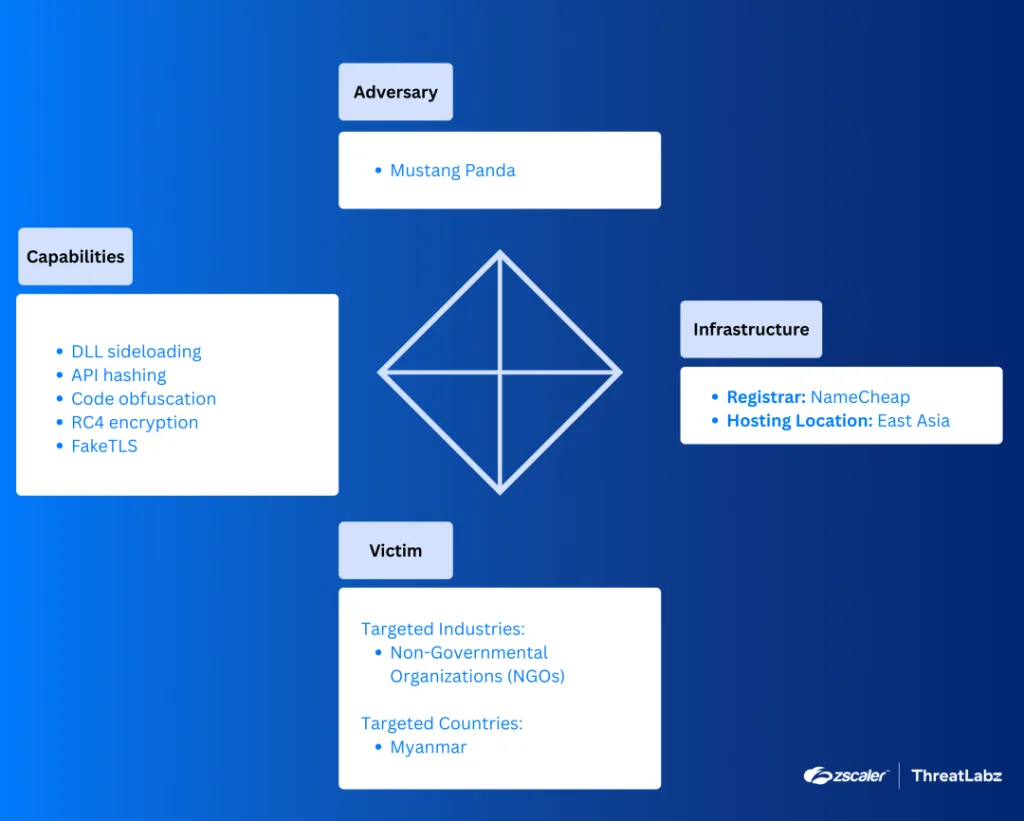
The China-linked threat actor Mustang Panda has once again drawn attention following a cyberattack targeting an organization in Myanmar. The operation featured a wave of previously unseen malicious toolsets, underscoring the group’s methodical and targeted approach, as well as its growing sophistication and stealth in executing cyber espionage campaigns.
At the heart of the recent attacks lies an updated variant of the TONESHELL backdoor. According to Zscaler ThreatLabz (1,2), this version employs an enhanced FakeTLS communication protocol to interact with its command-and-control (C2) server. Additionally, it introduces a revamped technique for generating and storing victim identifiers, reducing the likelihood of detection and increasing resilience within compromised environments.
Beyond the core TONESHELL variant, researchers identified three distinct modifications of the malware. The first functions as a traditional reverse shell, the second enables dynamic DLL loading from the C2 server and injects them into legitimate processes such as svchost.exe, and the third—most sophisticated—variant supports arbitrary file downloads and command execution via a bespoke TCP protocol.
A major enhancement to the group’s toolkit is the StarProxy module, designed for lateral movement within internal networks. Deployed using DLL sideloading, it also leverages the FakeTLS protocol. StarProxy acts as a proxy between compromised hosts and C2 infrastructure, encrypting traffic with a custom XOR algorithm via TCP sockets. Its deployment is particularly effective in environments where infected systems lack direct internet access.
In addition, Zscaler’s investigation revealed two newly developed keyloggers—PAKLOG and CorKLOG. Both tools capture keystrokes and clipboard content, though CorKLOG goes further by encrypting logs using RC4 encryption and establishing persistence mechanisms via system services and scheduled tasks. Notably, neither keylogger independently transmits the collected data; this responsibility falls to external components, complicating detection efforts.
Another sophisticated element in Mustang Panda’s arsenal is a Windows kernel driver named SplatCloak. Installed through a utility called SplatDropper, this driver disables security mechanisms associated with Windows Defender and Kaspersky Lab products, allowing malicious processes to operate unimpeded by defensive tools.
Mustang Panda—also known by aliases such as BASIN, Bronze President, Camaro Dragon, and Earth Preta—has been active since at least 2012. The group traditionally targets government agencies, military entities, ethnic minorities, and non-governmental organizations across East Asia. While it was once known for its widespread use of PlugX via DLL sideloading, recent years have seen a clear transition to more adaptive and technically advanced toolsets.
The growing diversity of malware components, frequent updates, and layered obfuscation techniques reflect a threat actor with high operational maturity and tactical flexibility. These measures are carefully calibrated to increase the effectiveness, survivability, and stealth of its campaigns within the increasingly competitive realm of cyber espionage.


