Hackers have compromised tens of thousands of corporate Microsoft Entra ID accounts by exploiting a tool originally designed for security professionals. The campaign, codenamed UNK_SneakyStrike, began in December 2024 and reached its peak during the first half of 2025, affecting more than 80,000 user accounts across hundreds of Microsoft cloud tenants. Tens of thousands of login attempts were recorded from suspicious IP addresses, many of which culminated in successful account takeovers.
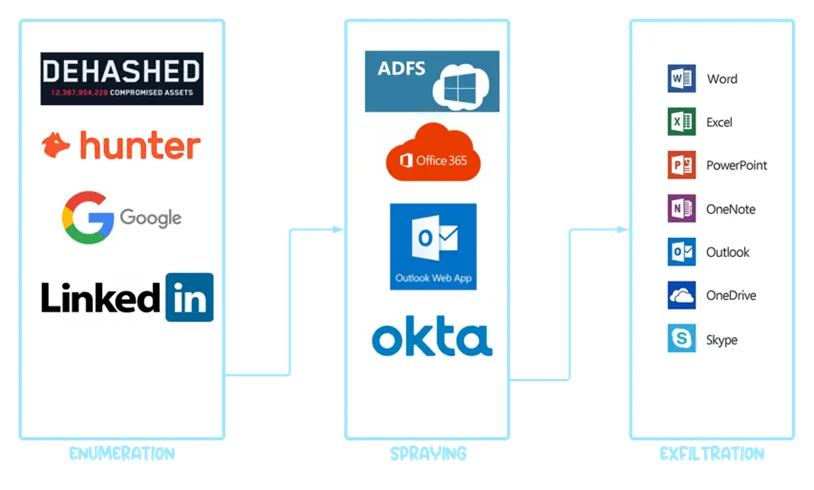
At the heart of the operation lies the open-source framework TeamFiltration, first introduced at DEF CON in August 2022. Though initially intended as a legitimate utility for testing the resilience of Microsoft Entra ID (formerly Azure Active Directory), it was swiftly co-opted by malicious actors. The tool’s capabilities include user enumeration, password spraying, data exfiltration, and persistent access through the injection of malicious payloads into OneDrive.
According to Proofpoint, the attackers leveraged the Microsoft Teams API and Amazon Web Services infrastructure to orchestrate the campaign globally. This geographic distribution of attack origins enabled them to bypass traditional IP-based filtering. The largest share of malicious activity was traced to the United States (42%), followed by Ireland (11%) and the United Kingdom (8%).
The attacks were carried out in calculated waves: large-scale brute-force attempts targeted the user accounts within a single cloud organization, followed by a lull lasting four to five days. This pattern indicates a high level of automation and fine-tuning, designed to minimize the likelihood of detection.
A notable feature of UNK_SneakyStrike’s methodology lies in its tailored approach: while small organizations were targeted indiscriminately, larger enterprises saw only selective attacks on specific employees. This strategic prioritization stems from TeamFiltration’s ability to filter out low-value targets and focus on accounts with elevated privileges or access to sensitive data.
Although TeamFiltration requires valid AWS and Microsoft 365 credentials to unlock its full functionality, observed attacks often relied on disposable or spoofed accounts, complicating efforts to trace or disrupt operations.
The weaponization of a framework developed for penetration testing once again highlights the double-edged nature of open-source security tools. In the wrong hands, even tools created for defense can be repurposed to facilitate offensive campaigns.
While the identities behind UNK_SneakyStrike remain unknown, the scale, precision, and infrastructure agility suggest a highly skilled group with a deep understanding of Microsoft’s cloud ecosystem. The campaign exhibited systematic tactics, dynamically switching between outbound servers and adapting techniques in real time.
Organizations leveraging Entra ID and Microsoft cloud services are strongly urged to bolster surveillance of anomalous activity, restrict Teams API access, scrutinize login logs for unusual geographies, and tighten external access to OneDrive and Outlook. Special attention should be paid to geographically dispersed IP patterns and wave-like brute-force activity.


