Significant developments have been observed in the operations of the phishing platform Tycoon2FA, notorious for its ability to bypass multi-factor authentication (MFA) in Microsoft 365 and Gmail. The developers behind this malicious Phishing-as-a-Service (PhaaS) tool have refined its evasion and obfuscation techniques, making it even harder to detect and neutralize.
First identified in October 2023 by security experts at Sekoia, Tycoon2FA has since undergone considerable evolution, growing increasingly sophisticated and elusive. Now, analysts from Trustwave have detailed several critical upgrades that significantly hinder endpoint security systems’ ability to identify malicious activity.
One of the most notable enhancements is the use of invisible Unicode characters to conceal binary payloads within JavaScript code. This technique—first reported by Juniper Threat Labs in February—allows malicious scripts to decrypt and execute stealthily at runtime, evading both automated scans and manual code inspection.
The platform has also abandoned Cloudflare Turnstile in favor of a custom HTML5 canvas-based CAPTCHA featuring randomly generated elements. This move is intended to bypass domain reputation checks while granting threat actors more granular control over the appearance and behavior of phishing pages.
A third major update is the integration of advanced JavaScript anti-debugging mechanisms. Tycoon2FA can now detect browser automation tools such as PhantomJS and Burp Suite, actively blocking any attempts to analyze its malicious content. If suspicious behavior or a failed CAPTCHA response—often a hallmark of security bots—is detected, users are redirected to a decoy or legitimate site, such as rakuten.com.
Trustwave emphasizes that while each of these obfuscation tactics may be familiar individually, their combined deployment drastically complicates efforts to detect and analyze the phishing infrastructure. Consequently, mitigating such attacks becomes significantly more challenging.
Simultaneously, researchers have reported an unprecedented spike in phishing campaigns leveraging SVG files. This technique has been adopted by multiple phishing platforms, including Tycoon2FA, Mamba2FA, and Sneaky2FA. Between April 2024 and March 2025, incidents involving SVG-based attacks surged by an astonishing 1800%.
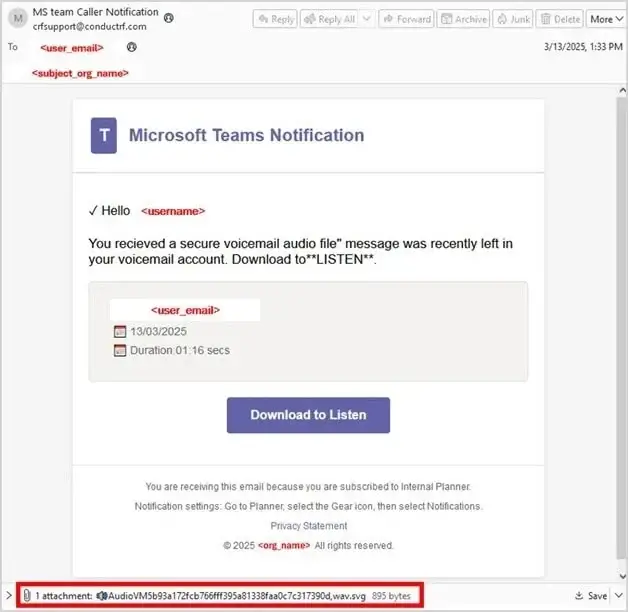
Adversaries disguise these SVG files as voice messages, brand logos, or icons of cloud-hosted documents. Owing to the SVG format’s ability to embed JavaScript, the scripts are triggered automatically when the image is opened in a browser. To evade detection, the malicious code is encrypted using multiple methods in tandem: base64 encoding, ROT13, XOR encryption, and obfuscation via injected junk instructions.
The primary objective of these scripts is to redirect victims to counterfeit Microsoft 365 login portals to steal credentials. One illustrative example cited by researchers involved a phishing email masquerading as a Microsoft Teams voicemail notification. Upon opening the attached SVG file—posing as an audio clip—JavaScript is executed, redirecting the victim to a fake Office 365 login page.
Given the rising prevalence of phishing services and SVG-based lures, users are strongly advised to exercise heightened vigilance when verifying email senders. Key defensive strategies include configuring email gateways to block or flag suspicious SVG attachments and deploying phishing-resistant MFA methods, such as FIDO2-compliant security keys.


