The phishing platform CoGUI, purpose-built for large-scale cyberattacks, has managed to dispatch over 580 million emails within the first four months of 2025. Its objective: the theft of login credentials, passwords, and payment information. While Japan bore the brunt of the campaign, other nations—including the United States, Canada, Australia, and New Zealand—were also targeted.
At the height of its activity in January, CoGUI orchestrated 170 distinct campaigns, distributing 172 million emails. These messages were cleverly disguised as notifications from well-known brands such as Amazon, Apple, PayPal, and Rakuten, as well as from tax authorities and financial institutions.
The attacks typically began with alarmist subject lines designed to provoke immediate action. Within the email was a link directing recipients to a phishing website—though the site would only open if the user’s device met a set of specific criteria: IP-based geolocation, browser language, operating system, screen resolution, and device type. If the parameters didn’t match, the target was redirected to a legitimate website, thereby minimizing suspicion.
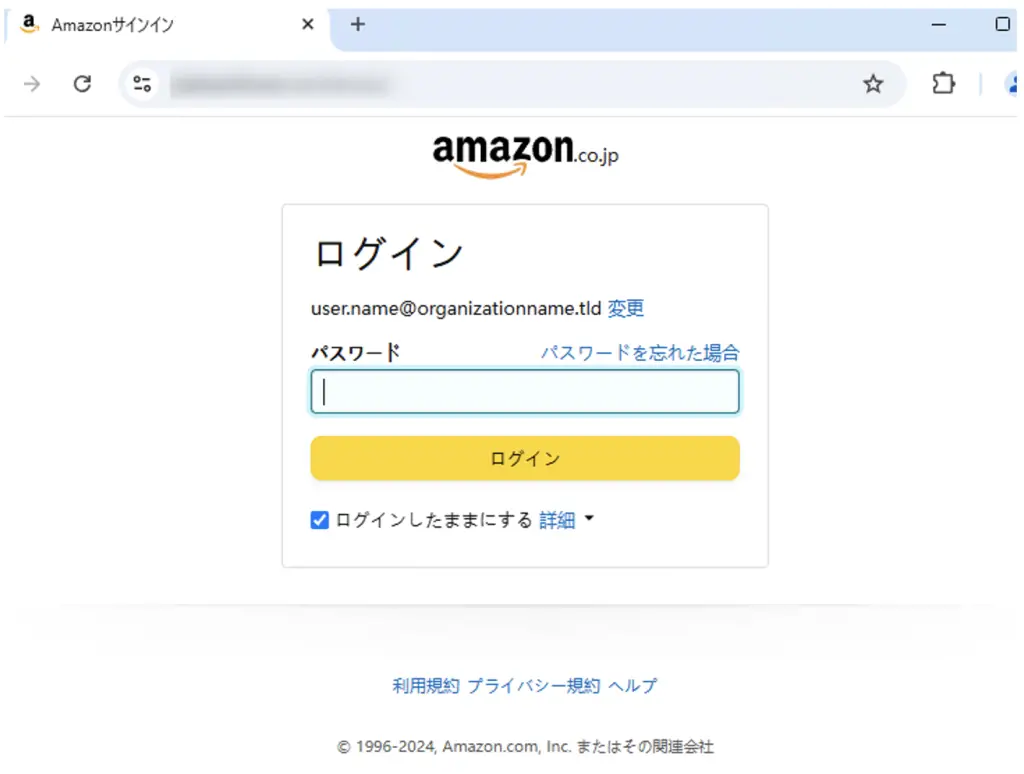
If the conditions were met, the victim was delivered to a counterfeit login page virtually indistinguishable from the authentic site. Once credentials were entered, they were immediately transmitted to the attackers. Among the templates identified was a remarkably convincing replica of Amazon’s login page.
According to cybersecurity firm Proofpoint, CoGUI has emerged as the most prolific phishing platform identified to date. Though it first surfaced in October 2024, the true extent of its operations only became apparent in December, when analysts began closely tracking its email campaigns. Initially believed to be linked to Darcula—a separate phishing toolkit associated with actors based in China—further technical analysis revealed that CoGUI operates independently, although both platforms are utilized by overlapping Chinese threat groups.
Beyond email-based attacks, CoGUI was also implicated in smishing campaigns across the U.S., in which fraudulent text messages about unpaid road tolls were used to harvest personal data. This particular attack vector was later absorbed by the Darcula platform.
Experts believe that CoGUI is not operated by a single group, but rather functions as a service-for-hire, accessible to a range of threat actors. Although its current focus remains on Japan, the platform is readily adaptable and could be deployed against targets in any region at any time.
To defend against such tactics, one principle remains paramount: never click on links embedded in unsolicited emails, no matter how legitimate they may appear. Instead, navigate to the intended site manually using a verified, official URL. If an email demands urgent action, that alone is often the clearest indication of a phishing attempt.


