The days when obtaining credentials using Mimikatz was trivially easy are rapidly becoming a thing of the past. Microsoft continues to harden its defenses against credential theft, while EDR systems grow ever more astute. As a result, traditional Red Team tactics—ranging from lateral movement to LSASS interaction—are increasingly triggering alarms within modern security solutions. Yet, the ingenuity of researchers remains undiminished, as they shift their focus toward subtler, but no less potent, methods of attack.
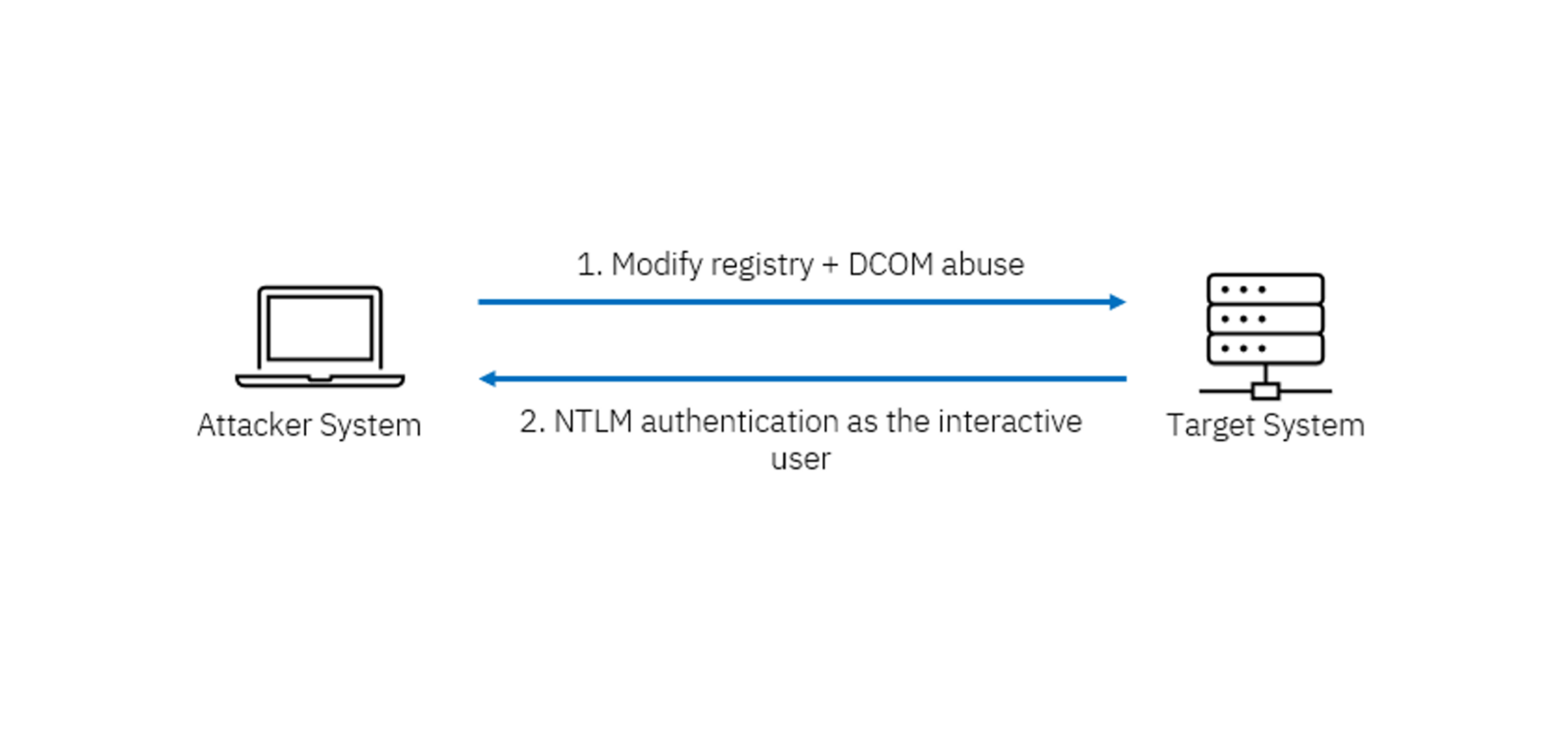
One such method involves exploiting the COM technology and its networked counterpart, DCOM. Though these mechanisms have existed in Windows since the late 20th century, they are seldom leveraged in attacks due to their architectural complexity. COM facilitates inter-application communication, while DCOM extends this capability across networks. Under specific conditions, however, both can serve as tools for session hijacking and coerced NTLM authentication.
A pivotal component in this technique is the RunAs parameter, which dictates the user context under which a DCOM object will execute. Of particular interest is the value “Interactive User,” which enables the object to run under the identity of the currently logged-in user. By modifying the corresponding registry entry, an attacker can inject a malicious DCOM object to execute in the context of another user. Although TrustedInstaller privileges typically restrict such alterations, a local administrator can exploit the SeTakeOwnershipPrivilege to circumvent these protections.
One approach involves forcing NTLM authentication without deploying any malicious binaries. This technique enables the capture of NTLM hashes, which can then be cracked offline or relayed directly to services like LDAP or SMB. It notably avoids detection-prone interactions with LSASS. The method is particularly effective when NTLMv1 is in use, as its hashes can be cracked rapidly using publicly available rainbow tables.
Among the DCOM objects utilized for such attacks is ServerDataCollectorSet, whose Extract method allows for specifying a CAB file path—potentially a UNC path—thereby triggering network authentication. If the object runs under a different user’s context (enabled via RunAs manipulation), the resulting hash can be intercepted. A similar outcome is achieved with the FileSystemImage object by simply modifying its WorkingDirectory property. Intriguingly, the UpdateSession object has been observed to perform network operations as SYSTEM, even when invoked under a user context.
Researchers at IBM have successfully automated this process, incorporating the selection of targetable DCOM objects and enabling the WebClient service to facilitate HTTP-based authentication flows. Their framework also includes credential enumeration and system parameter manipulation to enforce NTLMv1 usage.
As for defense, several key measures are advised. First, enforce mandatory signing for LDAP and SMB, and disable NTLMv1 wherever possible. Second, monitor registry changes involving RunAs and LmCompatibilityLevel, and track the activation of the WebClient service as well as interactions with high-risk DCOM objects. These steps can enable early detection of anomalous behavior and mitigate potential breaches before they escalate.


