Malware execution flow v2 | Image: Kaspersky
The threat group known as Paper Werewolf, also operating under the alias GOFFEE, has deployed a new malicious tool dubbed PowerModul as part of a targeted cyber campaign against Russian organizations. According to Kaspersky Lab, the group’s activity was observed between July and December 2024, affecting entities across telecommunications, construction, mass media, energy, and government administration sectors.
BI.ZONE reports that Paper Werewolf has been active since 2022 and has carried out no fewer than seven distinct campaigns targeting organizations in industries ranging from energy and finance to media. A hallmark of their operations is not only cyber-espionage but also the deployment of destructive tactics—such as altering employee passwords—to hinder recovery efforts and delay restoration of infrastructure control.
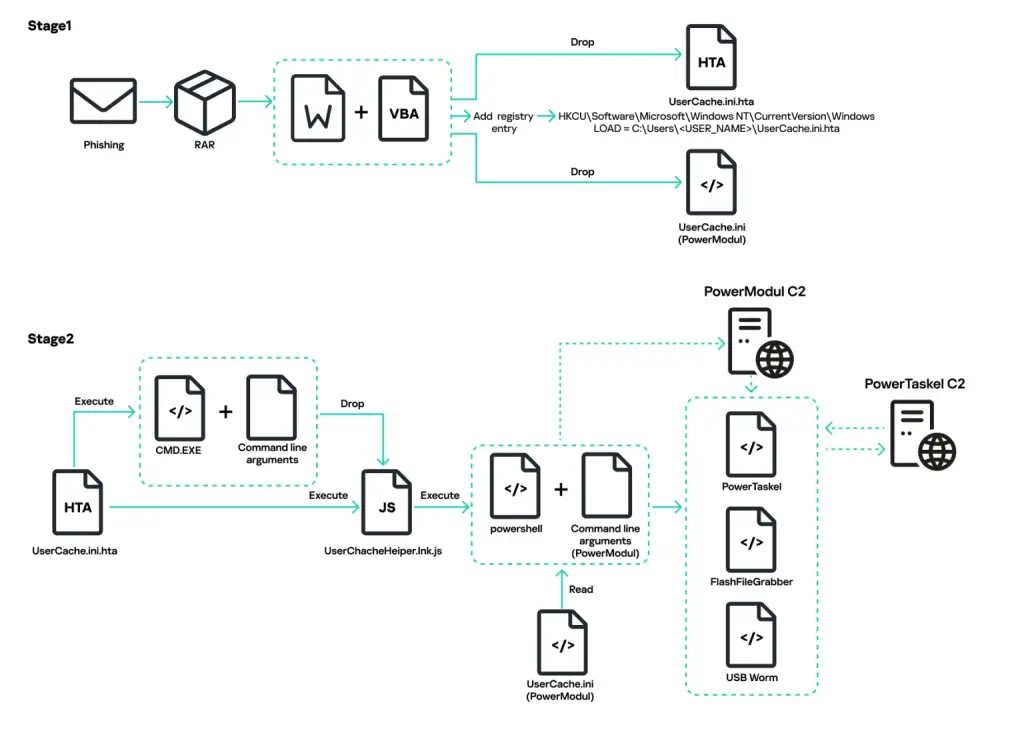
The initial infection vector typically involves phishing emails containing documents with embedded macros. When activated, these macros deliver PowerRAT, a PowerShell-based trojan that serves as a conduit for the next stage of the attack. The payload often consists of a modified version of the Mythic agent, known as PowerTaskel or QwakMyAgent. Additionally, the attackers have leveraged a malicious IIS module called Owowa, which intercepts Microsoft Outlook credentials.
In recent attack chains, the threat actors have used RAR archives containing executable files with deceptive double extensions—such as .pdf.exe or .doc.exe. When executed, these files mimic the behavior of opening a legitimate document by downloading a decoy PDF or Word file from a remote server, while silently deploying a backdoor. For obfuscation, the attackers embed encrypted shellcode into legitimate Windows binaries such as explorer.exe, enabling the agent to establish a connection with the command-and-control (C2) server immediately.
An alternate infection method employs Microsoft Office documents with embedded macros acting as droppers to install and execute PowerModul. This PowerShell-based script enables the download and execution of additional scripts from the C2 infrastructure. In use since early 2024, PowerModul has frequently been utilized as a loader for PowerTaskel.
Among the additional payloads distributed via PowerModul are:
- FlashFileGrabber – a utility designed to exfiltrate files from USB drives and send them to the C2 server.
- FlashFileGrabberOffline – a variant that scans connected USB devices for files with specific extensions and saves them locally.
- USB Worm – a worm capable of infecting removable drives with a replica of PowerModul.
PowerTaskel, in addition to executing PowerShell scripts, collects system metadata as a “check-in” message, executes remote C2 commands, and can escalate privileges using PsExec. In one observed scenario, PowerTaskel received a script containing a FolderFileGrabber module—similar to FlashFileGrabber, but capable of extracting files from remote devices over SMB via a hardcoded network path.
While GOFFEE initially favored malicious Word documents with embedded VBA macros, recent campaigns increasingly lean toward binary Mythic agents for lateral movement within compromised environments.
Simultaneously, BI.ZONE has reported heightened activity from another group, Sapphire Werewolf, which is distributing an updated version of the Amethyst spyware. This tool exfiltrates credentials from Telegram, mainstream browsers (including Chrome, Opera, and Yandex Browser), as well as SSH and FileZilla configuration files and documents stored on USB drives. Analysts suggest this may be part of a broader wave of targeted attacks on the Russian market.


