Critical security flaws have once again been discovered in popular vBulletin forums—vulnerabilities that allow for arbitrary code execution directly on the server, without the need for login credentials. These include two severe exploits, identified as CVE-2025-48827 and CVE-2025-48828. The former is already being weaponized in real-world attacks, while the latter can be chained with it to achieve full system compromise.
The vulnerabilities were uncovered on May 23, 2025, by independent security researcher Egidio Romano (EgiX), who published a detailed technical breakdown of the exploitation mechanisms. At the heart of the issue lie changes introduced in PHP beginning with version 8.1, coupled with logical flaws in vBulletin’s templating engine. Together, they produce a dangerous result: remote, unauthenticated execution of arbitrary commands on the server.
The first flaw stems from improper use of the Reflection API. This API permits invocation of protected methods within objects and previously required deliberate bypasses for access. However, in PHP 8.1, certain reflective calls no longer require such explicit overrides. If unaccounted for in the codebase, these methods can now be invoked directly—no circumvention needed.
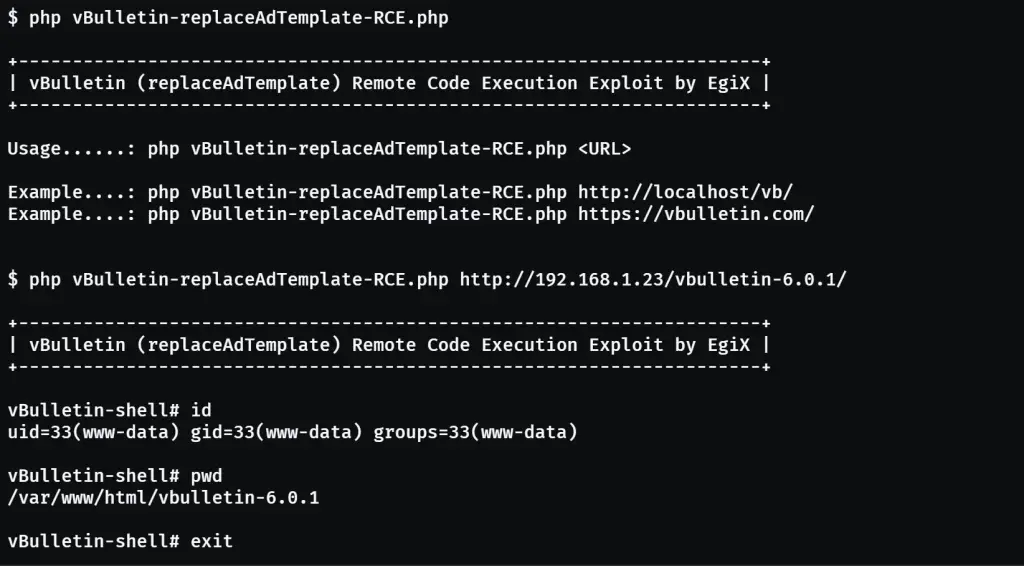
vBulletin contains multiple instances of such calls. For example, the vulnerable replaceAdTemplate method allows for specially crafted templates to be injected directly via URL requests. CVE-2025-48828 bypasses unsafe function filtering using PHP tricks such as invoking variables as functions (e.g., ${'assert'}). As a result, malicious payloads are accepted as valid input by the system.
The combination of these flaws forms a potent vector: a single request is sufficient to inject and execute arbitrary commands on the server, typically under the www-data user on Linux. This paves the way for downloading backdoors, executing malicious scripts, and deepening system intrusion.
Just three days after Romano’s publication, on May 26, another researcher—Ryan Dewhurst—observed real-world exploitation attempts. Upon analyzing his honeypot logs, he detected suspicious requests targeting the vulnerable endpoint /ajax/api/ad/replaceAdTemplate. Indicators pointed to scanning and exploitation attempts involving malicious PHP uploads.
One attacker was traced back to IP addresses registered in Poland. The requests revealed an effort to upload a remote web shell, granting persistent access and enabling command execution through a browser interface.
So far, attacks have only leveraged CVE-2025-48827, but the published exploit chain clearly anticipates eventual use of the second flaw. All components are already in place, including a public proof-of-concept and pre-built templates for automated scanners such as Nuclei—available as early as May 24. In essence, the attack vector is fully weaponized and ready for deployment.
Of particular concern is the vast scope of affected versions. These bugs impact not only the latest releases, but every version from vBulletin 5.0.0 to 5.7.5 and from 6.0.0 to 6.0.3, provided the environment runs PHP 8.1 or newer. Although patches were released last year—Patch Level 3 for version 5.7.5 and Patch Level 1 for all 6.x versions—they were issued without broad announcements, leaving many administrators unaware of the critical nature of the update.
As a result, a substantial number of forums remain vulnerable. Even those running the latest major versions but neglecting minor patches are exposed—especially high-traffic sites, where exploitation could lead to user data theft, content tampering, and total site compromise.
vBulletin remains one of the most widely used PHP/MySQL forum engines, powering thousands of websites globally. Its modular architecture and support for mobile APIs make it suitable for both niche communities and large-scale commercial platforms. Yet this flexibility also results in a broad attack surface, reaffirming the necessity of regularly updating even seemingly innocuous components.
vBulletin has previously been the target of high-profile breaches. Past vulnerabilities allowed attackers to access databases, serve malicious advertisements, and use the platform as a stepping stone into larger systems. The current flaws belong to that same dangerous class: simple to exploit, yet devastating in the hands of a capable adversary.
Developers urge forum administrators to urgently apply the security patches and, where feasible, migrate to vBulletin version 6.1.1, where these vulnerabilities have been fully resolved. Failure to do so leaves sites exposed to attacks via templates, APIs, and core-level weaknesses.


