For over eight months, a cybercriminal group has been distributing trojanized versions of the KeePass password manager, exploiting them to deploy Cobalt Strike, steal credentials, and ultimately launch ransomware attacks within corporate networks. The campaign was uncovered by WithSecure during an investigation into a ransomware incident in which the victim organization lost access to its VMware ESXi servers.
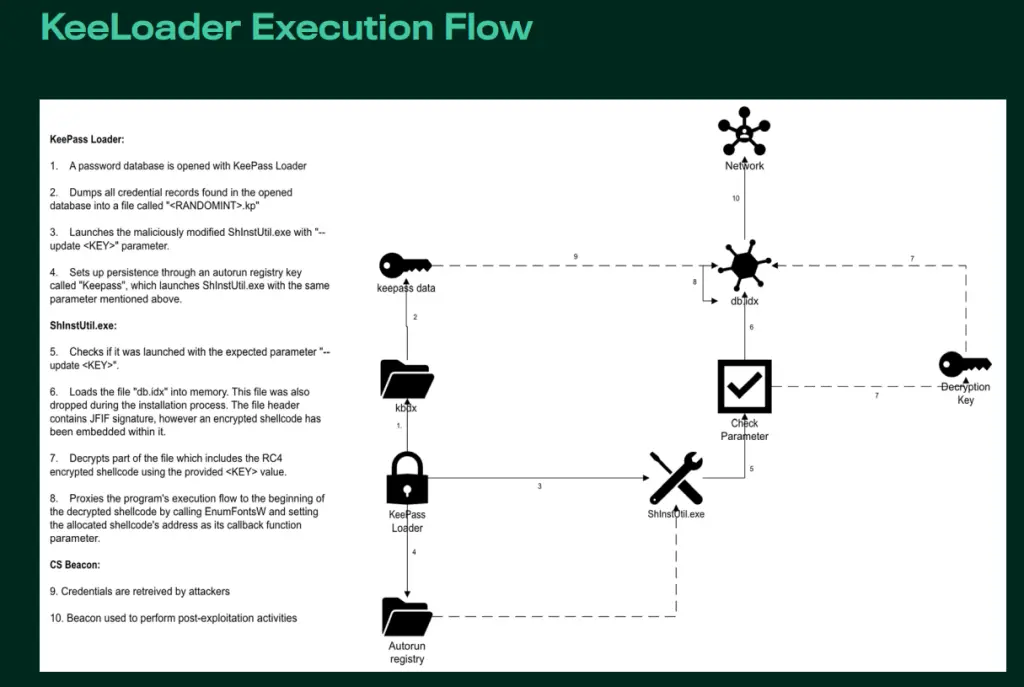
The attack began with a malicious KeePass installer delivered through Bing advertisements that redirected users to spoofed websites. As an open-source project, KeePass allowed attackers to alter its source code, embedding malicious functionality into a working build of the application. This modified version, dubbed KeeLoader, retained KeePass’s familiar interface while silently installing a Cobalt Strike Beacon—used for persistent access and command-and-control. Simultaneously, it exfiltrated the user’s entire KeePass password database in plaintext via the same Beacon.
According to WithSecure’s report, the campaign utilized a distinctive watermark—a unique identifier embedded in the Beacon binary, tied to a specific Cobalt Strike license. This watermark had previously been observed in operations attributed to the Black Basta group, known for deploying ransomware and collaborating with Initial Access Brokers (IABs). In this case, the campaign’s distribution of KeeLoader is believed to have been orchestrated by such a broker.
In addition to stealing passwords, the tampered software exported other database contents—logins, URLs, and user comments—into a CSV file with a .kp extension, stored within the %localappdata% directory. The file name was a random number between 100 and 999. These records were likewise sent to the attackers, granting full access to the victim’s online accounts.
Notably, investigators discovered multiple KeeLoader variants signed with legitimate digital certificates. Distribution relied on cleverly crafted lookalike domains such as keeppaswrd[.]com, keegass[.]com, and KeePass[.]me. Some of these domains—keeppaswrd[.]com among them—remain active and continue to distribute malicious KeePass builds, as confirmed by VirusTotal scans.
The attackers’ infrastructure was extensive. They created counterfeit landing pages mimicking popular services including WinSCP, Phantom Wallet, Sallie Mae, and DEX Screener. These pages were used to disseminate other malware variants or harvest user credentials. A central domain used in the campaign—aenys[.]com—hosted numerous subdomains for these fake portals.
WithSecure analysts attribute this activity to UNC4696, a threat group previously associated with the Nitrogen Loader campaign, itself linked to the operators behind the BlackCat/ALPHV ransomware.
This campaign serves as a sobering reminder that even seemingly legitimate domains advertised online cannot be blindly trusted. Threat actors continue to circumvent ad network policies by masking malicious redirects with authentic-looking URLs. As such, downloading critical software like password managers must always be done through verified, official sources—never via advertisement links.


