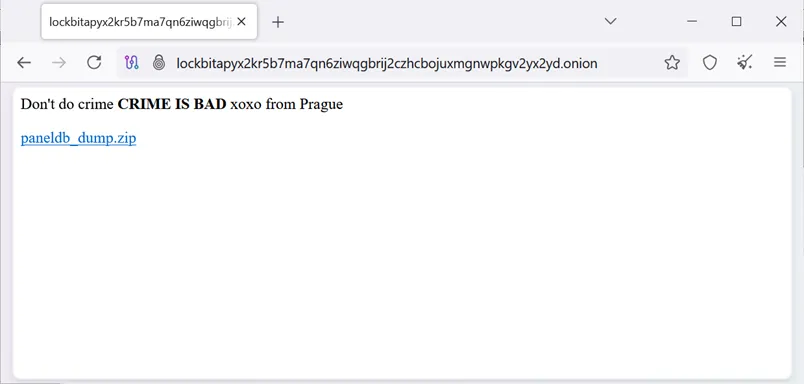
The LockBit ransomware syndicate has found itself at the center of a dramatic incident after its darknet infrastructure was subjected to a sweeping cyberattack. Unidentified assailants defaced all of the gang’s administrative panels, replacing the interface with a taunting message—”Don’t do crime. CRIME IS BAD xoxo from Prague”—along with a link to download an archive containing a dump of the group’s MySQL database.
The file, titled paneldb_dump.zip, contains an SQL dump from LockBit’s admin interface. Comprising twenty tables, several of which are of high value in understanding the group’s internal operations, the archive was first brought to public attention by a cybercriminal using the alias Rey, while a more detailed analysis was conducted by BleepingComputer.
Among the most revealing tables is btc_addresses, listing 59,975 unique Bitcoin addresses linked to LockBit’s financial operations. The builds table details specific malware samples generated by affiliates for carrying out attacks, with entries including public encryption keys and, in some cases, the names of targeted companies. Although no private keys were leaked, the data is more than sufficient to trace the structure and intent behind the group’s campaigns.
The builds_configurations table exposes the technical parameters used to create ransomware payloads—such as which ESXi servers to avoid and which file types to encrypt.
Particularly notable is the chats table, which logs 4,442 messages exchanged between LockBit operators and their victims from December 19, 2024, to April 29, 2025. This constitutes a near-complete record of negotiations, providing insight into ransom demands, threats, and coercion tactics.
The users table lists 75 registered users—including administrators and affiliates—with access to the control panel. According to cybersecurity expert Michael Gillespie, all passwords were stored in plaintext. Some, such as “Weekendlover69,” “MovingBricks69420,” and “Lockbitproud231,” provoked both amusement and alarm within the security community, highlighting the group’s lax internal security.
Judging by the dump’s timestamp and the most recent chat entry, the database was extracted no later than April 29, 2025. LockBit’s operator, known as LockBitSupp, confirmed the breach in a Tox conversation with Rey, acknowledging the compromise but claiming that private keys and other mission-critical data remained secure.
While the exact method of intrusion has not been conclusively identified, the server hosting the admin panel was running PHP version 8.1.2, which is known to be vulnerable to CVE-2024-4577—a flaw enabling remote code execution. The circumstantial evidence suggests this vulnerability may have served as the point of entry for the attackers.
Additional intrigue surrounds the defacement message itself, which closely resembles one used in a similar attack against the Everest group’s darknet infrastructure. The repeated phrasing hints at either the same perpetrators or the adoption of similar tactics.
LockBit previously endured a massive international takedown dubbed Operation Cronos in 2024, which led to the seizure of 34 servers hosting leak sites, mirrors, stolen data repositories, cryptocurrency wallets, and the confiscation of approximately 1,000 decryption keys. The affiliate control panel was also completely disabled. Despite efforts to rebound, this new breach delivers a devastating blow to the gang’s already fractured reputation.
Though it remains premature to declare the end of LockBit’s operations, a breach of this magnitude could erode affiliate trust and severely hamper the group’s ability to coordinate future campaigns. Similar public leaks have dismantled groups like Conti, Black Basta, and Everest—reminding observers that the resilience of ransomware syndicates may be more fragile than it appears.


