The U.S. National Institute of Standards and Technology (NIST) has introduced a new methodology for assessing the likelihood of vulnerability exploitation in software and hardware systems. On May 19, 2025, NIST unveiled the Likely Exploited Vulnerabilities (LEV) equation—a model designed to evaluate how probable it is that a given vulnerability has been or will be exploited by malicious actors, even in the absence of confirmed incidents.
This new metric aims to complement existing prioritization tools, such as the Known Exploited Vulnerabilities (KEV) catalog maintained by the Cybersecurity and Infrastructure Security Agency (CISA). The overarching goal is to enhance risk assessment capabilities in scenarios where exploitation has not yet been observed but appears plausible.
The LEV equation is the result of a collaborative effort between former NIST researcher Peter Mell and CISA analyst Jonathan Spring. Details are outlined in an official NIST technical paper, which emphasizes that while tens of thousands of vulnerabilities are published annually, only a small fraction are actively exploited. LEV seeks to help security professionals focus their attention on those with the highest threat potential.
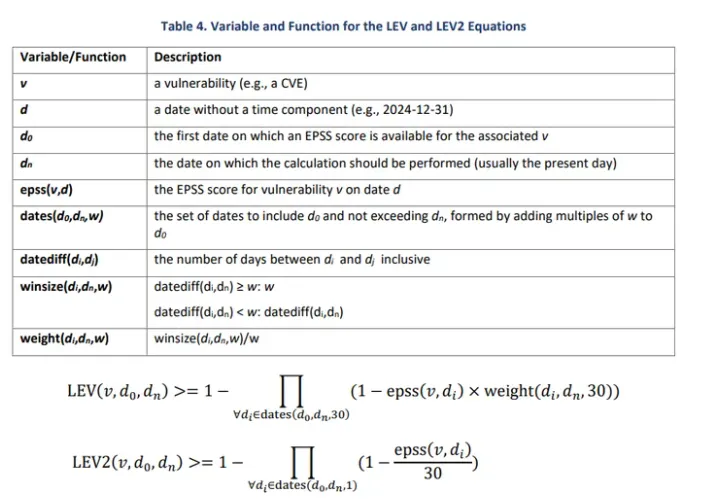
According to the authors, existing systems such as the Exploit Prediction Scoring System (EPSS) have limitations in precision and coverage. The LEV equation is intended to address some of these shortcomings by incorporating EPSS scores as input, while also analyzing the likelihood of exploitation within 30 days of public disclosure. Additional factors—such as publication dates and specific characteristics of each vulnerability—are also taken into account.
Two variants of the equation have been developed: a foundational version (LEV) and a more resource-intensive model (LEV2), designed for the routine automated assessment of large-scale vulnerability datasets. The authors note that even LEV2 can be run daily on a standard laptop.
Industry experts have greeted the innovation with a mixture of intrigue and caution. Dustin Childs, Head of Threat Analysis at the Zero Day Initiative (Trend Micro), remarked that the new approach could dramatically improve the speed of security teams’ responses: “If professionals have a tool to gauge the likelihood of exploitation, it could be a game-changer.”
However, skepticism remains. Katie Moussouris, founder of Luta Security, warned that reducing such a complex issue to a mathematical formula risks oversimplifying reality. In her view, not all vulnerabilities are equal in value or attractiveness to attackers, even if they appear similar on paper.
Casey Ellis, founder of Bugcrowd, acknowledged the promise of the idea but stressed that its implementation will be critical: “Teams need clear, actionable intelligence—not just another signal.” Paul Mote, Vice President of Solutions Architecture at Synack, added that LEV may help bridge the gap between the KEV catalog and the remaining 99% of CVE entries that often go overlooked.
In this light, the LEV equation emerges as a significant new component in the vulnerability assessment ecosystem—not as a replacement for existing frameworks, but as a refined instrument to enhance precision and timeliness in threat response.


