Overview of Slow Pisces “coding challenges” campaign | Image: Unit 42
On February 21, 2025, the largest cryptocurrency heist in history began to unfold when hackers seized a wallet belonging to Bybit, the world’s second-largest exchange. The losses amounted to nearly $1.5 billion. In an effort to obscure their tracks, the perpetrators rapidly dispersed the stolen funds across dozens of wallets and platforms, then commenced a sophisticated laundering operation.
All indicators point to the involvement of the North Korean hacking group TraderTraitor. Despite the staggering losses, Bybit managed to stay afloat by securing cryptocurrency loans and offering a reward for assistance in recovering the stolen assets. Almost immediately after the incident, the FBI identified TraderTraitor—an offshoot of the infamous Lazarus Group operating under the direction of North Korean intelligence—as the likely culprit.
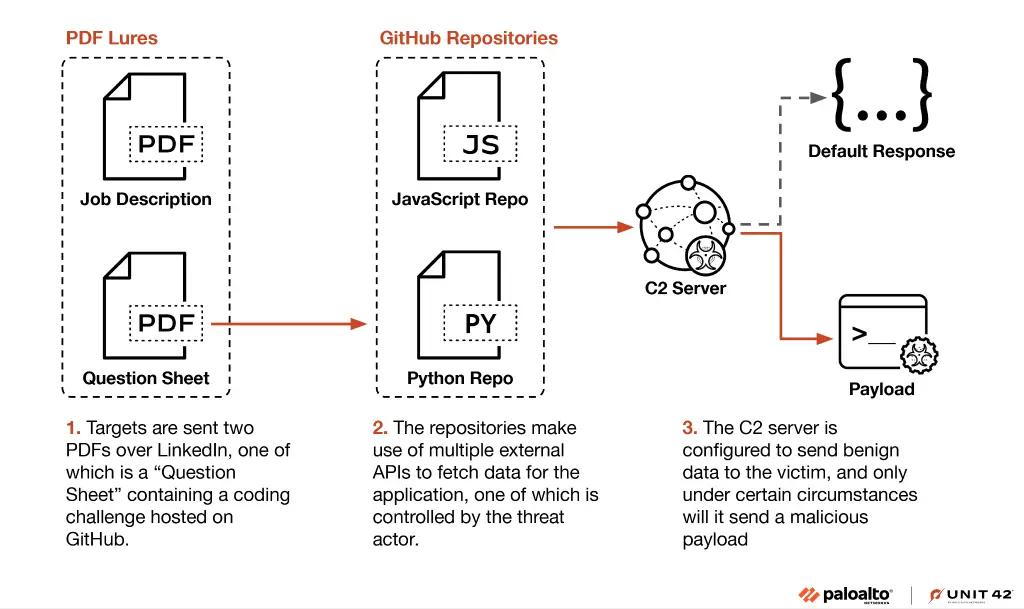
This was not their first appearance on investigators’ radars. TraderTraitor has previously been linked to high-profile crypto thefts and software supply chain compromises. Experts note the group’s strategic targeting of Web3 employees, particularly developers, via meticulously crafted phishing campaigns. They monitor industry personnel, create fake profiles on GitHub, Telegram, LinkedIn, and Slack, and infect victims with tailored malware.
A core element of their toolkit includes macOS-specific backdoors such as PLOTTWIST and TIEDYE, which are designed to evade detection while allowing stealthy movement within networks. Once access to crypto wallets is secured, the group executes an intricate laundering process detailed by analysts at Elliptic: the stolen funds are fragmented, routed through countless wallets, converted into resilient assets like Ethereum and Bitcoin, and funneled through mixers to obscure their origin.
This operational model is repeated year after year. In March 2024, TraderTraitor was responsible for the $308 million theft from Japanese firm DMM. Their tactics continually evolve to evade blockchain forensics and infiltrate infrastructure across the crypto ecosystem. Their reach extends into software platforms as well—in June 2023, they compromised identity management provider JumpCloud.
Gradually, the group has grown more organized and technically advanced. Unit 42 researchers uncovered a new tool dubbed RN Loader, which installs data-stealing modules and then self-deletes to minimize detection risk. Such advancements highlight the group’s increasing emphasis on stealth and persistence.
Key to the effectiveness of North Korea’s cyber program is the coordination between its various arms. Some experts suspect strong links between the hackers and proxy IT workers embedded in Western companies. These operatives may act in concert—some extracting profits, others siphoning sensitive data or coercing former employers.
Notably, North Korea does not merely tolerate these actors—cyberattacks have become a strategic instrument for national financing. The stolen funds are not used for personal enrichment but are funneled into the regime’s nuclear ambitions and government operations. Analysts assert that North Korea remains the most sophisticated nation in the realm of cryptocurrency laundering, with its methods growing ever more elusive.


