The forthcoming Linux 6.15 kernel is set to introduce significant advancements in the cryptographic subsystem, with particularly notable optimizations tailored for modern Intel and AMD processors based on the x86_64 architecture.
As of last week, all updates to the cryptographic codebase have been merged into the mainline development tree. Among these changes are the removal of deprecated compression interfaces, enhancements to the scatterwalk API for handling fragmented memory data, added support for Kerberos5 algorithms, elimination of obsolete SIMD fallback code, the inclusion of a new PCI device identifier “0x1134” in the AMD CCP driver (likely referencing an as-yet-unannounced device), along with various bug fixes.
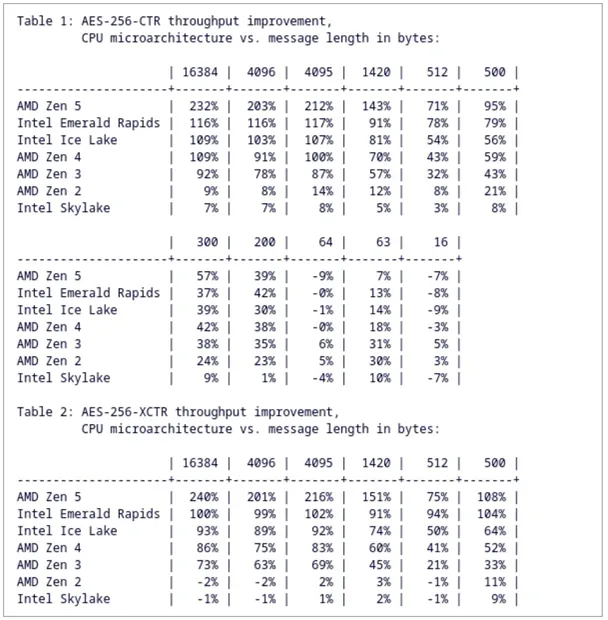
The most impactful improvement for end users, however, lies in the new AES-CTR implementation leveraging the VAES instruction set. This updated code has been meticulously optimized for the latest Intel CPUs and, most notably, AMD’s Zen 5 architecture. Previously reported benchmarks suggest that AES-CTR performance on Zen 5 can be accelerated by up to 3.3 times compared to prior implementations.
This optimization harnesses the combined power of AES-NI, AVX, and VAES — advanced instruction sets designed to enhance cryptographic operations at the hardware level. The patches were authored by Google engineer Eric Biggers, renowned for his substantial contributions to Linux cryptographic acceleration. His work continues a broader trend across recent kernel versions, wherein more algorithms are being adapted to efficiently utilize hardware-backed execution paths, especially on x86_64 platforms.
As a result, users of new-generation AMD and Intel systems can expect a tangible boost in encryption performance, particularly in workloads involving high-throughput data transfer and secure communication.