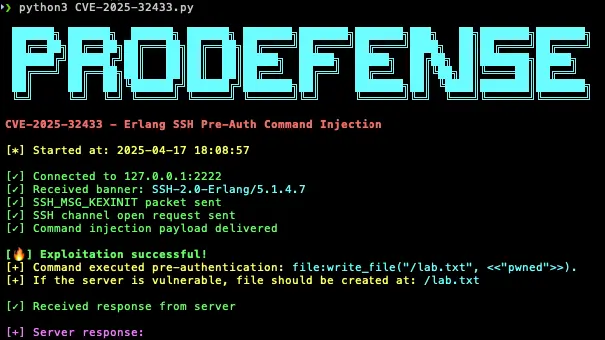
The automation of exploit development is no longer a distant vision of the future—it is a present reality. Armed with the right prompts and access to open-source data, artificial intelligence can now transform a vulnerability description into a working exploit in a matter of hours. This was demonstrated by a ProDefense expert who, in the span of a single evening, created an exploit for a critical vulnerability in the Erlang SSH library (CVE-2025-32433).
The inspiration arose from a post by Horizon3.ai, which highlighted the relative ease of crafting an exploit for the flaw. Matthew Keeley set out to test whether AI could traverse the path from CVE disclosure to functioning code—and the results left him astonished. GPT-4 and Claude Sonnet 3.7 not only grasped the nature of the vulnerability but also compared the patched code to the original, pinpointed the differences, and articulated the essence of the security flaw.
Initially, the model attempted to construct a fuzzing framework—and succeeded in establishing the environment: Docker files, configurations for the vulnerable SSH server, and testing commands. While fuzzing did not yield a direct exploit, it served as a vital starting point. Once diff files from the published patch were introduced, GPT-4 was able to generate a fully functional proof-of-concept (PoC) and even explained the vulnerability’s logic, identifying how the code change mitigated unauthenticated message handling.
The first exploit attempt failed—an expected outcome for generated code. Keely then employed another AI tool—Cursor, powered by Claude Sonnet 3.7—which completed the necessary refinements. The end result was a working PoC, produced in just a few hours through prompt engineering and open-source analysis.
The velocity at which one can now move from CVE publication to live attack has accelerated dramatically. As Keely observes, what once took days or weeks can now be achieved in a single day. He notes that over the past year, the pace of vulnerability exploitation has surged, along with adversarial coordination: the same vulnerability can be leveraged globally—across industries, regions, and infrastructures—within mere hours of disclosure.
This surge in threat velocity is borne out by statistics: the number of published vulnerabilities (CVEs) increased by 38% between 2023 and 2024. It marks not only a rise in volume but a systemic acceleration from discovery to exploitation.
For defenders, this new landscape demands immediacy. Every new CVE must be treated as potentially already weaponized. Defense strategies must include the capability for urgent, secure patch deployment. It is the only way to keep pace with a world in which AI transforms malicious intent into operational exploits before administrators even finish reading the vulnerability description.


