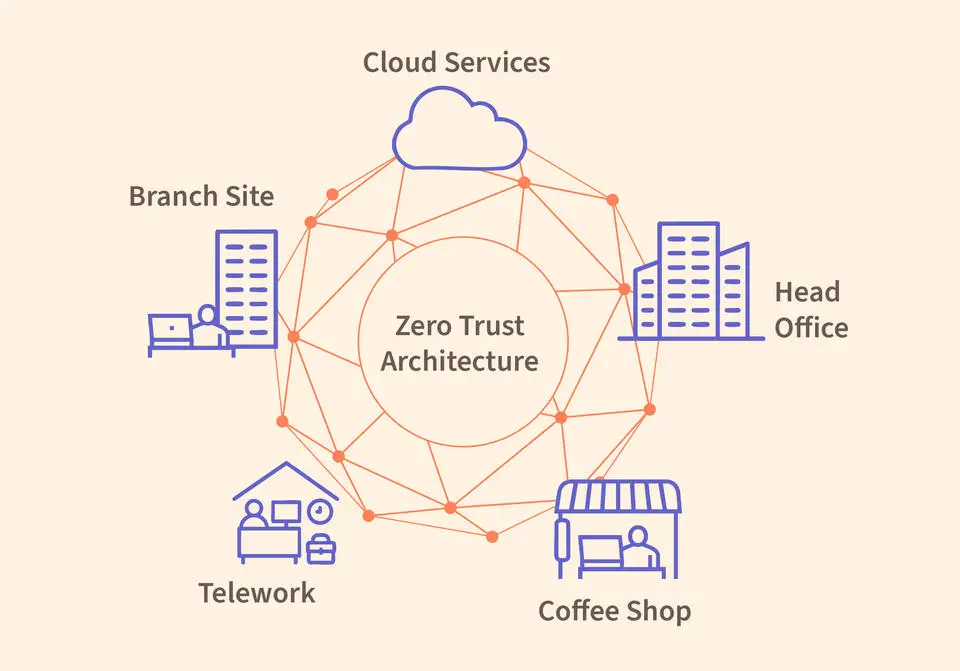
Traditional models for securing corporate networks are no longer adequate in the face of modern realities. In the past, placing all servers within a single data center, restricting external access, and monitoring inbound traffic was sufficient. Yet, the era when digital assets resided solely within a localized infrastructure is swiftly drawing to a close. Today, employees connect from different cities—logging in from cafés, apartments, or coworking spaces—while mission-critical services operate across various cloud environments.
In response, the security paradigm is shifting toward Zero Trust Architecture (ZTA), whose core tenet is radical skepticism: trust is never assumed based on location, IP address, or prior authentication. Every request—regardless of origin—is treated as potentially hostile. For those new to this philosophy, a natural question arises: where does one begin, and how can such a framework be implemented within the constraints of real-world business?
The U.S. National Institute of Standards and Technology (NIST) has sought to answer this question through its comprehensive guide, Implementing a Zero Trust Architecture (SP 1800-35). The document is the culmination of a multi-year initiative led by NIST’s National Cybersecurity Center of Excellence (NCCoE) and presents 19 fully developed implementation scenarios. Each is grounded in commercially available technologies, thoroughly tested, and enriched with insights from 24 participating industry partners.
Unlike its predecessor, NIST SP 800-207 (published in 2020), which focused primarily on theory—defining conceptual models and logical components—the new publication is firmly rooted in practice. It explores the mechanics of deploying Zero Trust solutions using existing technologies, serving as both a technical manual and a strategic guide for navigating the complexity of today’s IT environments.
For years, security operated under a simple principle: once inside the network, a user was inherently trusted.
Zero Trust turns this logic on its head. Instead of relying on perimeter-based defenses, it embraces a dynamic model in which every request is evaluated in real time against a multitude of factors—ranging from user context to device characteristics. Even if an intruder breaches the network, lateral movement is severely constrained. Every action requires explicit authorization and is meticulously monitored. This approach safeguards against both external threats and internal risks such as compromised accounts or endpoints.
Transitioning to such an architecture requires more than implementing new tools—it demands a fundamental reevaluation of access control principles. Organizations must understand who is requesting access, why, from where, and at what time. Yet each enterprise is different, with its own array of services, vulnerabilities, constraints, and business processes.
The documented use cases span a broad spectrum—from multi-cloud networks and on-premise office infrastructures to employees connecting via public Wi-Fi. Each example has been rigorously tested: the NCCoE team, in collaboration with industry stakeholders, spent four years deploying software, fine-tuning configurations, resolving conflicts, and measuring performance.
The technologies referenced in the guide are commercially available and widely adopted, but their inclusion does not constitute endorsement by NIST. The goal is not to promote specific vendors, but to demonstrate that robust Zero Trust environments can be built using readily accessible tools.
Special emphasis is placed on practical application—how to address authentication, segmentation, monitoring, and policy management challenges during implementation.
A particularly valuable aspect of the document is its accessibility to various organizational roles. It offers actionable guidance not only to technical experts, but also to system architects, cybersecurity managers, administrators, and IT leaders responsible for shaping long-term infrastructure strategies. It may serve as a reference manual, a development blueprint, or even a source of inspiration for crafting bespoke security solutions.
Rather than prescribing a one-size-fits-all solution, the authors provide a versatile toolkit to help organizations tailor their Zero Trust architecture to specific needs and risk profiles. For enterprises embarking on this transformation, it is arguably the most comprehensive and practical guide available in recent years.


