A hacker has breached the servers of Israeli firm TeleMessage, a company specializing in modified versions of popular messaging apps, including Signal, WhatsApp, Telegram, and WeChat. These applications were marketed as secure archiving tools for government bodies and large corporations. According to media reports, the attack resulted in the theft of message fragments, internal login credentials for administrative panels, and personal data belonging to users—among them officials from U.S. agencies and employees of major financial institutions.
The vulnerability proved critical: despite TeleMessage’s assurances of preserving end-to-end encryption, the modified applications in fact rerouted all incoming and outgoing communications to a client-side server, bypassing the core security model. It was this very server—hosted in Amazon AWS’s Northern Virginia infrastructure—that became the hacker’s target. The attacker claimed the breach took no more than twenty minutes and described the process as “surprisingly easy.”
Among the compromised data were messages from group chats, including one named “Upstanding Citizens Brigade,” which circulated political content related to interviews with Donald Trump. Other intercepted conversations appeared linked to the cryptocurrency firm Galaxy Digital, discussing legislative efforts—potentially regarding cryptocurrency regulation—with mentions of U.S. senators and the bill’s prospects in Congress.
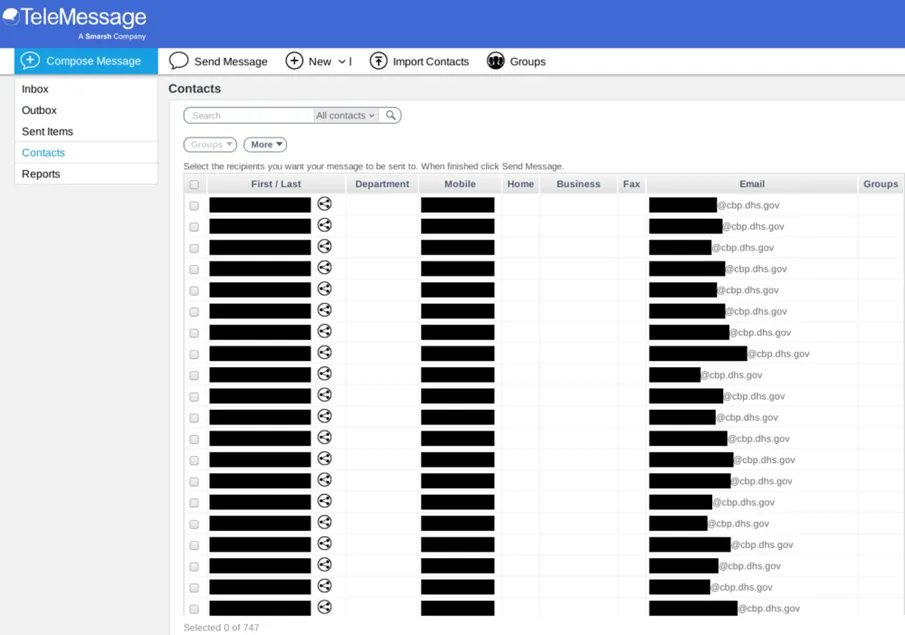
A screenshot shared by the hacker (via 404 Media) revealed contact details of officials from U.S. Customs and Border Protection (CBP). Several phone numbers were confirmed as authentic by 404 Media journalists through direct calls. One administrative panel within TeleMessage displayed as many as 747 CBP-related entries, highlighting the scale of the data compromise. Authentic numbers belonging to employees at Coinbase and other financial firms were also verified.
Another screenshot indicated that TeleMessage was in use by the Washington D.C. Police Department’s intelligence division. Scotiabank was also mentioned, suggesting that it—like other financial institutions—may have used the product to comply with business communication archiving requirements.
Despite the gravity of the breach, leaked materials suggest that TeleMessage continued to claim—via YouTube videos—that its applications maintained the encryption and security standards of the original Signal. In reality, the company’s solution transformed a secure messenger into a tool that mirrored all data to a remote server, effectively nullifying its protections in the presence of any vulnerability. A Signal representative had previously stated unequivocally that the organization cannot vouch for the security of modified versions of its app.
The story came to light after a Reuters photographer inadvertently captured U.S. National Security Council member Mike Waltz using a TeleMessage-modified version of Signal during a meeting with Trump. Upon zooming in, journalists identified interface elements distinctive to the altered app. In the past, Waltz had also unintentionally leaked information by adding a journalist from The Atlantic to a chat discussing military operations.
Following a wave of media reports about the breach and ensuing data leaks, the TeleMessage website was scrubbed entirely—product pages and even download links vanished. Representatives from the parent company Smarsh, as well as from CBP, Coinbase, Scotiabank, and other involved parties, declined to issue immediate comments.
The attack did not encompass the entirety of TeleMessage’s stored data—the hacker gained access to snapshots captured by the system for debugging purposes. Yet even these fragments contained live, unencrypted messages, shattering any illusion of security. The hacker explained that his motivation was pure curiosity and chose not to notify TeleMessage directly, fearing the company would attempt to conceal the vulnerability.
This incident serves as a stark reminder of the perils of integrating archiving functions into messengers originally engineered for absolute confidentiality. Instead of robust protection, government entities and corporations ended up with a fragile system where a breach doesn’t require compromising a user’s phone—merely tapping into the archiving point suffices, as the hacker has so clearly demonstrated.


