The Chinese cyberespionage group UNC5174, also known as Uteus or Uetus, has launched a new campaign targeting Linux systems by deploying a modified version of the SNOWLIGHT malware and the open-source VShell tool. The operation was uncovered by researchers at Sysdig, who noted that adversaries are increasingly adopting such tools not only for cost efficiency but also to masquerade as less sophisticated, disorganized attackers.
Previously linked to the Chinese government, UNC5174 had remained relatively dormant over the past year. However, the emergence of this campaign signals a resurgence in activity, now supported by a more advanced operational infrastructure.
Among the vulnerabilities exploited in earlier breaches were flaws in ConnectWise ScreenConnect and F5 BIG-IP, which enabled the deployment of the SNOWLIGHT ELF binary, written in C. This component functions as a loader for the tunneling module GOHEAVY—developed in Go—which communicates with command-and-control servers via the SUPERSHELL platform.
The attackers also leveraged GOREVERSE, a reverse shell written in Go that operates through SSH. The French cybersecurity agency ANSSI confirmed similar activity resembling UNC5174’s tactics, citing the exploitation of vulnerabilities in Ivanti Cloud Service Appliance. The campaign utilized CVE-2024-8963, CVE-2024-9380, and CVE-2024-8190 to gain control of target systems and execute arbitrary code.
Both SNOWLIGHT and VShell are cross-platform, capable of running on Linux and macOS. VShell, in particular, was disguised as a counterfeit Cloudflare authentication application. According to forensic data, such executables were uploaded to VirusTotal from China as early as October 2024, indicating prior testing of this malware pairing.
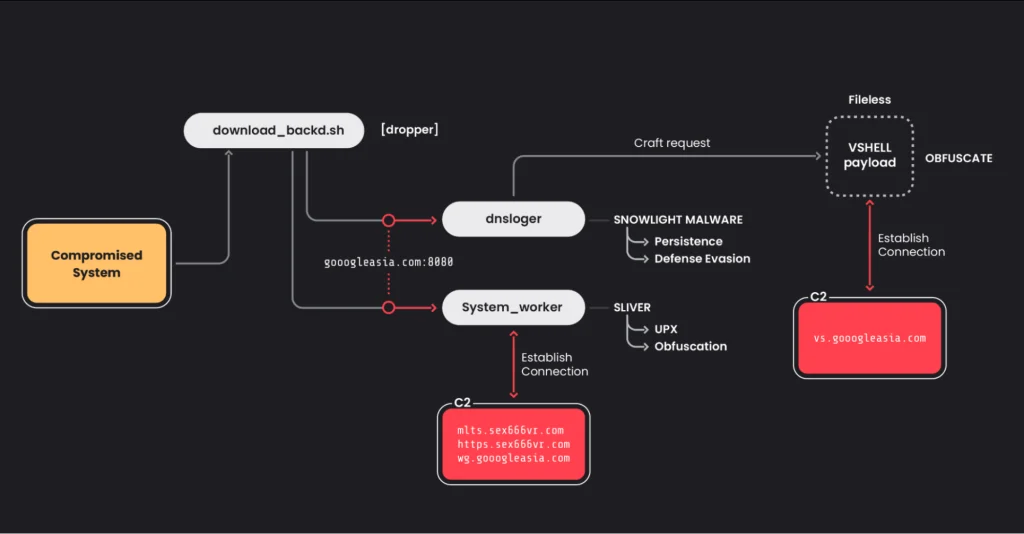
In an attack recorded in January 2025, SNOWLIGHT operated as a loader for VShell—a remote access trojan (RAT) that resides solely in memory, leaving no trace on disk and thereby evading conventional detection methods. An unidentified initial access vector was used to execute a malicious bash script named download_backd.sh, which installed two binary payloads: dnsloger (SNOWLIGHT) and system_worker (a Sliver module), both of which established persistence and maintained communication with the command-and-control infrastructure.
In the final stage of the intrusion, SNOWLIGHT initiated contact with its C2 server to retrieve VShell. The RAT enables full remote control over the compromised system, supporting command execution and file transfers. Of particular concern are its stealthy techniques, including the use of WebSocket connections and complete absence of disk-based artifacts.
Meanwhile, cybersecurity firm TeamT5 reported a similar intrusion campaign, also believed to originate from China, involving the deployment of SPAWNCHIMERA malware through Ivanti product vulnerabilities. The attacks targeted organizations across 20 countries, including Austria, Australia, France, Japan, South Korea, Singapore, the United Arab Emirates, the United Kingdom, and the United States.
Amid these developments, China has accused the U.S. National Security Agency of conducting cyberattacks against infrastructure linked to the Winter Asian Games, held in February in Harbin. According to China’s CVERC, over 170,000 attacks from American IP addresses were detected between January 26 and February 14, with total foreign-origin attacks exceeding 270,000. Beijing has characterized the U.S. actions as a threat to national security and interference with the nation’s critical infrastructure.


