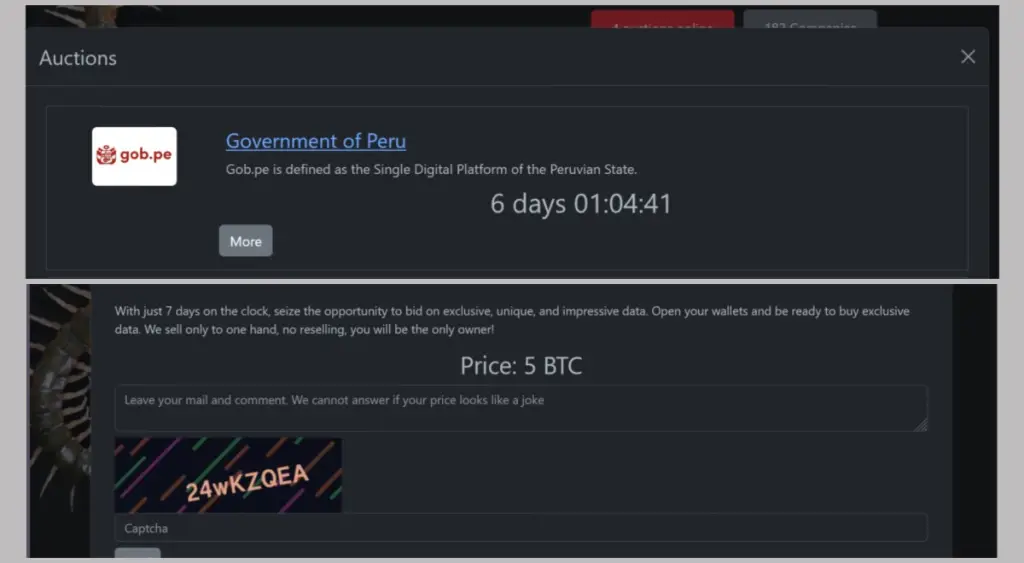
Government systems in Peru have been paralyzed following a large-scale cyberattack claimed by the hacker collective Rhysida, which has demanded a ransom for the stolen data.
The attackers published details of the breach targeting the South American nation’s government portal on the dark web late Thursday evening. Authorities have been given an ultimatum: six days to respond, with a deadline set for May 9. The exact ransom amount has not been disclosed.
Curiously, officials have chosen denial as their strategy. In statements to the public, government representatives claimed there was no cyberattack, attributing the disruption to technical issues on the website.
Independent experts, however, confirm that Peru’s main government portal, Gob.pe, remains inaccessible. In an attempt to ease public concern, the authorities issued a press release citing scheduled maintenance. Intelligence firm Venerix, reporting on the situation, notes that only 22% of Rhysida’s claims regarding the breach have been independently verified thus far.
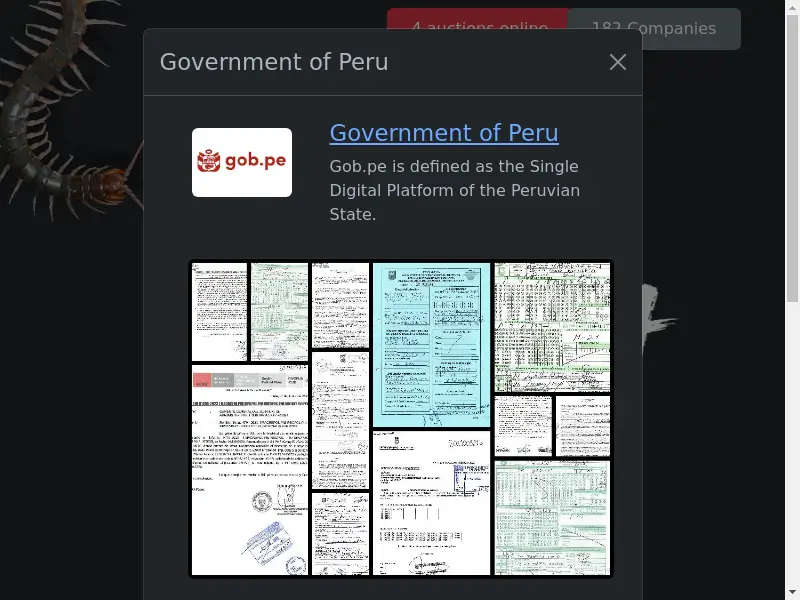
The potential scope of the leak is significant. Gob.pe hosts data of national importance for a country of over 33 million people, including passport records, tax information, national health insurance databases, police files, and employment documentation.
Rhysida, known for its double-extortion tactics, has listed the allegedly stolen data for sale at 5 bitcoins (approximately $488,000 USD). The total volume of exfiltrated data remains undisclosed. In their signature style, the hackers urge prospective buyers not to miss this “unique opportunity,” promising exclusive, non-resellable access to the dataset.
Samples of the purportedly stolen files have been posted on Rhysida’s website. While most are unreadable, among the samples is an administrative document bearing an official seal, dated June 2023.
This incident is not the first government-targeted cyberattack in Latin America. In November of last year, Mexico fell victim to the RansomHub group, which crippled the national portal and claimed to have stolen over 300 GB of data.
Since its emergence in May 2023, Rhysida has carried out attacks on 182 organizations. According to the U.S. Department of Defense, the group operates opportunistically, targeting a broad range of sectors including education, healthcare, manufacturing, and local government.
Earlier this year, the hackers demanded $1 million from the administration of Montréal-Nord in Quebec. Last summer, they successfully breached the city of Columbus, Ohio, disrupting municipal operations for several weeks.
At the end of 2024, Rhysida orchestrated a brazen attack on Seattle-Tacoma International Airport, paralyzing critical systems at one of the West Coast’s major transportation hubs. As a result, staff at Delta Airlines, Singapore Airlines, and Alaska Airlines were forced to issue boarding passes manually. The ransom demanded: 100 bitcoins.
In October of the same year, the group targeted Easterseals, a nonprofit serving individuals with disabilities, demanding over $1.3 million for the stolen data.
A study published by Trend Micro in February 2024 indicates that Rhysida typically gains initial access through phishing campaigns. In some cases, attackers impersonated cybersecurity experts offering to help organizations identify vulnerabilities. Once inside, they deployed Cobalt Strike to probe for weaknesses and executed their own ransomware tools.
Experts have also noted links between Rhysida and another hacker group, Vice Society, which employs similar techniques. It is believed the two groups collaborate and share ransom proceeds. Among Rhysida’s other high-profile attacks are breaches of The Washington Times, the British Library, the Ann & Robert H. Lurie Children’s Hospital of Chicago, and the Prospect Medical Group network.
In February of this year, researchers at South Korea’s Internet and Security Agency successfully cracked the gang’s encryption code. They subsequently released a free decryption tool, complete with detailed usage instructions.


