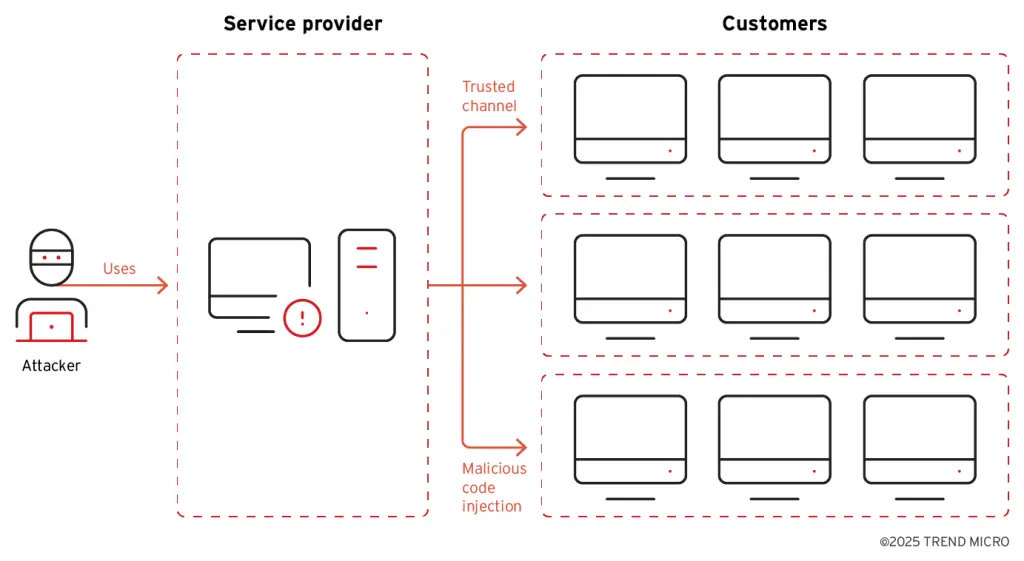
The campaign TIDRONE compromised the victim through a supply chain attack from the service provider or upstream vendor
The group known as Earth Ammit, affiliated with Chinese-speaking APT entities, conducted two waves of targeted attacks during 2023–2024. The first campaign, codenamed VENOM, focused on software service providers, while the second—TIDRONE—targeted defense industry enterprises. Both operations were rooted in supply chain compromise tactics: VENOM infiltrated the upper tiers of the drone ecosystem, while TIDRONE targeted vendors of military and satellite technologies.
In its early phase, Earth Ammit relied on freely available tools to minimize operational costs and hinder attribution. However, during TIDRONE, the group transitioned to proprietary malware—namely the CXCLNT and CLNTEND backdoors—enabling more covert and selective espionage operations.
The primary victims were organizations based in Taiwan and South Korea. Targets included drone suppliers, media outlets, technology and software firms, heavy industry manufacturers, as well as companies in the satellite and healthcare sectors. Earth Ammit’s overarching strategy was to infiltrate trusted supply chains as a means of reaching high-value end clients.
The investigation into TIDRONE, conducted in July 2024, revealed overlapping enterprise resource planning (ERP) software among multiple victims. This led researchers to uncover the earlier VENOM campaign. The findings were formally presented at Black Hat Asia 2025.
VENOM employed conventional tactics: attackers exploited vulnerable web servers to plant web shells, then used open-source proxies and RAT tools to establish persistence. The primary goal was to exfiltrate NTDS files and compromise downstream systems, laying the groundwork for the subsequent TIDRONE campaign.
TIDRONE unfolded in three phases. The first involved attacking through compromised suppliers and distributing tainted software via trusted channels. The second phase entailed the deployment of backdoors, particularly CXCLNT and CLNTEND, which were injected into system processes, bypassed UAC, and escalated privileges. The final phase consisted of data extraction—password dumps, screenshot capture, antivirus disabling, and installation of data collection tools.
A notable hallmark of TIDRONE was its extensive use of fiber-based techniques, including SwitchToFiber, FlsAlloc, and exception handling strategies—methods that greatly complicate detection and analysis. These techniques emerged concurrently with research presentations at Black Hat USA and Asia, suggesting the attackers may have drawn direct inspiration from these talks.
CXCLNT operated entirely in memory, left no disk artifacts, used SSL and HTTPS for communication, and dynamically loaded modules from a C2 server as needed. CLNTEND represented its logical evolution—supporting seven communication protocols (including WebSocket and SMB), implemented as a DLL capable of running in both client and server modes. It achieved stealth by injecting into dllhost.exe and spawning a command shell under winword.exe, thereby evading security controls and executing commands undetected.
Researchers also uncovered ScreenCap, a surveillance trojan embedded through CLNTEND that exfiltrated periodic screenshots to the operators.
Two key indicators linked the VENOM and TIDRONE campaigns: overlapping victimology and identical C2 infrastructure, including a domain with the telling name fuckeveryday[.]life—a clear sign that the same group was behind both operations. Attribution points to a Chinese-speaking threat actor. File and command timestamps correspond to the GMT+8 timezone, and the group’s methods bear striking resemblance to those of Dalbit, previously profiled by AhnLab.
To defend against such threats, organizations are advised to implement third-party risk management practices, verify software integrity via SBOM, monitor API calls, segment supplier-facing systems, adopt Zero Trust architectures, and strengthen behavioral analytics and EDR capabilities.


