 to Azure, from AWS to Ramp—just a few lines of unsecured code can compromise entire services. The recommended solution is to avoid storing sensitive credentials on the client side and to rely exclusively on secure communication channels.
Users are advised to uninstall any vulnerable extensions until developers remediate the unsecured HTTP calls. Unencrypted traffic is not an abstract threat—it can be easily intercepted and leveraged for phishing, surveillance, and targeted attacks.
Ultimately, neither popularity nor brand recognition guarantees adherence to basic security principles. Extensions must be scrutinized for the protocols they use and the nature of the data they transmit—only then can true data protection be ensured.


