The APT group known as ToddyCat has once again resurfaced, this time employing an unconventional approach to obfuscate its malicious activities. During the investigation of incidents that occurred in 2024, researchers at Kaspersky Lab uncovered a rare tool named TCESB—a previously undocumented creation engineered to surreptitiously execute malicious code within Windows systems.
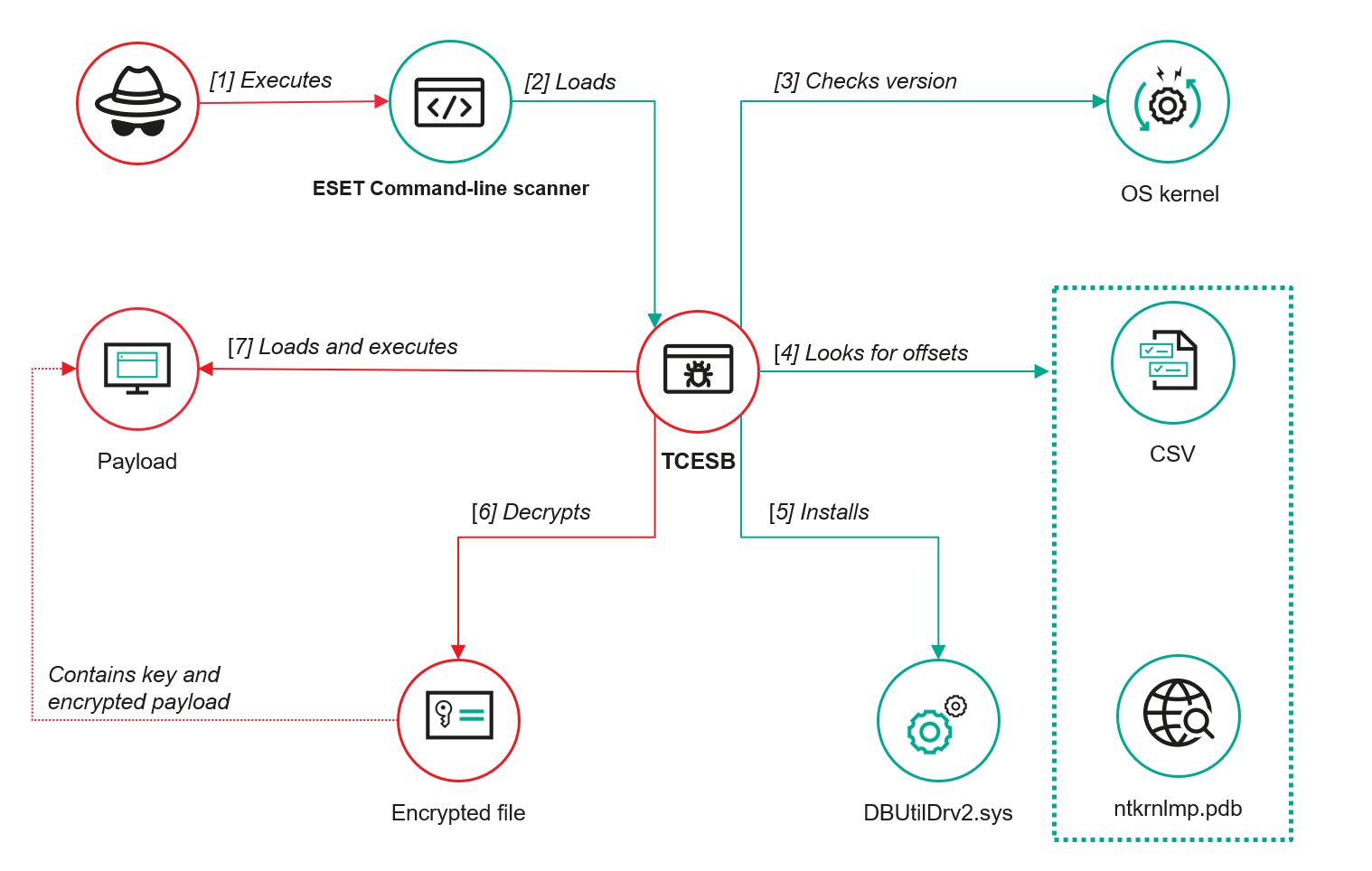
To circumvent security measures, the attackers cleverly exploited trust in legitimate antivirus software, executing the payload within the context of a component belonging to ESET’s security solution.
The TCESB tool masqueraded as the standard system library version.dll, employing a technique known as DLL proxying—a well-documented method wherein a legitimate dynamic-link library is replaced with a malicious one, all while preserving the core functionality of the host application.
Written in C++, the rogue DLL exported all original functions, forwarding calls as expected while quietly embedding its malicious logic. However, successful deployment relied on an additional vulnerability: an application that loads libraries from insecure directories.
This weak point was found in ESET’s Command Line Scanner, an executable that searched for DLL files in the current directory before falling back to the system directory. The attackers leveraged this flaw, which was later cataloged as CVE-2024-11859 and patched by ESET in January 2025, with details publicly disclosed several months later.
A thorough analysis of TCESB confirmed that two instances of version.dll were loaded during scanner operation—one genuine, the other malicious. Internal strings revealed code lineage linked to EDRSandBlast, an open-source tool designed to evade endpoint detection and response systems.
ToddyCat had modified and enhanced this codebase, introducing new features such as the suppression of system alerts related to process creation and library loading.
To surgically manipulate the Windows kernel, TCESB first identified the OS version using its own function, then located the necessary memory offsets. This was achieved by either consulting an embedded CSV file or retrieving debugging symbols (PDB files) from Microsoft servers, enabling precise kernel manipulation across various system builds.
A critical phase of the attack involved the use of a BYOVD (Bring Your Own Vulnerable Driver) technique—specifically installing a vulnerable yet validly signed driver. In this case, the attackers deployed DBUtilDrv2.sys from Dell, which suffers from the well-known vulnerability CVE-2021-36276. TCESB installed the driver via Device Manager, thereby acquiring the ability to alter protected areas of the Windows kernel.
The payload wasn’t immediately executed. Instead, the tool monitored for the appearance of a specific file, decrypting its contents using AES-128 once detected. The decryption key resided in the first 32 bytes of the file, complicating static analysis and bolstering stealth. The decrypted code was then executed in memory, leaving no footprint on disk.
TCESB maintained a meticulous log of its operations, recording everything from driver installation to payload decryption. Researchers observed two different filenames—kesp and ecore, both lacking file extensions—used for the payloads. The code’s structure made it clear that this was a carefully orchestrated attack, engineered to minimize the risk of detection.
The conclusions drawn from the investigation are unequivocal: TCESB is a highly sophisticated tool, derived from open-source roots yet significantly enhanced with bespoke functionality to silently execute malicious operations. Its primary objective is not merely execution but to masquerade as legitimate components and bypass all tiers of system defense.
To mitigate such threats, security professionals recommend monitoring installations of drivers with known vulnerabilities, scrutinizing the download of debugging symbols in environments where kernel debugging is not expected, and verifying the digital signatures of all system libraries loaded into memory.


