In the hospitality industry, incidents are increasingly surfacing in which cybercriminals, masquerading as representatives of Booking.com, gain control over hotel internal systems through seemingly routine correspondence. Hotel staff, accustomed to a constant stream of emails, unwittingly open fraudulent messages, unaware of the carefully orchestrated infection scheme behind them.
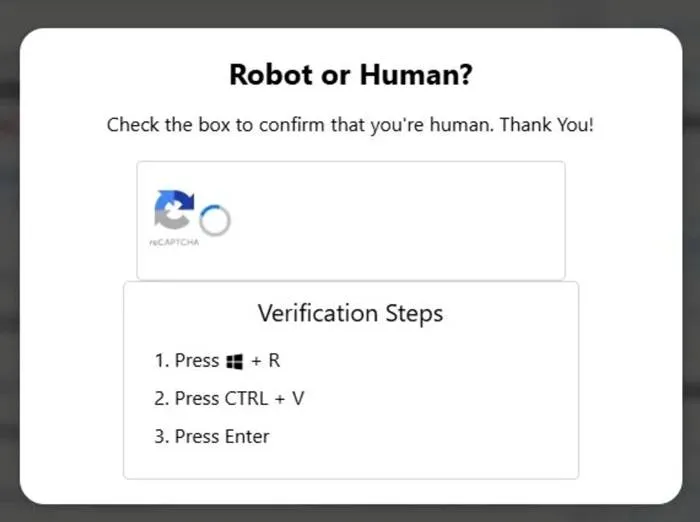
The phishing attack begins with an email virtually indistinguishable from legitimate Booking.com notifications. Within the message is a link purportedly confirming a reservation. Upon clicking, the recipient is redirected to a counterfeit login page, which prompts the user to complete a CAPTCHA. Everything appears authentic—yet it is at this very juncture that the true deception unfolds.
The CAPTCHA does not verify human interaction; rather, it covertly copies a malicious command into the clipboard and then instructs the user to paste it into the Windows command prompt. This single action downloads a trojan, granting the attackers remote access to the hotel’s network. This tactic is widely recognized as ClickFix.
According to cybersecurity firm Malwarebytes, which identified the latest wave of these attacks, the perpetrators target customer data, booking information, and payment credentials. Once access to a single device is secured, cybercriminals can compromise the entire hotel network, exfiltrate thousands of records, and offer them for sale on the dark web. In some cases, ransomware is deployed, locking hotel systems until a ransom is paid.
Domains implicated in the attacks include “vencys[.]com,” “bokcentrpart[.]com,” and “captpart[.]info.” The first distributes phishing emails, the second hosts the deceptive CAPTCHA page, and the third serves as the source of the malware payload.
Booking.com remains an attractive lure for cybercriminals, as its trusted reputation opens the door to sophisticated social engineering schemes. Hotels with automated email handling systems and limited cybersecurity awareness among staff are particularly vulnerable.
To avoid falling victim to such attacks, experts advise following a few fundamental precautions. Do not trust urgent emails, no matter how convincing they appear. Always log into services manually rather than clicking links within emails. Verify the sender’s domain, and never execute terminal commands originating from unverified sources. On an organizational level, hotels should implement staff cybersecurity training programs to mitigate the risk of social engineering attacks.
This case underscores the vital importance of digital hygiene in an industry so deeply rooted in guest trust. Safeguarding client data is an essential component of service quality—and that protection begins with vigilance in the smallest of details.


