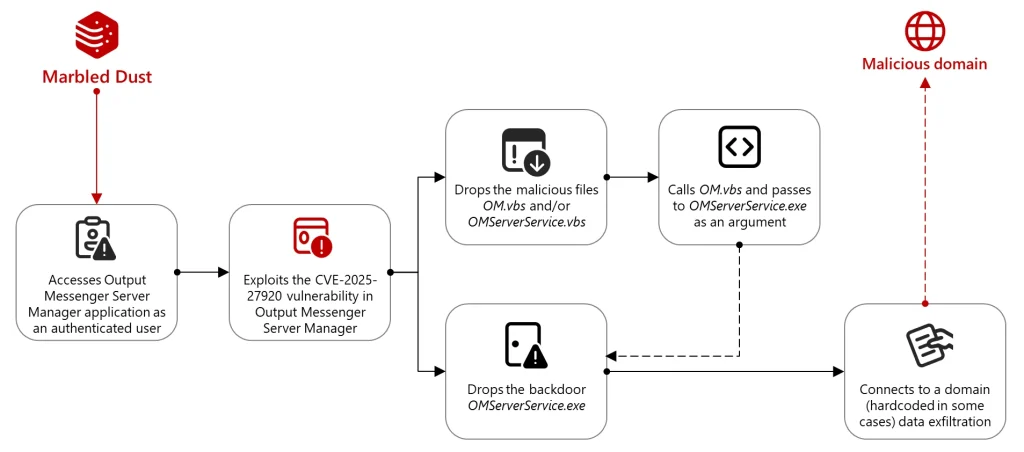
The Marbled Dust attack chain
The APT group known as Marbled Dust, believed to be affiliated with the Turkish government, has orchestrated a sophisticated espionage campaign targeting users of Output Messenger by exploiting a zero-day vulnerability in the corporate messaging platform. The operation focused on entities linked to Kurdish military groups in Iraq.
The attack — along with the underlying vulnerability, CVE-2025-27920 — was identified by analysts at Microsoft Threat Intelligence. The flaw affects Output Messenger Server Manager and is classified as a Directory Traversal vulnerability. It allows authenticated attackers to access files beyond the permitted directory scope, including configuration files, user data, and even source code. Beyond information theft, the flaw enables the deployment of a malicious executable into the server’s startup directory.
The developer of Output Messenger, Srimax, patched the vulnerability in December 2024 with the release of version V2.0.63. However, the campaign specifically targeted those who had failed to apply the update. Following the initial compromise, the attackers deployed a backdoor named OMServerService.exe, which connected to a command-and-control server under their control and exfiltrated data about the victim.
It remains unclear how the attackers obtained authentication credentials in each case, but Microsoft suspects the use of credential-harvesting techniques such as DNS spoofing and typosquatting domains — methods previously employed by Marbled Dust in man-in-the-middle (MITM) operations to collect login data.
Once the server-side component of Output Messenger was compromised, the attackers gained unfettered access to all user communications. They could impersonate users, infiltrate internal systems, and exfiltrate sensitive information. In one documented instance, the Output Messenger client on an infected machine connected to an IP address linked to Marbled Dust immediately after the malware received a command to collect and archive files.
Marbled Dust — also known by the aliases Sea Turtle, SILICON, and UNC1326 — has long operated across the Middle East and Europe. Its targets have included telecommunications firms, IT organizations, and politically affiliated entities, including those in opposition to the Turkish government. The group has previously been tied to attacks against Dutch internet providers and Kurdish websites between 2021 and 2023.
According to Microsoft, the successful exploitation of a zero-day vulnerability points to a growing sophistication in Marbled Dust’s technical capabilities and likely signals a shift in the group’s priorities — toward more urgent or wide-reaching objectives. Furthermore, the targeting of Output Messenger may indicate that corporate communications infrastructure is increasingly viewed as a strategic entry point for cyberespionage.


