An unusual social engineering attack was recently discovered on the website of iClicker, a widely used educational platform serving millions of students and instructors across the United States. From April 12 to April 16, 2025, the iClicker homepage hosted a malicious CAPTCHA designed to trick users into executing a PowerShell script disguised as an identity verification process.
Owned by the publishing house Macmillan, iClicker offers digital teaching tools such as attendance tracking, live polling, and audience engagement analytics. It is employed by over 5,000 instructors and more than 7 million students, including those at the University of Michigan, University of Florida, and several leading California institutions.
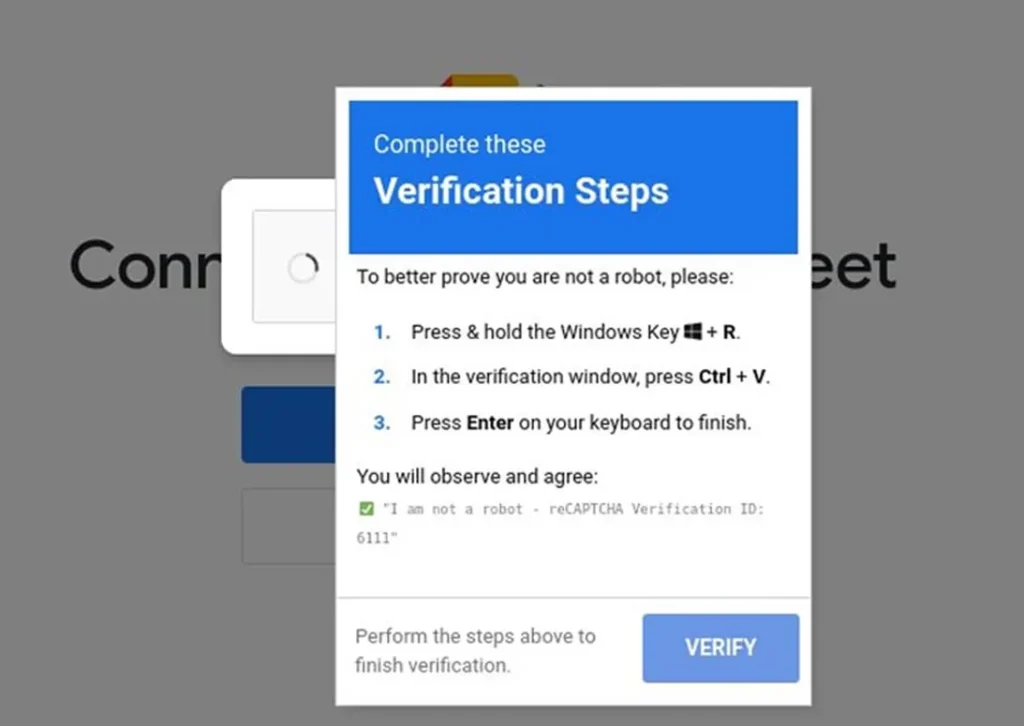
As detailed by the Safe Computing team at the University of Michigan, visitors to the homepage were prompted to click a “I’m not a robot” button. Upon doing so, a PowerShell script was automatically copied to the system clipboard—a method known as a ClickFix attack. The user was then instructed to open the “Run” dialog (Win + R), paste the script, and press Enter to allegedly complete a verification step.
In reality, this sequence triggered the download of obfuscated PowerShell code that connected to an external server and fetched a second-stage payload tailored to the specific user. If the target was a genuine user—such as a student or educator—the downloaded content was a fully functional piece of malware granting complete system access. In contrast, if the request originated from a sandbox environment or analyst machine, a benign file was delivered—typically a legitimate Microsoft Visual C++ Redistributable installer.
Although the precise nature of the malware remains unconfirmed, its behavior is consistent with that of an infostealer—a form of spyware engineered to harvest passwords, cookies, credit card data, cryptocurrency wallets, and sensitive documents (such as files named seed.txt, wallet.txt, and similar). The stolen data would then be exfiltrated to an attacker-controlled server, where it could be used for further attacks on university networks or sold on dark web marketplaces.
While the malicious code has since been removed from the website, the aftermath of the incident remains concerning. In an official statement, iClicker representatives assured users that no personal data or iClicker applications were compromised during the attack. Nevertheless, users who accessed the website during the affected window and followed the CAPTCHA instructions are strongly urged to perform a full antivirus scan, change their iClicker password, and update all credentials stored on their device.
Only those who visited iClicker[.]com from a desktop system and interacted with the fake CAPTCHA were impacted. The iClicker mobile application was not affected and remains safe for continued use.


