Kaspersky Lab researchers have uncovered a malicious campaign in which attackers are distributing a cryptocurrency miner and the ClipBanker trojan, cleverly disguised as Microsoft Office applications. The malware was spread via the SourceForge platform, and the number of affected users in Russia alone has already surpassed 4,600.
The attack leveraged one of SourceForge’s domains—sourceforge.io. Individuals searching for Microsoft software on unofficial websites could be redirected to a project hosted on this domain. The site purportedly offered free downloads of popular Office programs. Upon clicking the provided links, users were taken to a project page featuring a comprehensive list of Microsoft Office applications, each seemingly available for download. However, behind the download buttons lurked hyperlinks leading to malicious archive files.
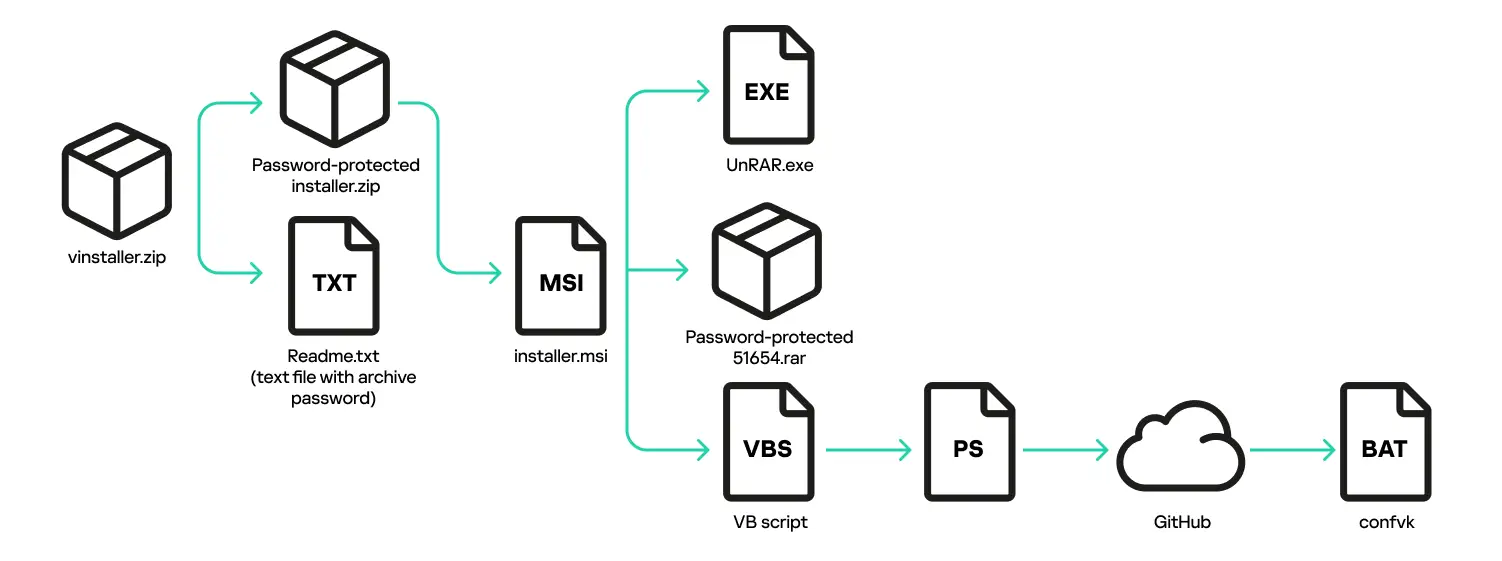
Inside the archive were two components: a password-protected archive and a text document containing the password. Once the protected archive was opened, a chain of downloads delivered two malicious payloads to the victim’s machine. One was a miner, exploiting the infected computer’s processing power to mine cryptocurrency. The other was the ClipBanker trojan, designed to hijack clipboard contents and replace cryptocurrency wallet addresses to reroute funds to the attacker. Notably, no legitimate Microsoft Office software was included in the download. While the primary aim of the campaign appears to be cryptocurrency theft and mining, experts caution that the attackers may later exploit the compromised systems for other malicious purposes, including resale on underground markets.
The perpetrators took advantage of a technical nuance in the SourceForge platform. For every project created on the primary site, sourceforge.net, a separate domain and web hosting instance is automatically provisioned on sourceforge.io. The attackers uploaded a benign project with Office-related add-ons on sourceforge.net, while deploying a deceptive Microsoft Office-themed page with links to malware-laden archives on sourceforge.io.
Security experts note a growing trend of cybercriminals using cloud storage, code repositories, and free hosting services to evade detection and reduce infrastructure costs. These services allow them to blend malicious content among millions of innocuous files.
The analysis also highlighted an interesting feature of the second archive: a file exceeding 700 megabytes in size. This bloated file size was likely designed to lend credibility, giving the impression of a legitimate software installer. In reality, the file employed a technique known as “file pumping,” where useless data is appended to artificially inflate the file size. The actual malicious payload weighed in at a mere 7 megabytes.


