High-level overview of GRAPELOADER infections
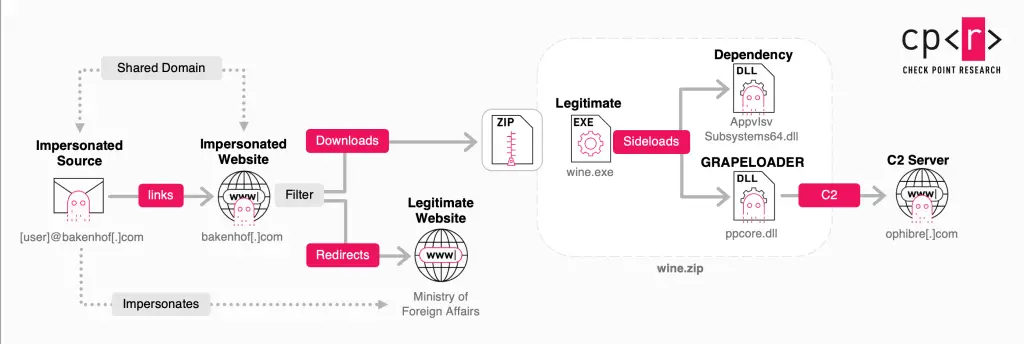
The cyber-espionage group Midnight Blizzard has launched a new phishing campaign targeting diplomatic institutions across Europe, including embassies. According to Check Point Research, since January 2025, the threat actors have been distributing fraudulent emails purporting to originate from foreign ministries, inviting recipients to a wine tasting event. The campaign utilizes spoofed domains, including “bakenhof[.]com” and “silry[.]com.”
The malicious payload is embedded within a “wine.zip” archive, which is only accessible to recipients who meet certain predefined criteria. If a user does not qualify, they are redirected to the legitimate ministry website—an evasion technique designed to avoid arousing suspicion. Inside the archive lies a legitimate executable, “wine.exe,” disguised as a PowerPoint presentation, alongside a malicious component named “ppcore.dll”—a loader known as GrapeLoader.
The malware is executed via DLL hijacking and immediately begins collecting system information. It then modifies the Windows Registry to achieve persistence, before establishing a connection to a command-and-control (C2) server, from which the primary malicious payload is fetched directly into system memory. Detection evasion mechanisms include a 10-second execution delay and the use of PAGE_NOACCESS memory protection to bypass antivirus and EDR solutions.
Researchers note that GrapeLoader represents a sophisticated evolution from its predecessor, RootSaw, offering improved stealth and a more refined architecture. Its principal function is reconnaissance and delivery of the second-stage payload, a modular backdoor named WineLoader, which masquerades as a legitimate VMware Tools library.
WineLoader collects extensive data from the infected machine, including IP address, username, hostname, process ID, privilege level, and other environment variables. This telemetry is used to determine whether the malware is running in a sandboxed environment and to assess the necessity of delivering additional components.
The identified variant of WineLoader incorporates advanced anti-analysis features, including duplicated relative virtual addresses, export table manipulation, insertion of junk instructions, and a complex string obfuscation scheme. Where tools such as FLOSS previously succeeded in extracting readable strings from malware samples, these newer techniques render automated analysis largely ineffective.
Due to the fileless nature of the attack—executing entirely in memory—and the highly targeted nature of the phishing emails, Check Point researchers were unable to obtain a complete second-stage payload or its auxiliary modules. As a result, the full capabilities of WineLoader remain unknown.
Nevertheless, the research underscores the increasing sophistication of APT29’s toolkit. The group continues to refine its stealth strategies, embrace modularity, and advance its methods for circumventing modern security defenses. These developments demand that defenders adopt multilayered security architectures and enhanced monitoring capabilities to detect and respond to such threats in a timely manner.


