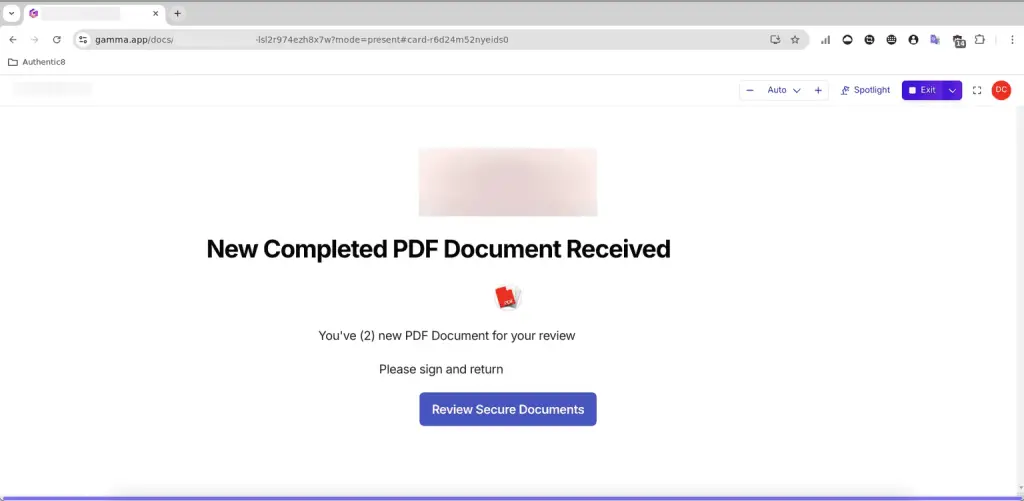
A cybercriminal group has begun exploiting the Gamma platform—an AI-powered presentation tool—in a newly orchestrated, multi-stage phishing campaign. Victims are lured into visiting a counterfeit Microsoft SharePoint login page, where their credentials are stealthily harvested.
Researchers at Abnormal Security revealed that the PDF file attached to the phishing email is, in fact, a disguised link to a Gamma presentation, masquerading as a secure document viewer. Upon clicking the link, the victim is directed to an intermediary page that mimics a Microsoft service interface, fortified with Cloudflare Turnstile CAPTCHA protection. This layer of legitimacy not only deceives the user but also reduces the likelihood of detection by automated security analysis tools.
The attack then proceeds to redirect the victim to a fraudulent Microsoft SharePoint login portal. Here, the attackers employ an Adversary-in-the-Middle (AitM) mechanism to validate the submitted credentials in real time, presenting an error message if the password is incorrect—thereby ensuring the data is accurate and usable.
This sophisticated scheme falls under the “Living-off-Trusted-Sites” (LoTS) category—leveraging legitimate online platforms to host malicious content, effectively bypassing traditional security filters such as SPF, DKIM, and DMARC. By exploiting less conspicuous tools like Gamma, the threat actors elude conventional detection systems while manipulating user trust. The presentation platform becomes not merely a camouflage layer but a pivotal element in a meticulously crafted redirection chain, obscuring the ultimate objective of the campaign.
Phishing attacks continue to evolve in complexity, adeptly incorporating trusted tools and legitimate services to conceal malicious intent. The incident involving Gamma underscores how seemingly benign technologies can be weaponized as part of a broader, well-coordinated breach.
Security mechanisms designed for overt threats are rendered ineffective against campaigns that exploit brand trust and intricate redirection paths. This highlights the urgent need for a continuous reevaluation of cybersecurity strategies and heightened scrutiny of unconventional uses of familiar digital platforms.


