A recently mitigated vulnerability in VMware ESXi hypervisors is being actively exploited by several ransomware groups to gain elevated privileges and deploy file-encrypting malware.
These attacks leverage the CVE-2024-37085 vulnerability (CVSS score: 6.8), which allows authentication bypass during integration with Active Directory, granting administrative access to the host.
VMware, a subsidiary of Broadcom, noted in a June advisory that an attacker with sufficient privileges in Active Directory can gain full access to the ESXi host by configuring AD settings to manage users. This can be achieved by creating a new AD group named “ESX Admins” and adding a user to it, or by renaming any group in the domain to “ESX Admins.”
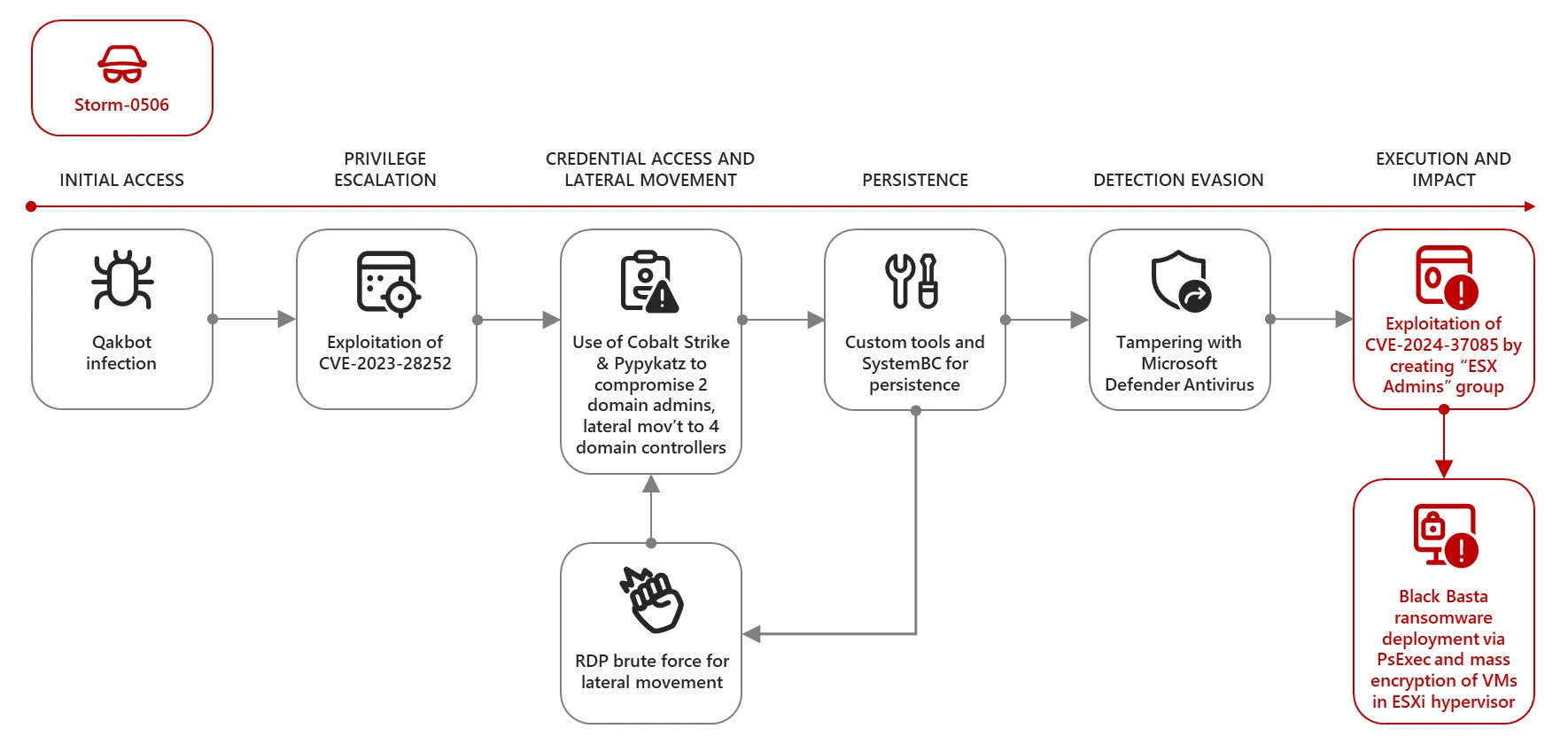
Microsoft, in its analysis published on July 29, reported that ransomware groups such as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest are using this technique to deploy Akira and Black Basta. Researchers emphasized that ESXi hypervisors connected to an Active Directory domain by default grant full administrative rights to any member of a domain group named “ESX Admins.” ESXi does not verify the actual existence of such a group.
In one attack by Storm-0506 on an unnamed engineering firm in North America, attackers exploited the vulnerability to escalate privileges on ESXi hypervisors after initial access was gained using QakBot and another vulnerability in the Windows CLFS driver (CVE-2023-28252, CVSS score: 7.8).
The attackers then deployed Cobalt Strike and Pypykatz (a Python version of Mimikatz) to steal domain administrator credentials and further propagate across the network. To maintain persistence, they used the SystemBC implant and gained access to ESXi to deploy Black Basta.
Attempts to compromise RDP connections for lateral movement and further deployment of Cobalt Strike and SystemBC were also documented. The attackers attempted to alter Microsoft Defender Antivirus settings to evade detection.
Mandiant, a Google subsidiary, reported that the financially motivated group UNC4393 uses initial access via a C/C++ backdoor codenamed ZLoader to deploy Black Basta, moving away from using QakBot and DarkGate.
Mandiant notes that UNC4393 shows a willingness to collaborate with multiple distribution clusters to achieve its goals. The latest wave of ZLoader activity began earlier this year and is primarily spread through malicious advertising, differing significantly from previous phishing-focused methods.
During these attacks, initial access is used to deploy Cobalt Strike Beacon and other reconnaissance tools. Lateral movement is achieved using RDP and SMB, while SystemBC is used for persistence.
The ZLoader loader, which returned to the attackers’ arsenal last year, is actively evolving. New variants are spread via a PowerShell backdoor named PowerDash.
In recent years, ransomware operators have increasingly adopted new methods to maximize impact and evade detection, frequently targeting ESXi hypervisors and exploiting new vulnerabilities in internet-facing servers.
For instance, the Qilin ransomware, originally developed in Go, has now been rewritten in Rust for enhanced security. Recent attacks using Qilin target vulnerabilities in Fortinet and Veeam Backup & Replication for initial access. The attackers use the Killer Ultra tool to disable EDR programs and clear Windows event logs to conceal traces of compromise.
Organizations are advised to install the latest software updates, maintain credential hygiene, employ two-factor authentication, and protect critical assets with appropriate monitoring procedures and recovery plans.


