A new phishing campaign has been detected in Taiwan, orchestrated by the active APT group known as Silver Fox. Cybersecurity experts report that the threat actors are disseminating malware from the Gh0stCringe and HoldingHands RAT families, posing as government agencies and trusted business partners. The primary attack vector involves email lures themed around taxes, invoices, and pension entitlements.
The first surge of activity in this campaign was observed back in January, marked by the circulation of the malicious Winos 4.0 platform. At the time, the phishing emails impersonated official notifications from Taiwan’s National Taxation Bureau. Similar activity was documented in May by researchers at Rapid7.
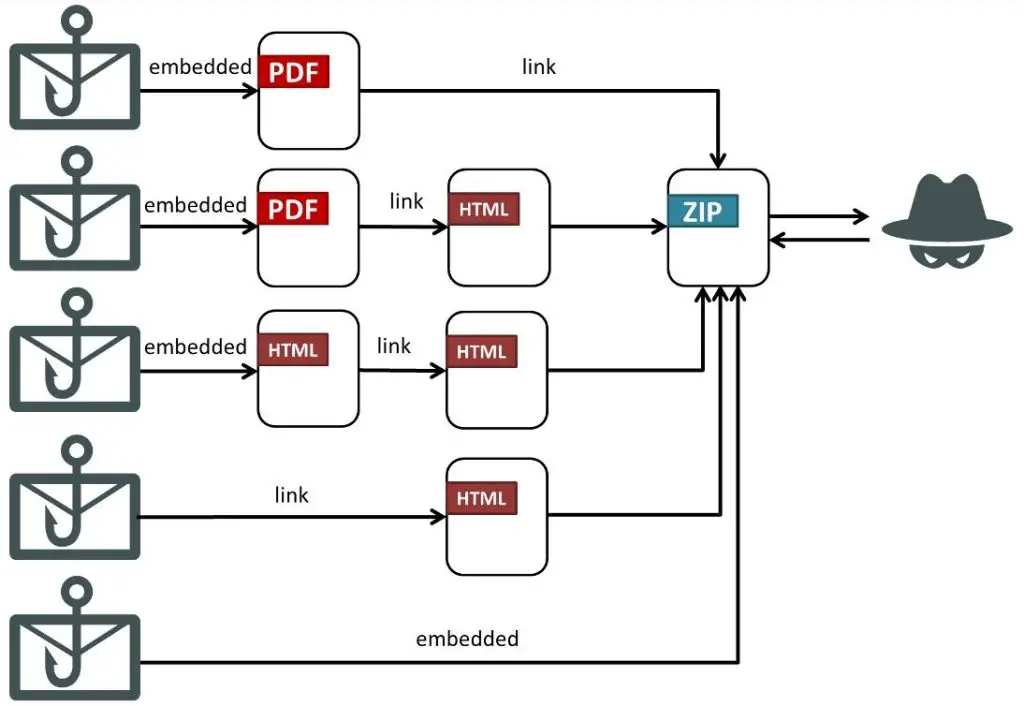
Now, analysts at Fortinet have uncovered new malware samples, confirming that Silver Fox continues its offensive using infected PDF files and ZIP archives delivered via phishing emails.
In most cases, the documents contain an image which, when clicked, initiates the download of a ZIP archive packed with malicious content. These archives typically bundle legitimate executable files with shellcode loaders and encrypted malicious payloads. The infection chain unfolds in multiple stages. Initially, the loader decrypts and executes DLL files, disguising the malware’s behavior as that of benign software. This technique, known as DLL sideloading, enables malicious libraries to be loaded by trusted executables.
The intermediate stages involve evading virtualized environments, detecting analysis tools, and employing privilege escalation techniques. These methods allow the malware to avoid detection and operate at full capacity within the targeted system.
The final phase of the infection culminates in the execution of a file named “msgDb.dat.” This module establishes communication with a command-and-control server, collects victim telemetry, and can download additional components, including tools for file manipulation and remote desktop access.
Fortinet further reports that attackers have begun distributing Gh0stCringe through PDF files that redirect users to HTM-based download pages, where they are enticed to retrieve infected archives. According to researchers, these attack chains are densely layered with fragments of shellcode and multiple loaders, significantly complicating forensic analysis and detection.
Gh0stCringe and HoldingHands are customized variants of the infamous Gh0st RAT remote access trojan, long favored by Chinese-linked hacker groups. The latest Silver Fox APT campaign underscores a persistent trend toward technical evolution and increasingly sophisticated malware delivery mechanisms.


