A new frontier in automated vulnerability discovery has been reached through the integration of the Claude chatbot with reverse engineering tools. A team of specialists from TrustedSec has implemented a groundbreaking approach in which artificial intelligence is harnessed to uncover previously unknown vulnerabilities within signed Microsoft binary files—potentially revolutionizing how cybersecurity professionals analyze code and detect threats.
In the course of their research, Claude was trained to interact with the Model Context Protocol (MCP) and analyze .NET assemblies in a fully autonomous manner. To achieve this, the developers deployed a custom MCP server utilizing ilspycmd—a decompilation tool for .NET—within a Docker container. This eliminated the need for manual analysis, granting the AI access to the complete structure of the assemblies, including private methods and internal calls.
The result was not only the identification of potential weaknesses but also the construction of full exploitation chains—culminating in the generation of working proof-of-concept code that validated the discovered vulnerabilities.
AI Breakthrough: Claude Chatbot Automates Zero-Day Discovery in Microsoft Binaries, Generates PoC Exploits!One of the most notable cases involved the System.AddIn.dll library, which is bundled with Windows. Claude identified a critical vulnerability related to the unsafe use of BinaryFormatter in the file AddInStore.cs. The methods ReadCache and WriteCache performed serialization and deserialization without proper validation, paving the way for attacks via specially crafted cache files.
While the vulnerability itself had been previously documented, it was used in this experiment as a benchmark to test analytical depth. Claude not only confirmed its existence but precisely mapped all possible exploitation vectors, including the -addinroot and -pipelineroot parameters in the AddinUtil.exe utility, which could lead to arbitrary code execution.
What proved especially impressive was Claude’s ability to trace the execution flow step by step—from user input to the invocation of the vulnerable Deserialize() method. The AI pinpointed that the dangerous code path is triggered via AddInStore.Update() or AddInStore.Rebuild(), which then proceed to GetPipelineDeploymentState(), where the unsafe deserialization occurs.
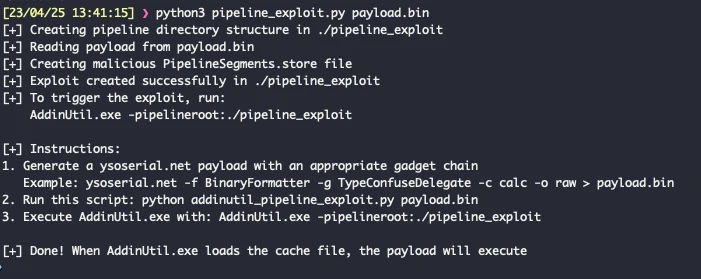
Claude also demonstrated a sophisticated understanding of binary file structures. It generated a Python script capable of creating the correct directory hierarchy (HostSideAdapters, Contracts, AddInSideAdapters, AddInViews) and populating it with a PipelineSegments.store file containing the precise 12-byte header expected by ReadCache. The result: successful execution of arbitrary code via AddinUtil.exe.
In this way, Claude showcased not only the ability to identify vulnerabilities but also to autonomously craft functional exploit chains with minimal human intervention. This marks a significant paradigm shift in software analysis—from manual code review to large-scale, deep inspection driven by artificial intelligence.
Such an approach heralds a new era in zero-day vulnerability hunting within corporate and critical infrastructure systems. Amid increasing pressure on security teams and the growing need for accelerated discovery, tools like this may become catalysts for scalable, intelligent automation in software security.


