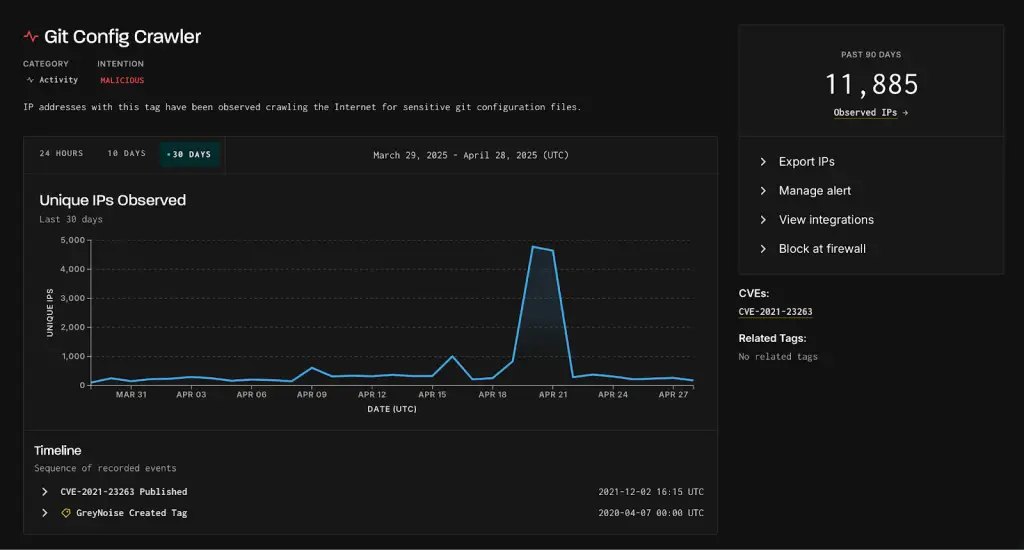
In recent days, cybersecurity experts have observed a disturbing surge in activity aimed at accessing configuration files of Git repositories. According to data from GreyNoise, a global threat intelligence platform, on April 20 and 21 alone, the number of unique IP addresses scanning for .git/config files exceeded 4,800 — the highest ever recorded and an unequivocal indication that malicious interest in vulnerable Git repositories is intensifying at an alarming pace.
While this does not stem from a newly discovered vulnerability, researchers warn that cybercriminals are exploiting well-known weaknesses — most notably CVE-2021-23263. This flaw arises from misconfigured web servers that inadvertently expose the .git directory to the public internet. If leveraged, an attacker could download the entire repository, including commit history, configuration files, and — most critically — embedded credentials.
GreyNoise reports that 95% of the IP addresses involved in attempts to access .git over the past 90 days are classified as malicious. The geographical spread of this activity spans nearly every region, though the highest concentration has been observed in Asia. Singapore, in particular, stands out both as a primary source and a principal target of these scanning operations. The United States ranks second, followed by Germany, the United Kingdom, and India.
Notably, many of the suspicious IPs are traced back to major cloud providers such as Cloudflare, Amazon, and DigitalOcean — suggesting that adversaries are leveraging scalable infrastructure to obfuscate their identities and amplify reconnaissance efforts.
GreyNoise notes that this marks the fourth wave of such scanning since September 2024, yet it has vastly outpaced previous ones in scale. Earlier peaks did not exceed 3,000 unique IPs, whereas this latest spike reached nearly one and a half times that figure in just two days.
Public exposure of the .git/config file is far more than a mere technical oversight. It can reveal the branching structure of development, internal repository links, authorship metadata, and even sensitive data inadvertently committed to version history. In 2024, a similar misconfiguration led to the exposure of 15,000 user accounts and the cloning of 10,000 private repositories.
Security professionals are urging immediate remediation measures. Foremost among these is ensuring that the .git directory is inaccessible via web servers. Administrators should block access to hidden files and directories at the configuration level, enable log monitoring for repeated access attempts to .git/config, and, upon signs of compromise, swiftly rotate all exposed credentials.
Organizations that utilize Git in their development workflows must regard these scanning activities as a direct threat to the security of their source code. The sooner these vulnerabilities are sealed, the greater the chance of averting severe consequences.


