Hackers are actively targeting outdated TP-Link routers by exploiting a vulnerability first discovered two years ago, which has only recently begun to be weaponized in real-world attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning, adding the flaw to its catalog of known exploited vulnerabilities. Experts are urging users to permanently retire aging models that no longer receive security updates.
The issue concerns a critical command injection vulnerability, tracked as CVE-2023-33538, which carries a CVSS severity score of 8.8. It allows remote attackers to execute arbitrary commands on the device without authentication. The flaw lies in the router’s web management interface: when processing a specific parameter in a GET request, the device fails to properly sanitize user input, enabling the injection of malicious commands.
The risk is especially acute for routers with external exposure—such as those with remote management enabled. However, even without direct internet access, the threat persists within local networks, potentially through compromised laptops or smartphones.
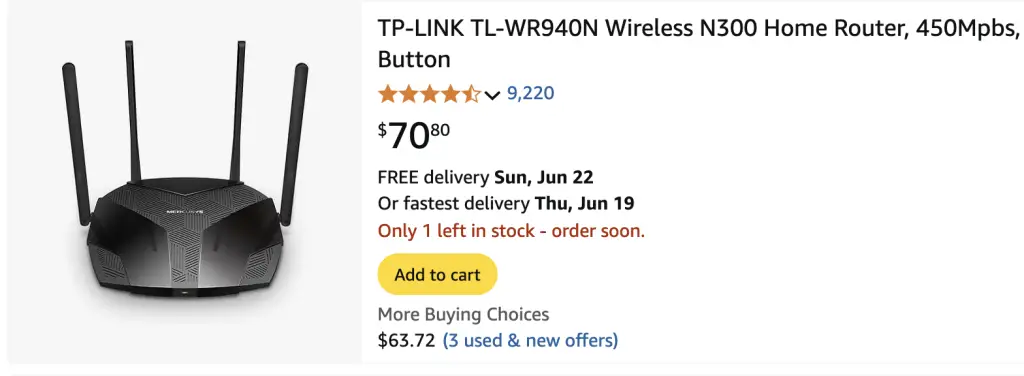
Among the vulnerable devices are several once-popular consumer models. Chief among them is the TP-Link TL-WR940N (versions V2 and V4), which remains available on Amazon, boasting over 9,000 positive reviews. Yet these specific versions have long been considered obsolete—their final firmware updates date back to 2016.
The second affected model is the TP-Link TL-WR841N, specifically versions V8 and V10. The last security update for these was issued in 2015, and the router originally launched in December 2005. Remarkably, it still ranks 165th among “Computer Routers” on Amazon, with more than 77,000 customer reviews. Versions prior to V11 are officially out of support.
The third vulnerable device is the TP-Link TL-WR740N (versions V1 and V2), all revisions of which have reached end-of-life status. The most recent firmware updates for these models were released 15 years ago, leaving them defenseless against modern cyber threats.
According to CISA, the widespread availability of ready-made exploits, combined with the prevalence of these devices, elevates the threat to a critical level. The agency strongly advises users to cease using these outdated routers and replace them with modern alternatives that continue to receive regular updates. U.S. federal agencies are required to remove these models from their infrastructure by July 7, 2025, but the recommendation extends equally to private organizations and individual users.
TP-Link has faced criticism in the past for its sluggish firmware release cycles and ambiguous support policies. The issue is systemic—many older models remain on the market with new hardware revisions but lack clear documentation about version differences or support timelines. As a result, consumers may unknowingly purchase hardware that is already vulnerable to current threats.
The TP-Link case is a stark reminder of how obsolete yet widely available consumer-grade devices can become a weak link in digital security. Given the severity of the risks, CISA’s call to retire these models should be seen not merely as technical advice, but as a vital measure for safeguarding personal data and the integrity of network infrastructures.


