Image: Infoblox
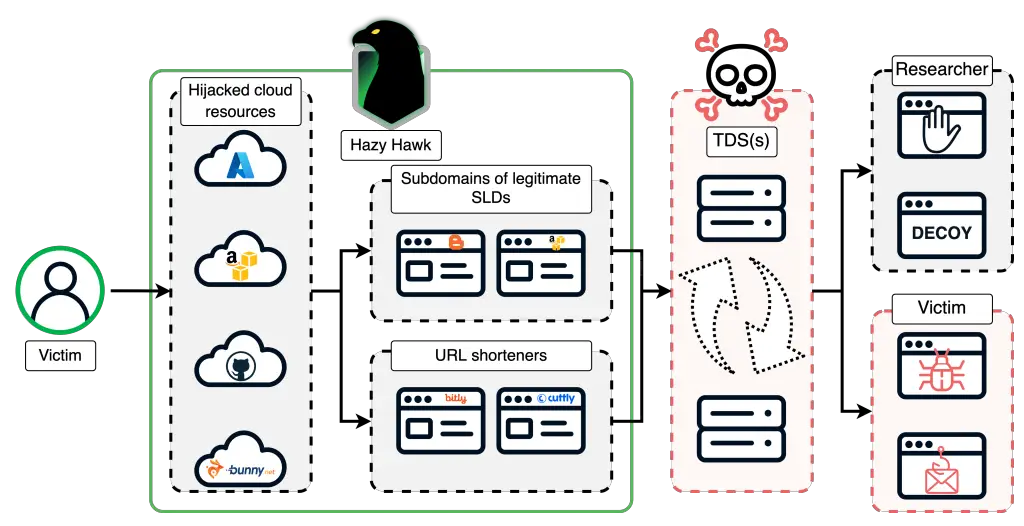
A threat actor known as Hazy Hawk has launched a widespread campaign to seize abandoned cloud assets belonging to major organizations, including Amazon S3 and Microsoft Azure, by exploiting misconfigured DNS records. Their reach has also extended to platforms hosted on Akamai, Cloudflare CDN, GitHub, Netlify, and other prominent services. According to researchers at Infoblox, domains and subdomains once owned by reputable entities have been repurposed as entry points for fraudulent schemes and malicious operations.
The group’s activity was first detected in February 2025, when Hazy Hawk took control of several subdomains associated with the U.S. Centers for Disease Control and Prevention (CDC). However, deeper analysis revealed that the campaign had already begun in December 2023 and had affected not only American government agencies but also global corporations such as Deloitte, PwC, and Ernst & Young, as well as prestigious academic institutions.
At the heart of the attack lies a deceptively simple tactic: the hijacking of CNAME DNS records that point to decommissioned or deleted cloud resources. By registering the missing component, attackers effectively seize control of the domain. This method allows them to swap legitimate content with malicious pages while retaining the trust of search engines and browsers—thanks to the domain’s original, reputable lineage.
Hazy Hawk’s infrastructure is cloaked behind innocuous redirects or seemingly legitimate websites, sometimes replicating original content in full. But the ultimate aim is to funnel users into a chain of redirects via Traffic Distribution Systems (TDS), leading them to sites laden with pornography, pirated software, and fraudulent surveys. Special emphasis is placed on convincing users to enable push notifications, which are later exploited to deliver an unending stream of malicious content.
Interestingly, despite infrastructure that echoes state-level cyber-espionage, Hazy Hawk’s motives appear purely commercial—deeply entrenched in the murky world of underground advertising and affiliate monetization. Each user interaction with a rogue ad generates revenue for affiliates, making the operation financially lucrative. According to Infoblox, domain hijacking may even be offered as a standalone service to other groups engaged in malvertising campaigns.
Experts emphasize the critical importance of promptly removing CNAME records when cloud assets are retired. Failure to do so—even by large enterprises—can turn once-trusted domains into silent conduits for malicious messaging and user manipulation. For everyday users, the recommendation is clear: never accept push notifications from unfamiliar websites, as doing so risks opening the floodgates to invasive and hazardous content.
Hazy Hawk serves as a vivid illustration of how vulnerable forgotten domains remain, even when they once belonged to the world’s most prominent institutions. As long as dark web ad networks remain profitable, such attacks are likely to proliferate in both scale and sophistication.


