In recent times, cybercriminals have increasingly shifted their focus from deploying malware to employing subtle manipulations rooted in the art of social engineering. Their latest targets: the developers themselves. Experts at Praetorian have observed a new wave of attacks wherein threat actors exploit a legitimate GitHub authorization mechanism — the OAuth 2.0 Device Code Flow. Originally designed to facilitate login on devices with limited input capabilities, this protocol has now become a convenient backdoor for stealing access tokens.
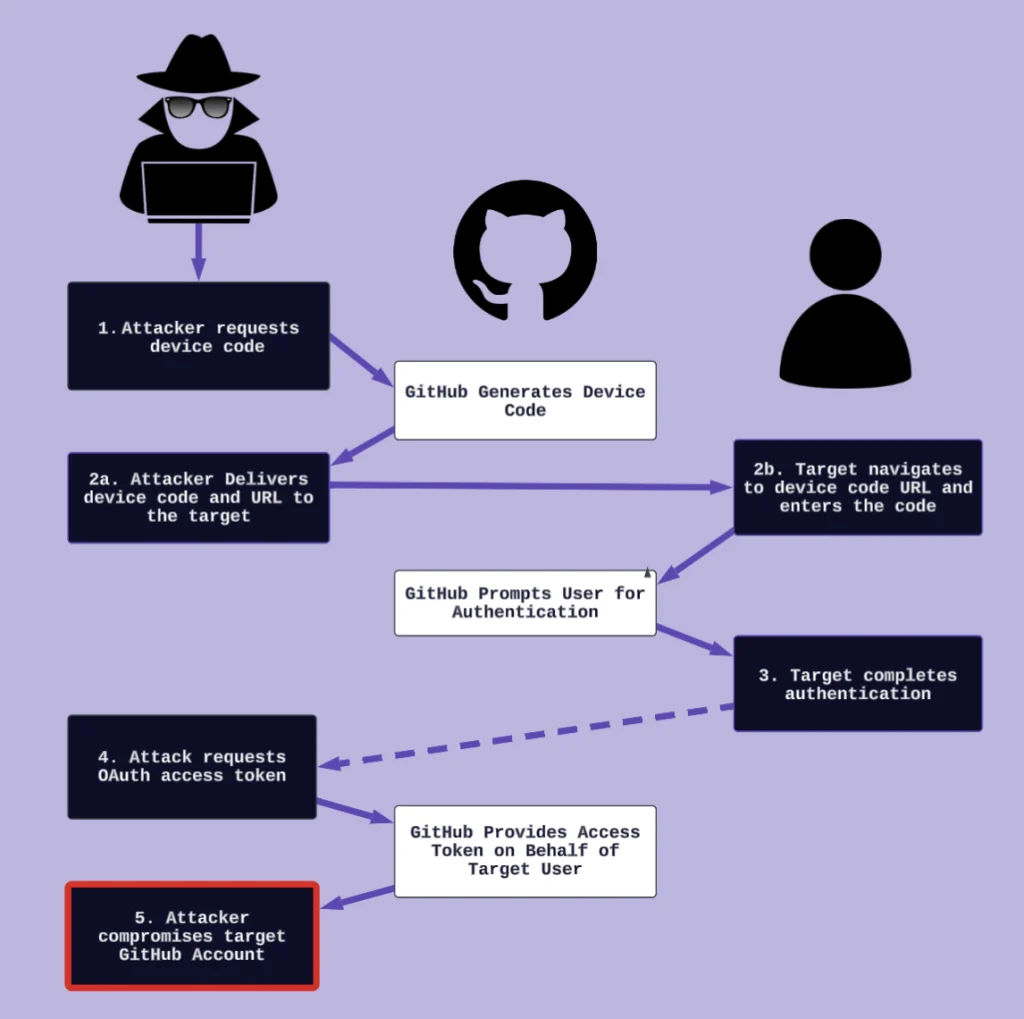
The essence of the attack lies in obtaining a temporary device code via the GitHub API and passing it to a developer while impersonating technical support or an internal administrator. The moment an unsuspecting employee enters the code at the provided link, the trap is sprung: the attacker acquires a fully privileged OAuth token, gaining access to private repositories, CI/CD environments, and the company’s most sensitive secrets.
This approach is particularly insidious because it preys on trust and plausibility. GitHub does not verify whether the entity initiating the code request is the same as the one confirming it. As a result, anyone can trigger the process, and a deceived user can unwittingly authorize it.
The attack unfolds as follows:
- The adversary initiates a device code request with specific privileges — such as access to user data, repositories, and workflow configurations.
- The code and authentication link are sent to a company employee via email, phone, or SMS, under the guise of tech support.
- The victim enters the code on GitHub’s authorization page, unknowingly granting full access.
- The attacker receives an OAuth token with elevated permissions.
- This token enables the theft of source code, insertion of malicious changes, exposure of secrets, and even the launching of supply-chain attacks.
In one incident, threat actors gained internal access and began auto-generating device codes, inserting them into fraudulent phone interactions. In another case, a tool dubbed GitPhish was deployed — automatically creating valid codes through a fake GitHub Pages site, presenting users with a convincing interface and a live authorization code.
What exacerbates the situation is that this form of authorization cannot be disabled in GitHub. Thus, all efforts must turn toward mitigation. Experts recommend the following countermeasures:
- Event Log Analysis: Monitor
org_credential_authorization.grantevents, scrutinizing their frequency and scopes, especially when repeated across multiple users. - Network Traffic Surveillance: Detect unusual spikes in traffic to
github.com/login/device, which may indicate an ongoing phishing campaign. - IP Whitelisting: Apply allow-listing policies at the corporate level, while carefully considering the potential impact on CI/CD workflows.
- Post-Authorization Behavior Monitoring: Watch for abrupt increases in repository cloning, secret scanning, or other atypical activity following the issuance of a new token.
Given the escalating frequency of such attacks, it is crucial to establish rapid response protocols and raise internal awareness. In today’s digital landscape, the most dangerous threat may not come from the outside — but from within the very walls of your GitHub account.


