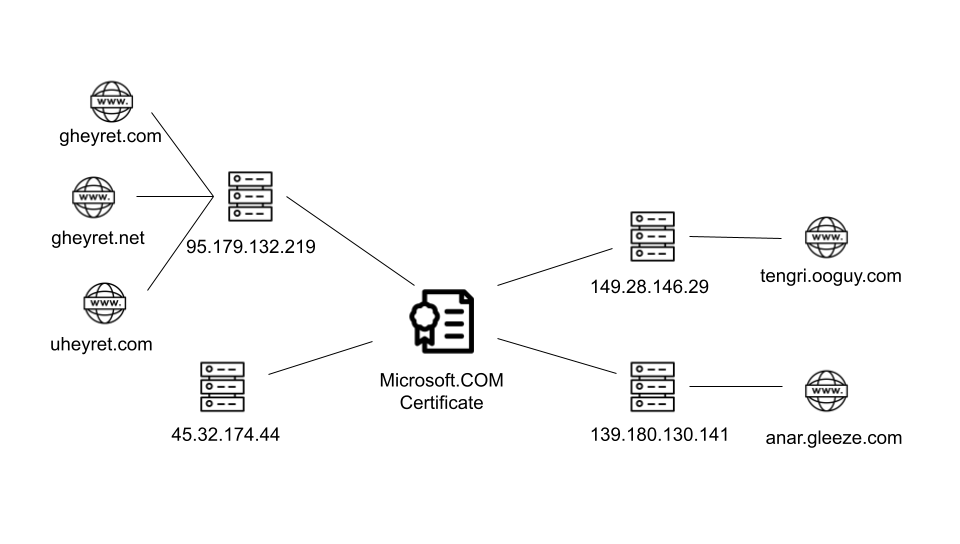
Diagram demonstrating the two distinct clusters of C2 infrastructure used in this campaign.
In March 2025, senior members of the World Uyghur Congress (WUC), living in exile, fell victim to a targeted phishing campaign aimed at installing spyware for remote surveillance. The attackers deployed a specially modified version of an open-source Uyghur-language text editor, developed by a figure trusted within the community. Although the malware itself was technically unsophisticated, the delivery method was meticulously tailored to the target audience, with technical traces indicating that preparations for the operation had begun as early as May 2024.
This approach has become characteristic of attacks linked to Chinese state interests: in the past, threat actors have repeatedly weaponized programs and websites intended to support repressed cultures, turning them into instruments of digital persecution against the very communities they were meant to aid. This incident underscores the ongoing threats of digital repression against the Uyghur diaspora, where technology is deployed to surveil, intimidate, and silence dissent beyond China’s borders.
In mid-March 2025, WUC members received alerts from Google warning of state-sponsored attacks. Upon receiving these notifications, they sought assistance from journalists and experts at Citizen Lab. The ensuing investigation uncovered a phishing campaign disguised as communications from a partner organization. Emails contained links to Google Drive, leading to an archive with an infected version of the UyghurEditPP editor. Once launched, the program harvested system information, transmitted it to a remote server, and had the capability to download additional malicious payloads.
Digital persecution of Uyghurs abroad has long been a component of China’s broader strategy. The repression in Xinjiang—also known as East Turkestan—has been marked by surveillance, forced movement control, internment, and suppression of cultural and religious expression. These methods have now extended overseas, encompassing physical threats, coercion of families via video calls, and pressure to renounce human rights advocacy.
Particular attention is paid to activists spotlighting human rights abuses, such as members of the WUC. This organization, uniting over 30 groups across 18 countries, plays an active role in international human rights initiatives and faces continuous repression by Chinese authorities. Beijing has designated the WUC as a terrorist organization and persistently seeks to discredit it through arrests, surveillance, and cyberattacks.
The investigation revealed notable details regarding the attack structure. The malware communicated with domains tengri[.]ooguy[.]com and anar[.]gleeze[.]com, both of which reference culturally significant terms in Central Asian tradition. The compromised servers used self-signed certificates bearing a forged Microsoft name, further highlighting the illegitimacy of the infrastructure.
Earlier phases of the campaign involved registering domains that closely mimicked the legitimate UyghurEditPP developer’s name, suggesting long-term strategic planning. In later stages, attackers shifted to different domain names while preserving thematic consistency.
Another infected instance of UyghurEditPP was found on VirusTotal, featuring slight variations in configuration, indicating that the attack may have unfolded in several phases or that different groups within the Uyghur diaspora were targeted with distinct campaigns.
The techniques employed align with well-documented Chinese state tactics: exploiting cultural support tools, registering domains through Dynu Systems, and hosting infrastructure within Choopa LLC’s autonomous system, previously implicated in similar operations.
Such attacks inflict damage far beyond the immediate breach. They undermine trust in initiatives dedicated to cultural preservation, fostering fear and self-censorship among affected communities. Digital repression exerts a profound psychological toll on activists and deepens their vulnerability.
To mitigate risks, it is critical to download applications only from official websites, verify digital signatures or trusted publisher statuses, and scrutinize domain names and browser warnings for potential threats.
Although the technical sophistication of the attack was modest, the level of social engineering demonstrated acute awareness of the target community’s nuances. This incident serves as a stark reminder that even simple methods, when skillfully executed, can be profoundly dangerous.
Addressing digital persecution demands not only the vigilance of human rights organizations but also proactive engagement from governments hosting vulnerable diaspora members. Notification systems alerting users to targeted attacks—such as those employed by Google—should become a standard practice among all digital service providers. Combating digital repression requires coordinated efforts across both public and private sectors.


