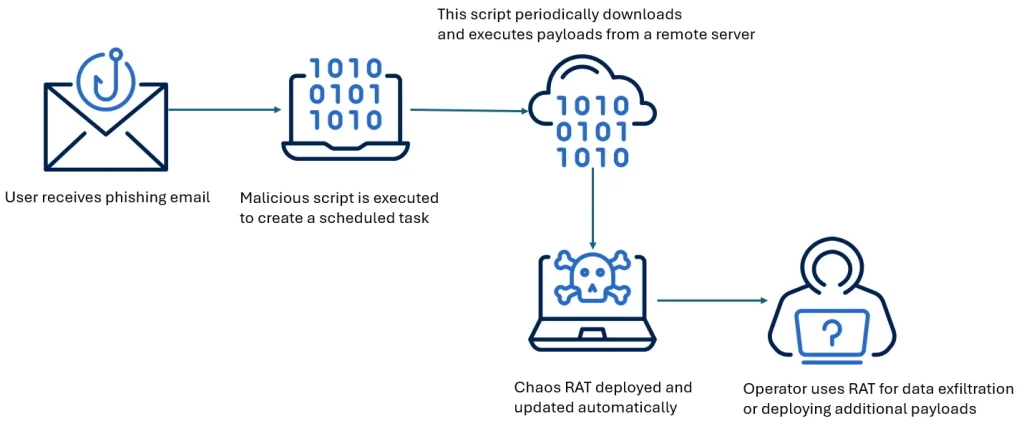
Amid a surge in cybercriminal activity, security experts have turned their attention to a new iteration of the Chaos RAT remote trojan—capable of infecting both Windows and Linux systems. According to Acronis, the malware is being distributed under the guise of a legitimate network diagnostic tool for Linux environments. Unsuspecting victims are lured into downloading a file named “NetworkAnalyzer.tar.gz,” unaware of the threat it conceals.
Chaos RAT is a cross-platform remote access tool written in Go, inspired by offensive security frameworks like Cobalt Strike and Sliver. It comes equipped with a web-based administrative panel that enables attackers to craft payloads, manage compromised machines, initiate sessions, and execute arbitrary commands. Its feature set includes reverse shells, file upload and deletion, screenshot capture, system information gathering, device locking and rebooting, as well as the ability to open arbitrary URLs.
Although the development of Chaos RAT dates back to 2017, it only drew significant attention in December 2022, when it was first observed in attacks targeting public-facing Linux web applications, often used to deploy the XMRig cryptominer. The current version, 5.0.3, was released on May 31, 2024, and is actively leveraged in real-world attacks.
Acronis researchers have identified multiple Linux infections where Chaos RAT was delivered via phishing emails containing malicious attachments or embedded links. In several instances, the malicious script automatically modified the system’s task scheduler by altering the /etc/crontab file, thereby ensuring persistent access and the ability to relaunch the trojan.
Earlier incidents suggested that Chaos RAT and cryptominers were deployed separately—indicating that the trojan was initially employed for reconnaissance and information gathering rather than immediate monetization. However, its current masquerade as a network utility suggests a shift in tactics, aiming to build trust and avoid detection.
Of particular note is a critical flaw discovered in Chaos RAT’s command-and-control panel: a command injection vulnerability, CVE-2024-30850, with a CVSS score of 8.8, and an XSS vulnerability, CVE-2024-31839, rated at 4.8. Together, these flaws allowed adversaries to execute arbitrary code on the server with elevated privileges. Both vulnerabilities were patched by the project’s author in May 2024.
Though attribution remains inconclusive, the report underscores a broader trend: open-source tools are increasingly repurposed as convenient foundations for cyberattacks, complicating efforts to trace their origins. When identical source code is employed by multiple threat groups, pinpointing the responsible actors becomes virtually impossible. Open-source malware offers “good enough” solutions—easily modified, rapidly deployed, and requiring no ground-up development.
Concurrently, researchers at Point Wild have observed a similar wave of attacks targeting Trust Wallet users. Threat actors distribute counterfeit desktop applications via phishing campaigns, fraudulent websites, and bundled software packages. Their primary objective is to harvest browser credentials, intercept wallet data, and extract seed phrases and private keys. The malware used in these operations may function as a clipboard hijacker—replacing copied data—or perform real-time analysis of browser content.


