In the spring of 2025, cybersecurity experts at Check Point uncovered a sophisticated malware campaign specifically targeting Minecraft players. The multi-stage attack hinges on the distribution of counterfeit cheats and mods—such as Oringo and Taunahi—disguised as legitimate Java archives on GitHub. In reality, these files initiate a covert download chain that culminates in the installation of a data-stealing infostealer written in .NET.
The attack begins when a user is lured into downloading a so-called “mod” from GitHub. The bait comprises hundreds of repositories, crafted to appear as repositories for hacked tools or game exploits. The campaign is orchestrated by an underground scheme dubbed Stargazers Ghost Network, which operates around 500 counterfeit repositories, each artificially inflated with stars from approximately 70 fraudulent accounts.
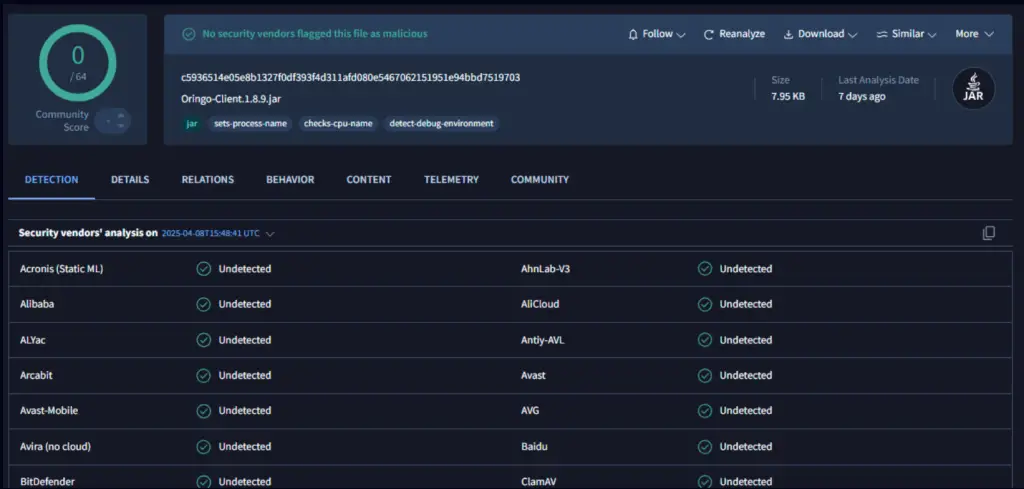
The first stage involves downloading a JAR file—e.g., “Oringo-1.8.9.jar”—engineered with anti-analysis and anti-virtualization measures. Its role is to execute a second Java file which, upon the launch of Minecraft, retrieves the core malicious payload: a data-harvesting component. The URL for the second-stage download is concealed in an encoded format on Pastebin, allowing the attackers to use it as an inconspicuous collection point devoid of direct links to the final host.
For the malware to activate, the player must manually place the JAR file into the Minecraft mods directory:
When the game is launched, the embedded loader scans the directory and triggers the malicious code. This second stage not only downloads the .NET-based infostealer but is itself capable of harvesting Discord and Minecraft tokens, as well as Telegram-related data.
The final infostealer is designed for broad-spectrum data exfiltration. It extracts passwords from browsers, copies the contents of cryptocurrency wallets, and scans for activity in applications like Steam and FileZilla. Additional functions include capturing screenshots, reading clipboard content, and retrieving the device’s external IP address.
All harvested data is compressed and transmitted to the threat actors via Discord Webhooks—delivering it directly into their private channels. According to researchers, this malware chain may have compromised over 1,500 devices.
The report places special emphasis on how gaming communities, particularly the Minecraft ecosystem, are being exploited as effective vectors for malware dissemination. What begins as an innocent attempt to enhance the gaming experience through mods ultimately results in infection by a complex, antivirus-evading malware that causes tangible harm—from stolen credentials to compromised cryptocurrency wallets and messaging accounts.


