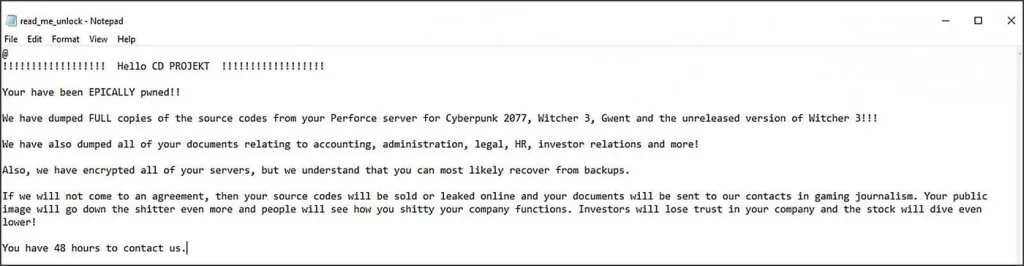
Ransom Note dropped by HelloKitty Group
Researchers at The Raven File have identified renewed activity from the HelloKitty ransomware, which now targets not only Windows systems but also Linux environments, including ESXi virtual infrastructure. First detected in 2020, HelloKitty originated as a fork of DeathRansom but has since evolved significantly in both architecture and operational methodology.
Modern variants of HelloKitty employ a hardcoded RSA-2048 public key, which is hashed via SHA256 to generate a unique victim identifier. For each encrypted file, a distinct 32-byte value is derived from a processor timestamp. Encryption is layered—first using the Salsa20 algorithm, followed by AES. The resulting files bear extensions such as .CRYPTED, .CRYPT, or .KITTY, and include metadata with the RSA-encrypted file size, key, and a “magic” value necessary for decryption.
Some strains utilize alternative encryption schemes, including NTRU, indicating a rapid adaptation to emerging cryptographic methodologies. While early attacks were primarily focused on Windows, a Linux/ESXi variant appeared in July 2021, significantly broadening the group’s operational landscape.
Of particular note is the geographic footprint of recent samples. Indicators such as embedded language strings, download IP addresses, and references to Chinese platforms like QQ and SkyCN suggest a Chinese origin. However, earlier reports had attributed the group’s operations to Ukraine, raising questions about deliberate obfuscation or a multinational actor composition.
A comparative analysis of infection techniques from 2020 to 2024 reveals marked sophistication. Where earlier versions relied on blunt methods—such as deleting shadow copies, terminating processes, and injecting into the system—newer variants display a more refined and selective approach. The malware now performs in-depth reconnaissance, examining system registries and configurations while deliberately avoiding outdated techniques that are easily detected by modern security solutions.
HelloKitty has impacted not only corporate entities but also critical infrastructure. In December 2020, it affected the Brazilian energy provider CEMIG, and in February 2021, it attacked CD Projekt Red, a major Polish game developer. Subsequent incidents involved healthcare institutions in the UK and IT companies in France.
The ransomware has not been confined to a single threat group. Rather, it has become a widely adopted tool leveraged by high-profile actors such as Vice Society, UNC2447, Lapsus$, and Yanluowang, positioning HelloKitty as a staple of the Ransomware-as-a-Service (RaaS) ecosystem.
Though no active HelloKitty leak sites have been discovered at present, a newly observed variant originating from China—bearing partial code overlap with RingQ malware—may signify a resurgence. The absence of onion addresses suggests the group either has not finalized its infrastructure or is intentionally operating under the radar.
The reemergence of HelloKitty, armed with enhanced encryption, cross-platform capabilities, and ambiguous origins, presents a renewed challenge for cybersecurity professionals. Its operators are clearly learning from past missteps and evolving in step with defensive technologies, rendering HelloKitty one of the most resilient and adaptive ransomware strains in the wild.


