The North Korean hacking group Konni—also known as Opal Sleet and TA406—which maintains ties to the DPRK government, has been observed targeting Ukrainian governmental institutions in an espionage campaign aimed at gathering intelligence. According to researchers at Proofpoint, the operation began in February 2025.
The attackers employ phishing emails, posing as analysts from fictitious think tanks and referencing recent political developments or shifts in Ukraine’s military leadership. Message subjects range from the resignation of senior military officials to upcoming presidential elections. Publicly available email platforms such as Gmail, ProtonMail, and Outlook are used to disseminate these messages at scale, enticing recipients to follow embedded links.
These links direct users to the cloud storage platform MEGA, where they are prompted to download a password-protected archive titled Analytical Report.rar. Inside lies a CHM file which, when opened, executes an embedded PowerShell script. This script initiates the second stage of the attack by downloading an additional PowerShell payload that harvests device information and establishes persistence within the system.
In alternative variants, the attackers utilize HTML attachments to deliver ZIP archives containing seemingly benign PDF documents alongside malicious LNK shortcuts. These shortcuts execute either PowerShell or VBScript commands with embedded, encrypted code. According to researchers, the final payload is believed to be a surveillance-focused backdoor, although its precise functionality has not yet been fully extracted.
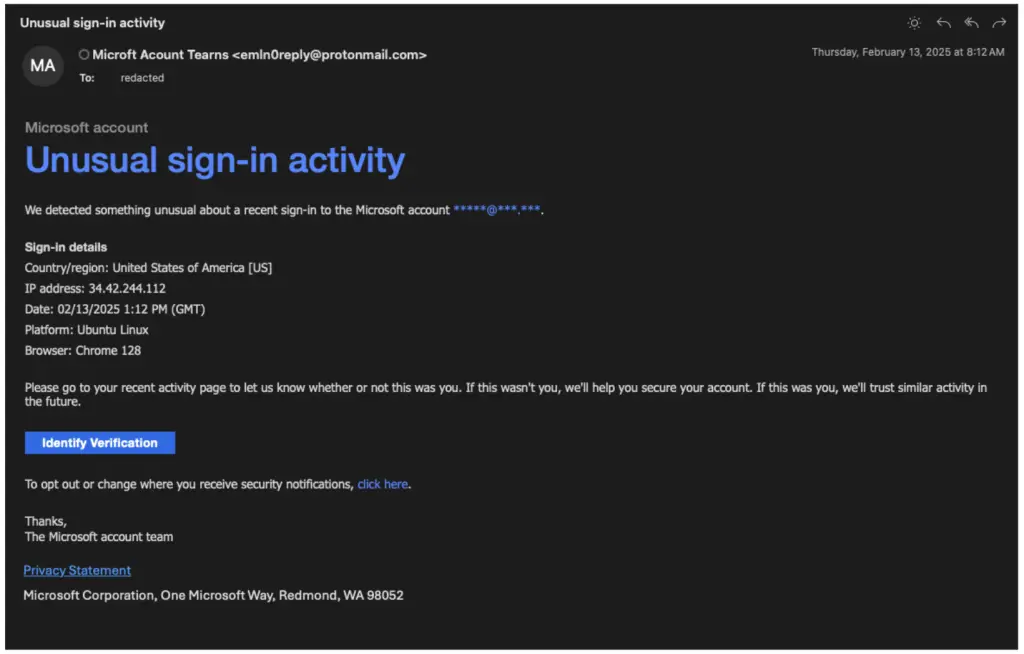
In parallel to the core campaign, Konni has also conducted preparatory operations aimed at account credential theft. These efforts involved fake security alerts allegedly from Microsoft, warning of “unusual sign-in activity.” Targets were instructed to verify their accounts on a phishing site, jetmf[.]com, thereby unwittingly surrendering their credentials.
Konni’s recent activity signals a heightened North Korean interest in the evolving situation in Ukraine. Proofpoint analysts believe the objective is to gauge internal sentiment within Ukrainian state institutions and to assess any emerging threats to North Korean military interests.
North Korea’s cyber involvement in this ongoing conflict adds further complexity to an already volatile digital landscape. These actions underscore the international scope of modern cyber operations, which unfold in tandem with other forms of geopolitical pressure.


